3.8. VT AIR Amazon AWS¶
VT AIR AWS brings you all VT AIR feature to Amazon’s Cloud.
VT AIR AWS AMI can be run in any region where EC2 offers service on various sizes of instance. VT AIR for AWS is available in the AWS Marketplace.
Two different versions are currently available:
Intel Based VT AIR Version
Graviton Based VT AIR Version
The graviton version will only run on the AWS Graviton EC2 instances.
All features are available in the AWS Version and you can use VT AIR as a firewall to protect your EC2 instances or as a VPN server to connect via IPSec, OpenVPN or WireGuard.
In order to configure your AWS environment to utilize VT AIR as a firewall in front of other VMs, a couple of configuration steps have to be done.
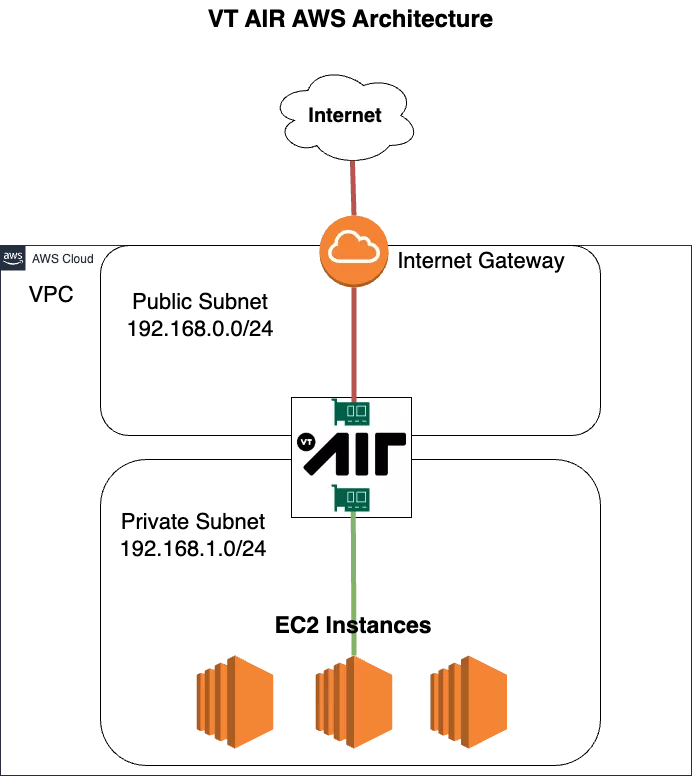
VPC configuration
New VPC
Public Subnet
Private Subnet
Public Routing Table
Internet Gateway for default route
Private Routing Table
Default route pointing to VT AIR LAN interface
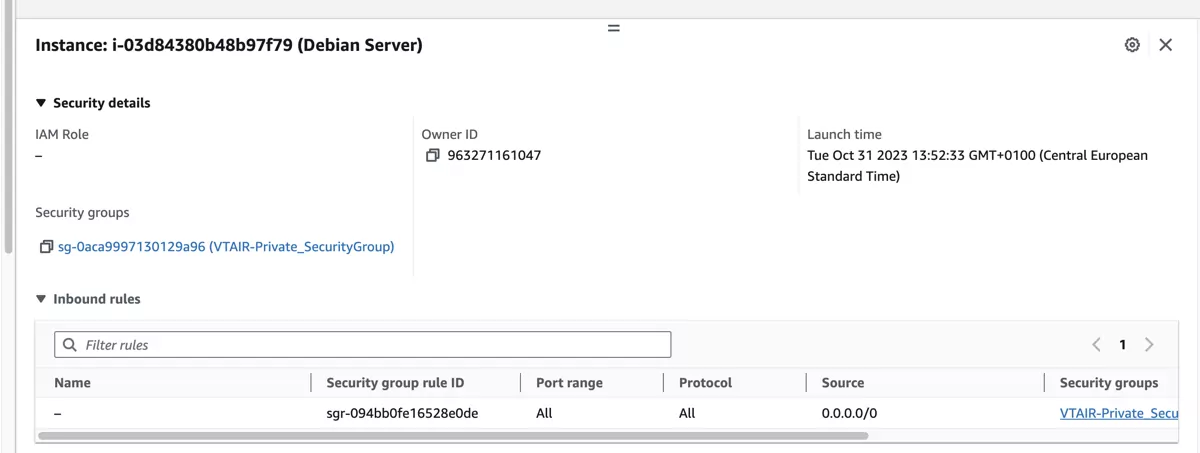
Public Security Group
Private Security Group
EC2 VT AIR Appliance
Public Network Interface (WAN)
In the Public Subnet
Public Security Group
Private Network Interface (LAN)
In the Private Subnet
Private Security Group
Disable Source and Destination Check
Allocate Elastic IP
Connect to the Public Network Interface (WAN)
VT AIR configuration
Enable and set LAN Interface
Create DNAT Rules and VPN Configuration
EC2 VMs
Add to the Private Network Subnet
Set Private Security Group
3.8.1. Default Login¶
Default login data for the WebGUI are user admin and the password is the instance id of the VM. For example i-0198da08d22664a39. You can find the instance id in the ec2 console.
For SSH or the console the default user is admin and your ssh key from the instance launch is automatically added to the user. You can get root access by using sudo.
3.8.2. VPC Configuration¶
Login to your AWS Account and change to the VPC configuration page.
We have created videos to show the entire configurations.
3.8.2.1. New VPC¶
We will create a new VPC for the VT AIR setup. If you already have a VPC or two subnets configured, you can skip these steps.
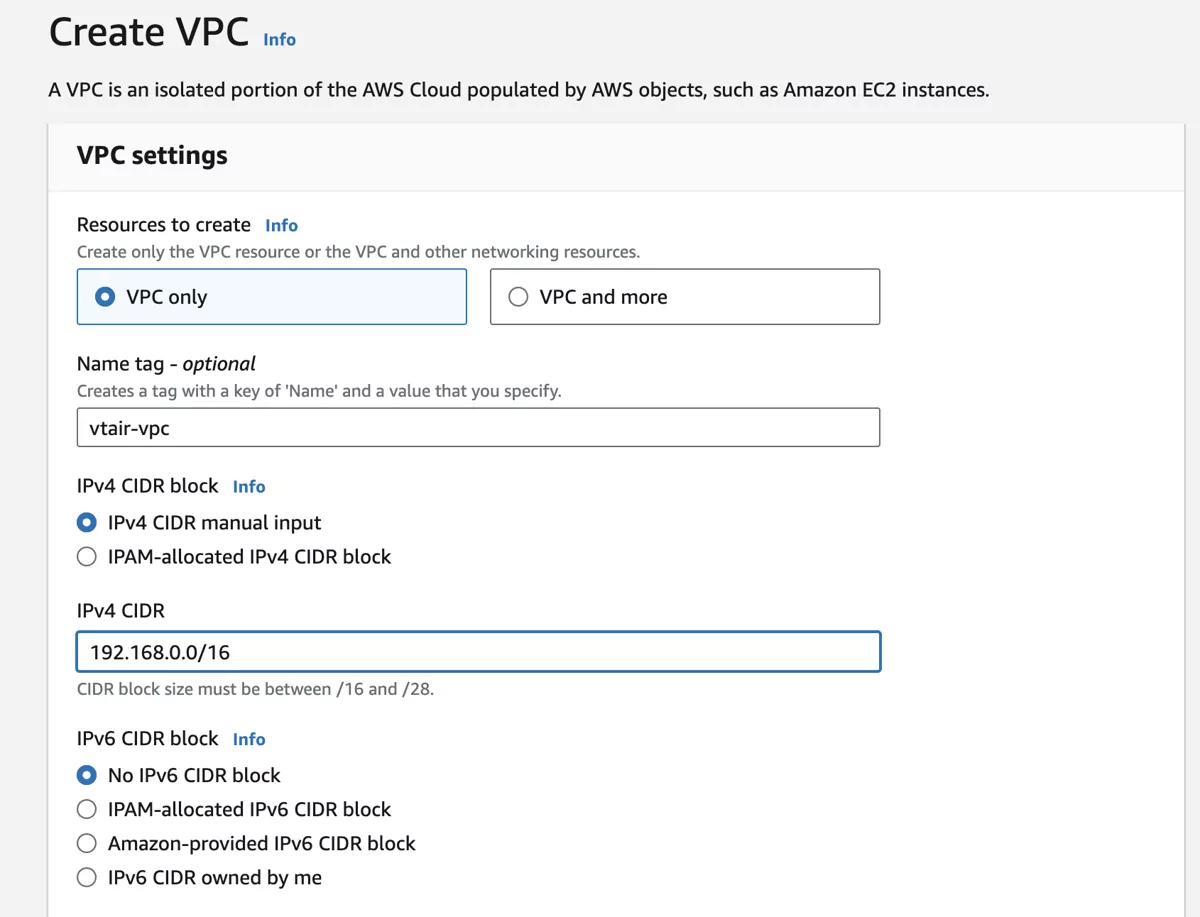
Go to Your VPCs and click on Create VPC.
Choose VPC only give the VPC a name, in our case we choose VTAIR-VPC and select a network. The network has to be large enough to hold both the Public and Private Subnet. We are going to use 192.168.0.0/16.
3.8.2.2. Public Subnet¶
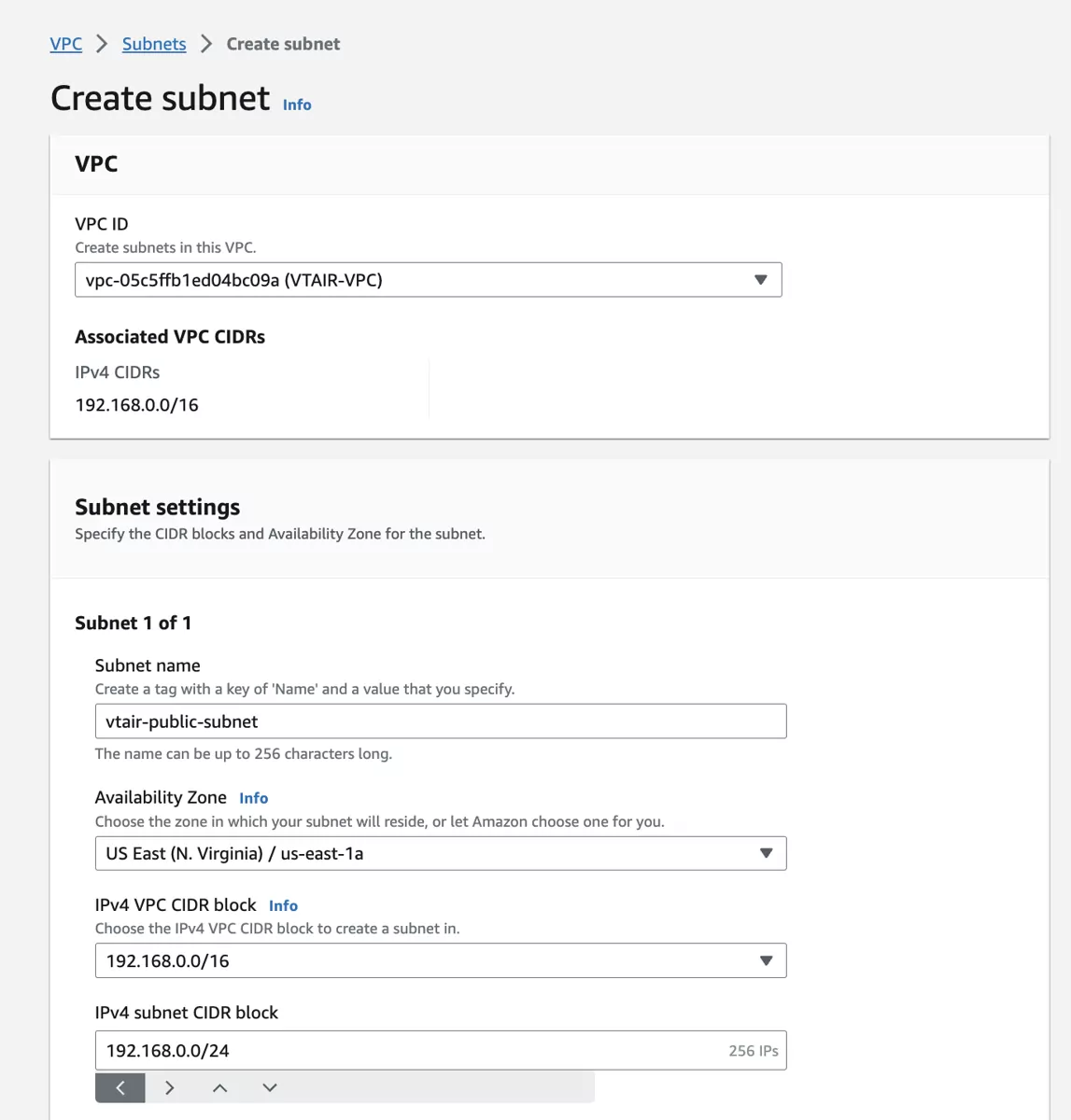
Navigate to Subnets and click on Create subnet. Select the newly created VPC VTAIR VPC and give the subnet a name. We will use vtair-public-subnet and choose the first ip network 192.168.0.0/24.
Make sure to select the same availability zone for both subnets.
3.8.2.3. Private Subnet¶
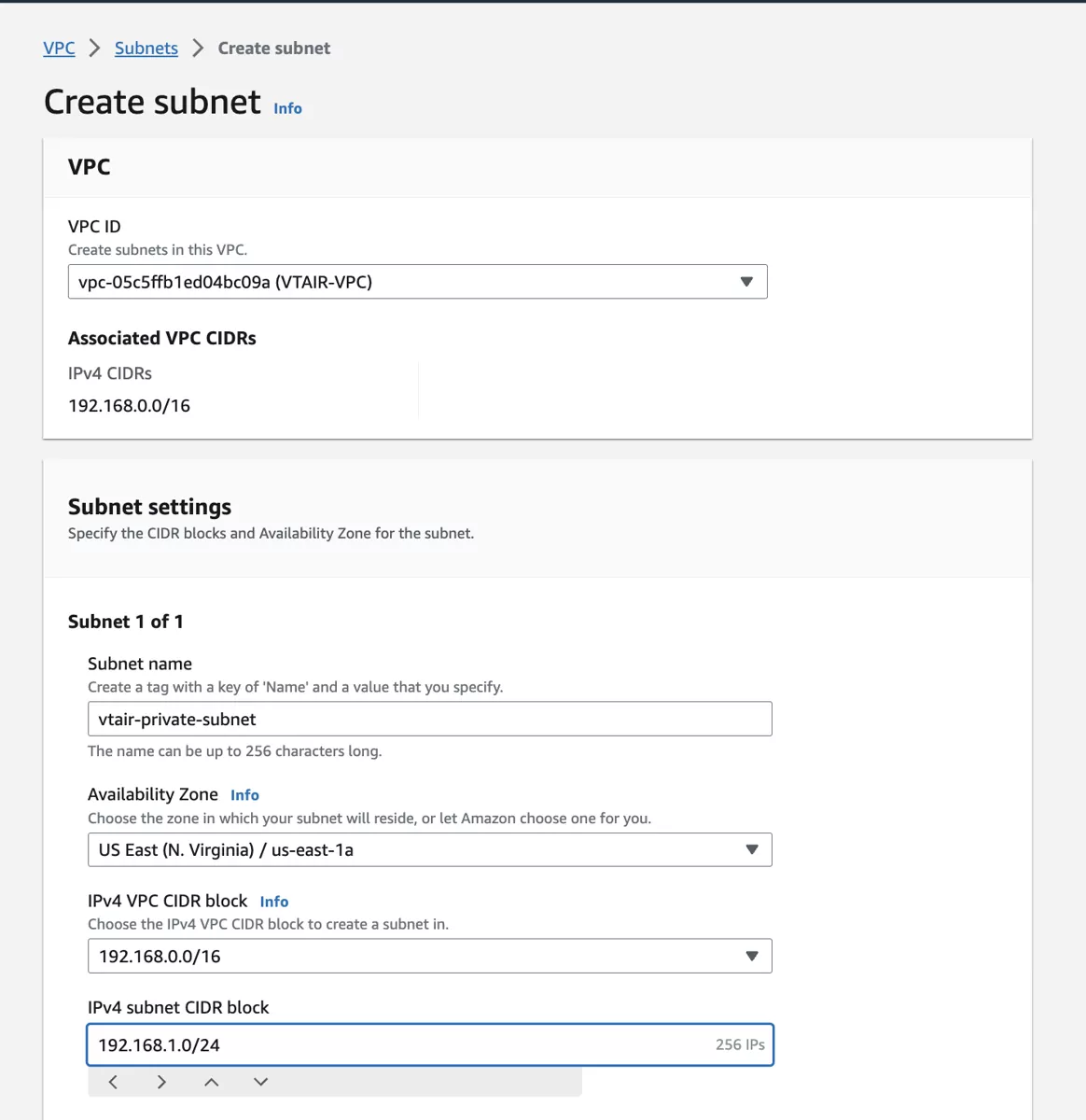
Navigate to Subnets and click on Create subnet. Select the newly created VPC VTAIR VPC and give the subnet a name. We will use vtair-private-subnet and choose the first ip network 192.168.1.0/24.
Make sure to select the same availability zone for both subnets.
3.8.2.4. Public Routing Table¶
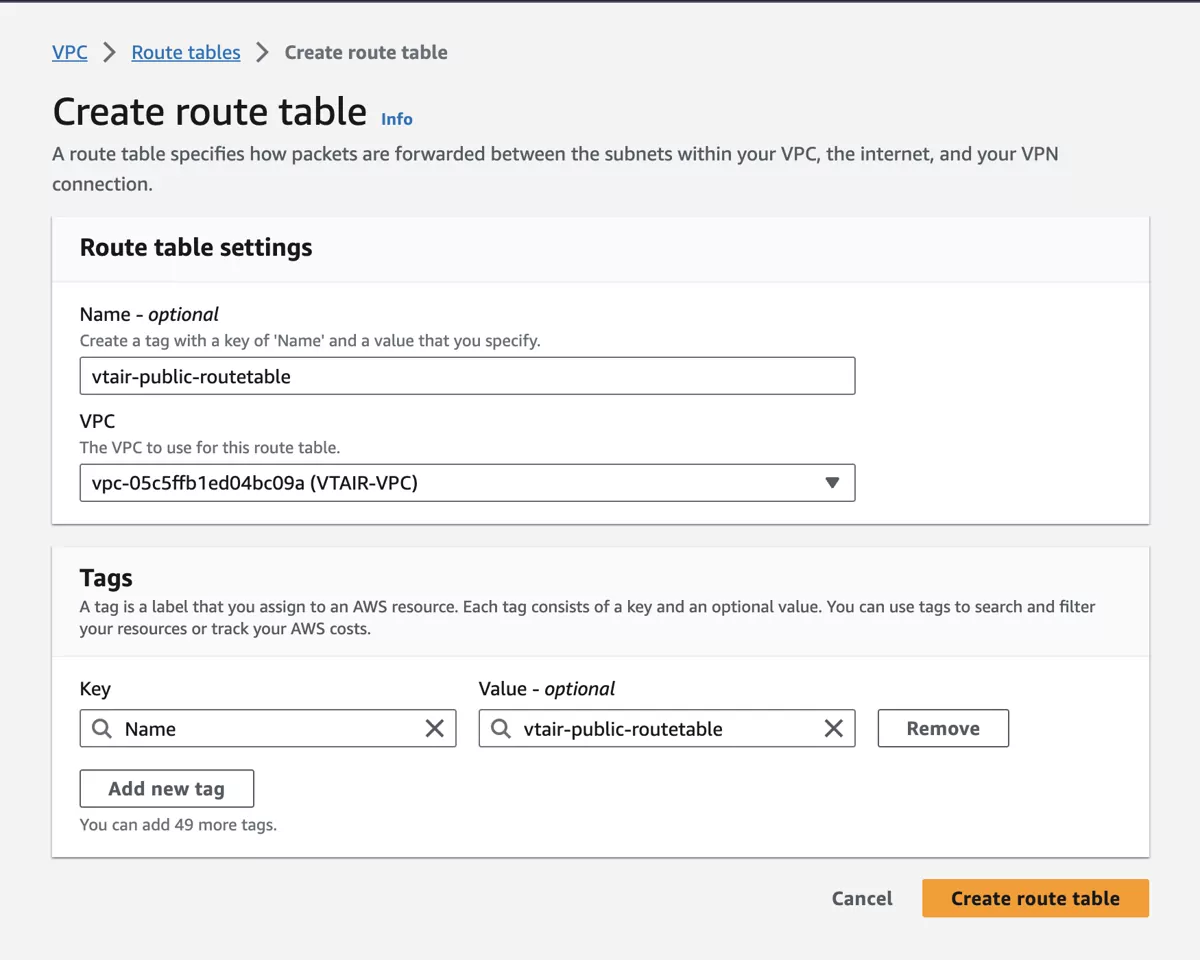
We will create a Public Routing Table that is used with the Public Subnet. It will contain an Internet Gateway that we connect to the default route of the Routing Table.
Navigate to Route Tables and click on Create route table. Select the newly created VPC VTAIR VPC and give the routing table a name. We will use vtair-public-routetable.
We need to connect the routing table to the Public Subnet.
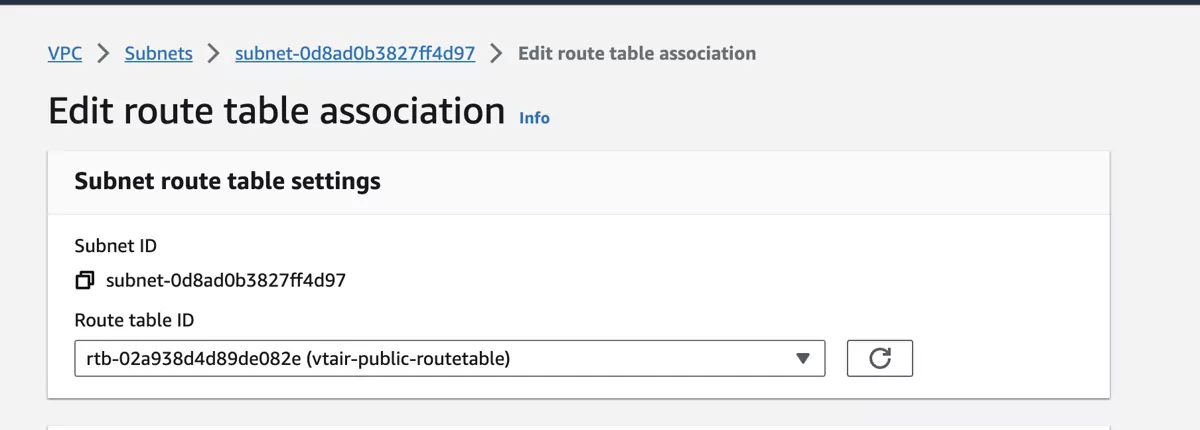
Navigate to Subnets and select the vtair-public-subnet. In the menu on the bottom select the Route Table tab and press Edit route table association.
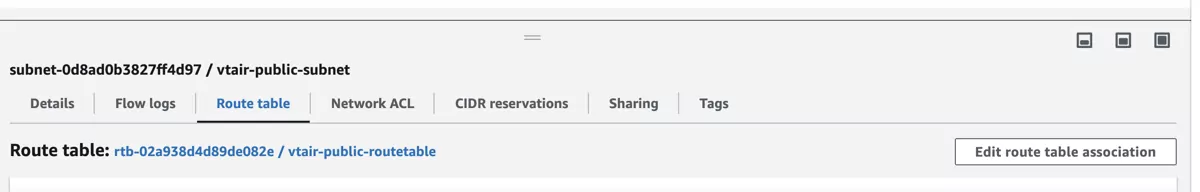
Select the vtair-public-routetable in the dropdown menu and save.
3.8.2.4.1. Internet Gateway¶
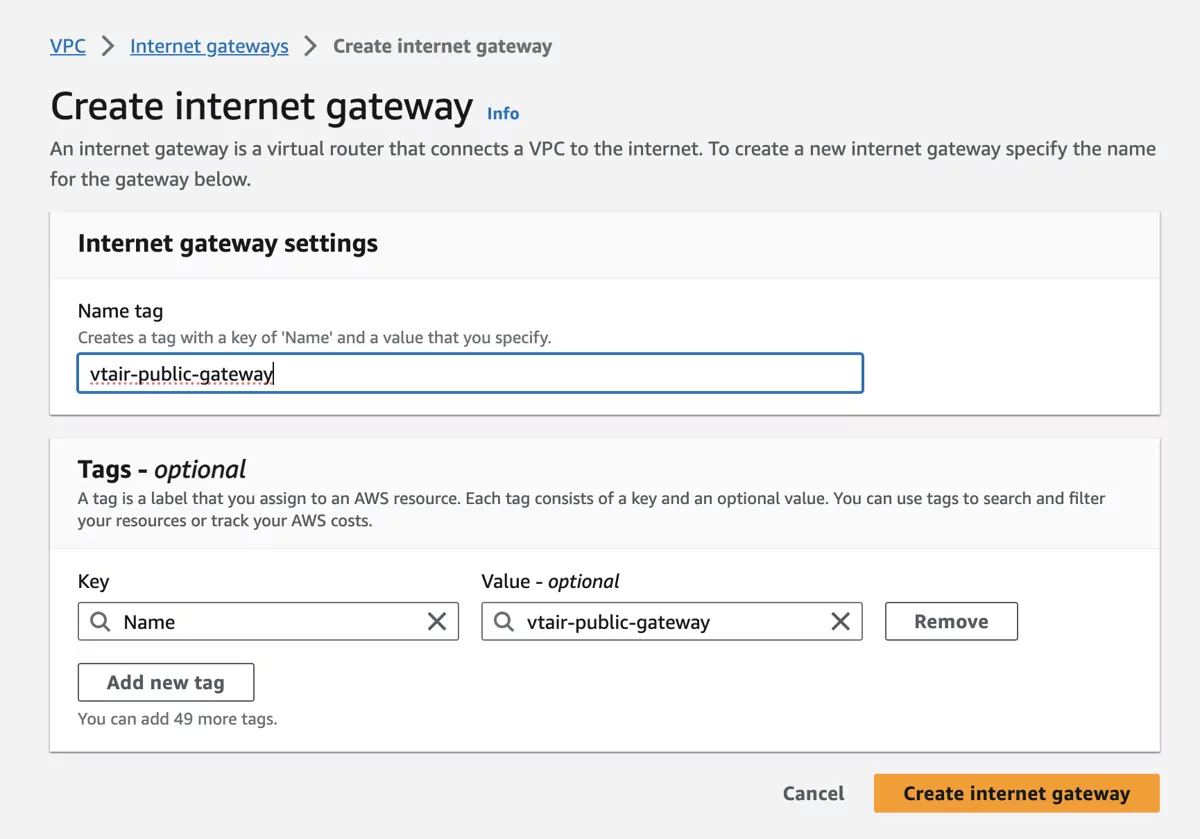
We need to create an Internet Gateway for the Public Routing Table as a default route. Navigate to Internet Gateways and click on Create internet gateway.
We will use the name vtair-public-gateway.
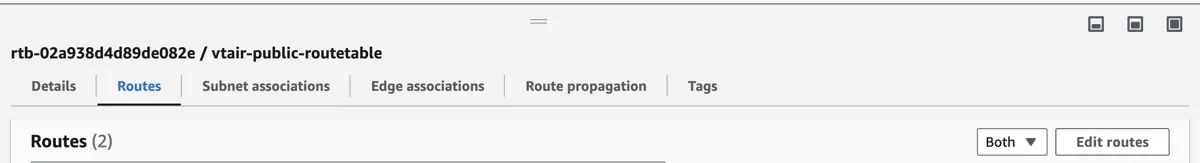
We now have to connect the Internet Gateway with the routing table. Navigate to Route Tables and click on the vtair-public-routetable. In the menu on the bottom select the Routes tab and press Edit routes.
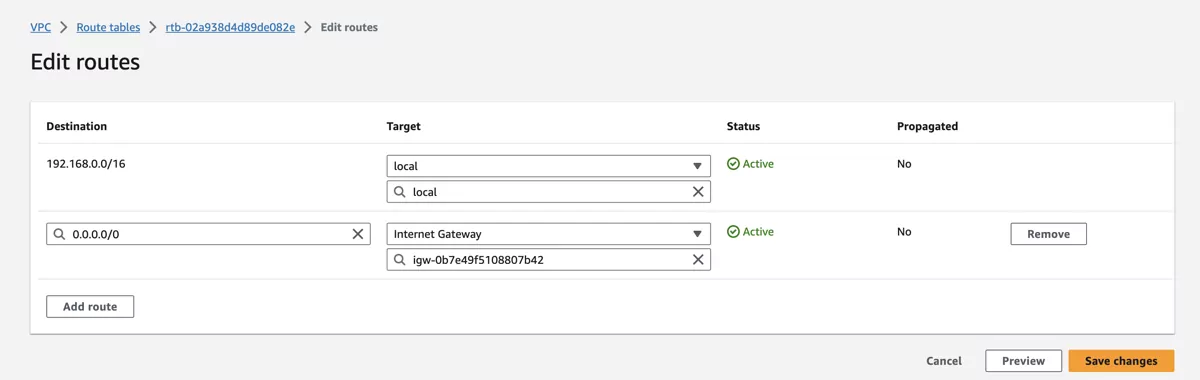
Create a new route with destination 0.0.0.0/0 and as target select Internet Gateway and select the newly created Gateway in the dropdown.
3.8.2.5. Private Routing Table¶
We will create a Private Routing Table that is used with the Private Subnet. It will contain the VT AIR LAN Interface that we connect to the default route of the Routing Table. This step needs to be done after the VT AIR EC2 VM is up and running.
Navigate to Route Tables and click on Create route table. Select the newly created VPC VTAIR VPC and give the routing table a name. We will use vtair-private-routetable.
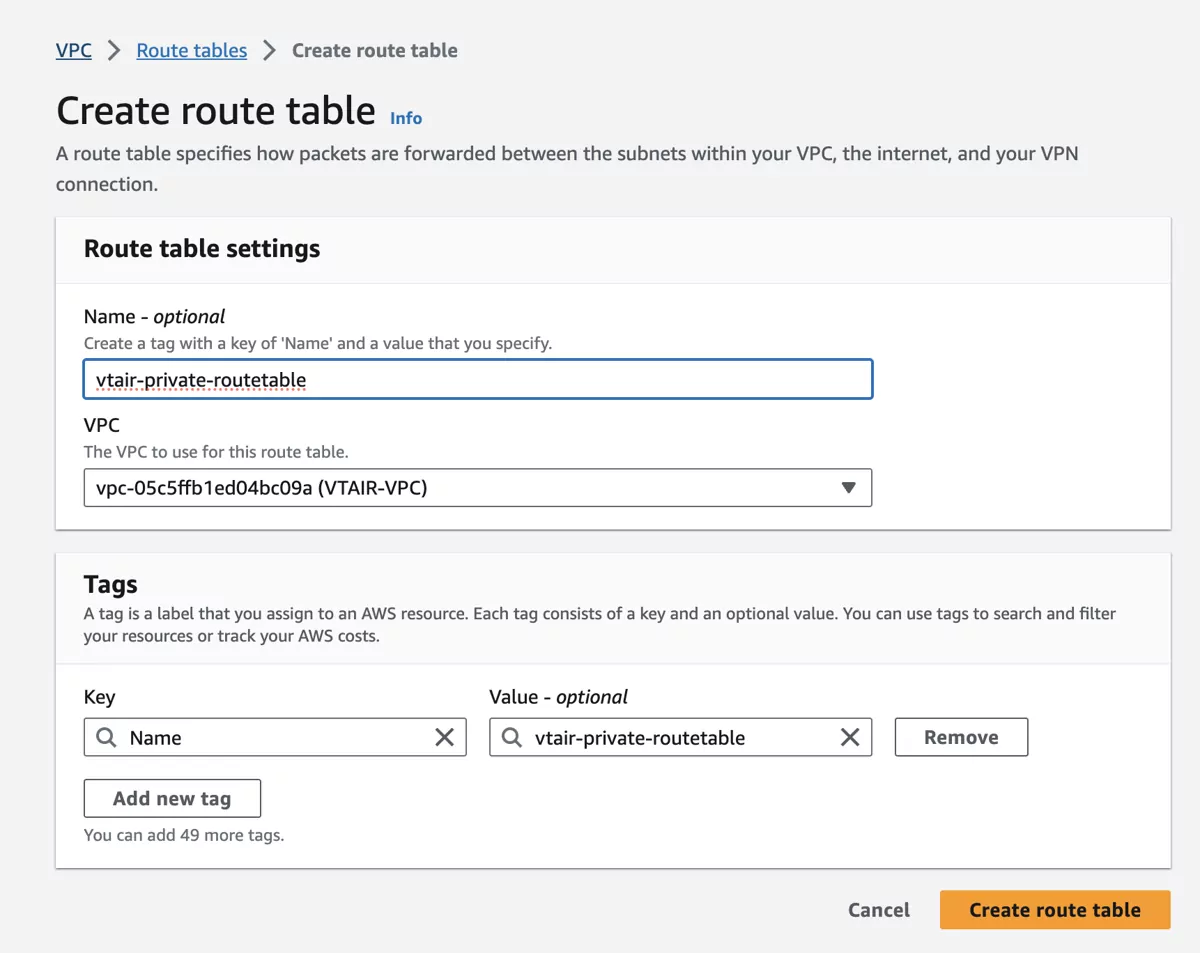
We need to connect the routing table to the Private Subnet.
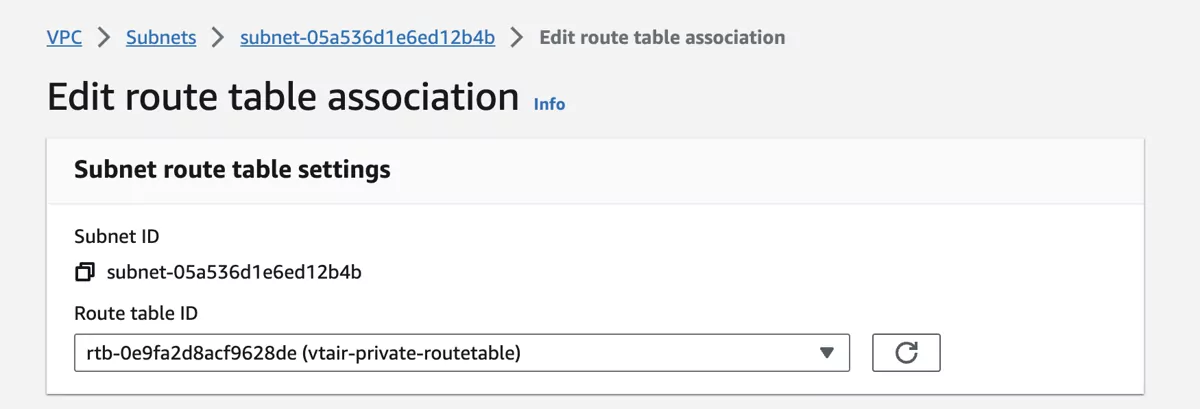
Navigate to Subnets and select the vtair-private-subnet. In the menu on the bottom select the Route Table tab and press Edit route table association.
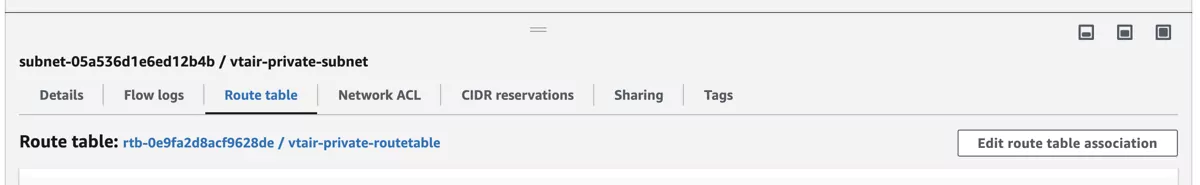
Select the vtair-private-routetable in the dropdown menu and save.
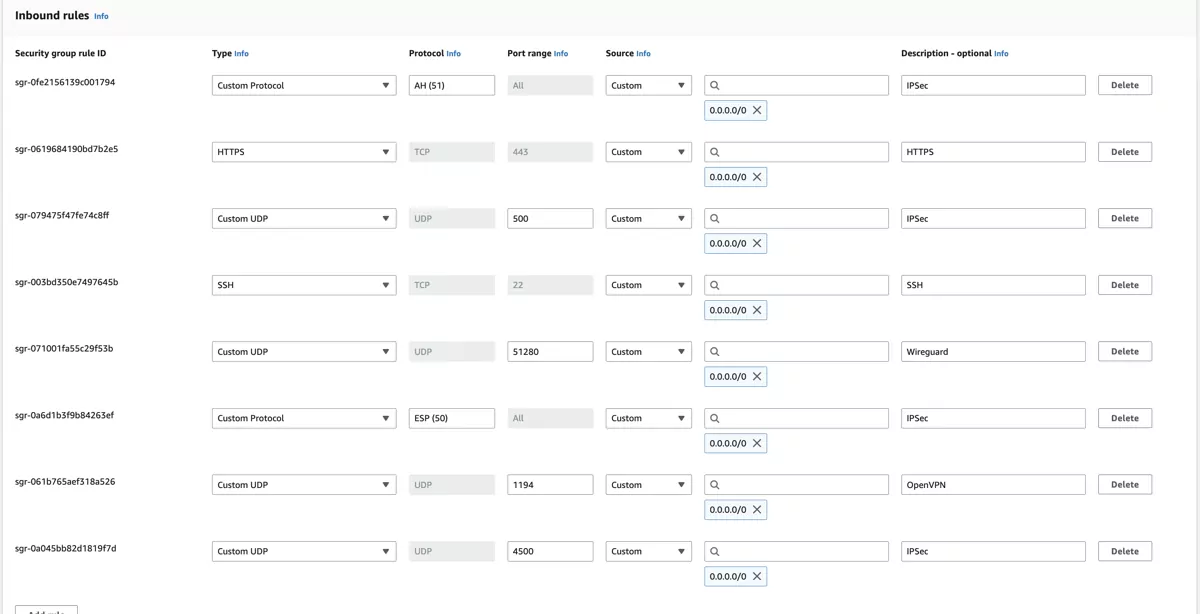
3.8.2.6. Public Security Group¶
We need to create a Public Security Group that will be associated with the VT AIR Public Network Interface. You can customize the group to your needs, we do recommend to add at least the following entries:
Port 22 (TCP)
Port 443 (TCP)
and depending on which VPN is used:
1194 (UDP) for OpenVPN
51280 (UDP) for Wireguard
500 and 4500 (UDP) for IPSec
ESP/AH for IPSec
Navigate to Security Groups and click on Create security group. Select the newly created VPC VTAIR VPC and give the security group a name and a description. We will use VTAIR-Public-SecurityGroup and VT AIR Public Access.
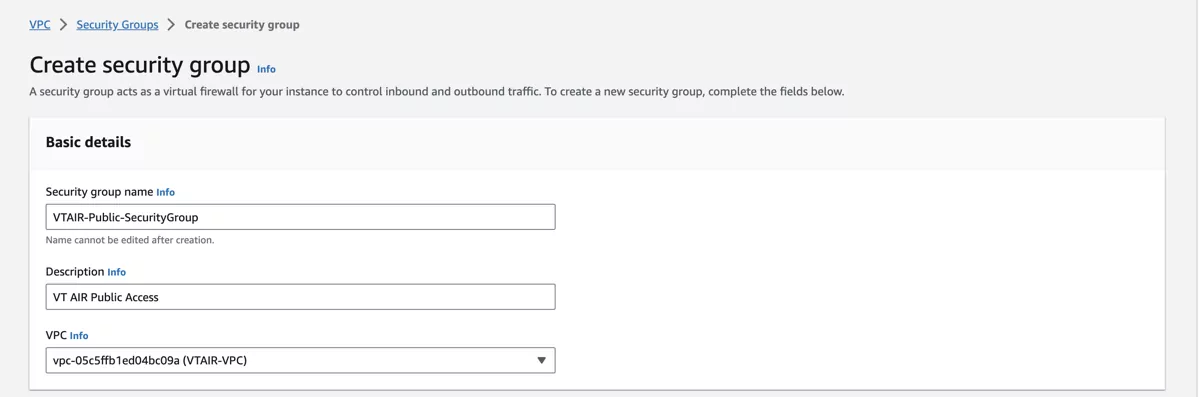
For the inbound traffic we created all rules above.
3.8.2.7. Private Security Group¶
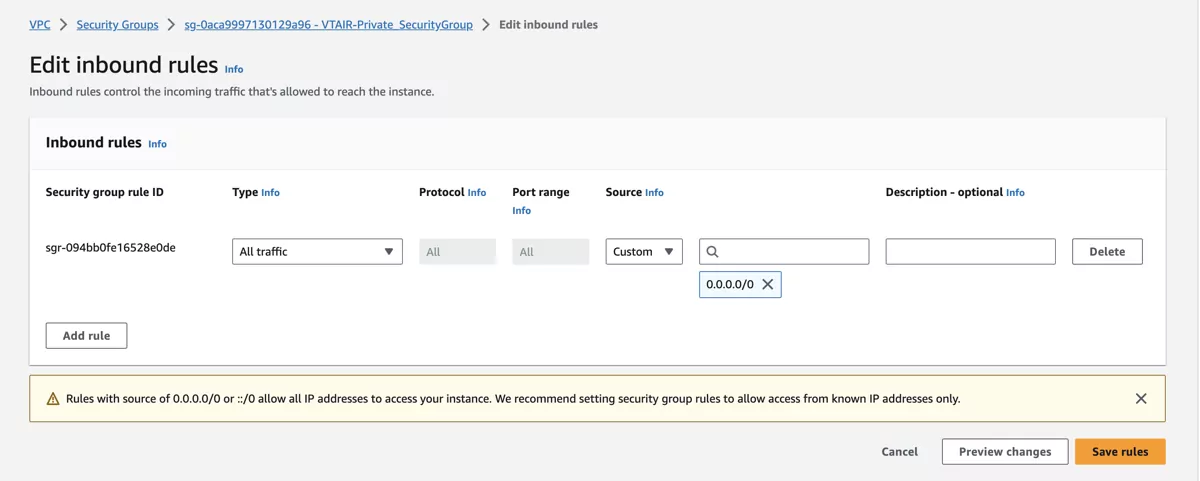
We need to create a Private Security Group that will be associated with the VT AIR Private Network Interface. We will allow all traffic on the private side as it is protected by the VT AIR Firewall.
Navigate to Security Groups and click on Create security group. Select the newly created VPC VTAIR VPC and give the security group a name and a description. We will use VTAIR-Private-SecurityGroup and VT AIR Private Access.
For the inbound traffic we created the allow all rule.
3.8.3. EC2 VT AIR Appliance¶
It is time to create and start the VT AIR Appliance.
We have created videos to show the entire configurations.
Navigate to EC2 and select Instances and press Launch instances.
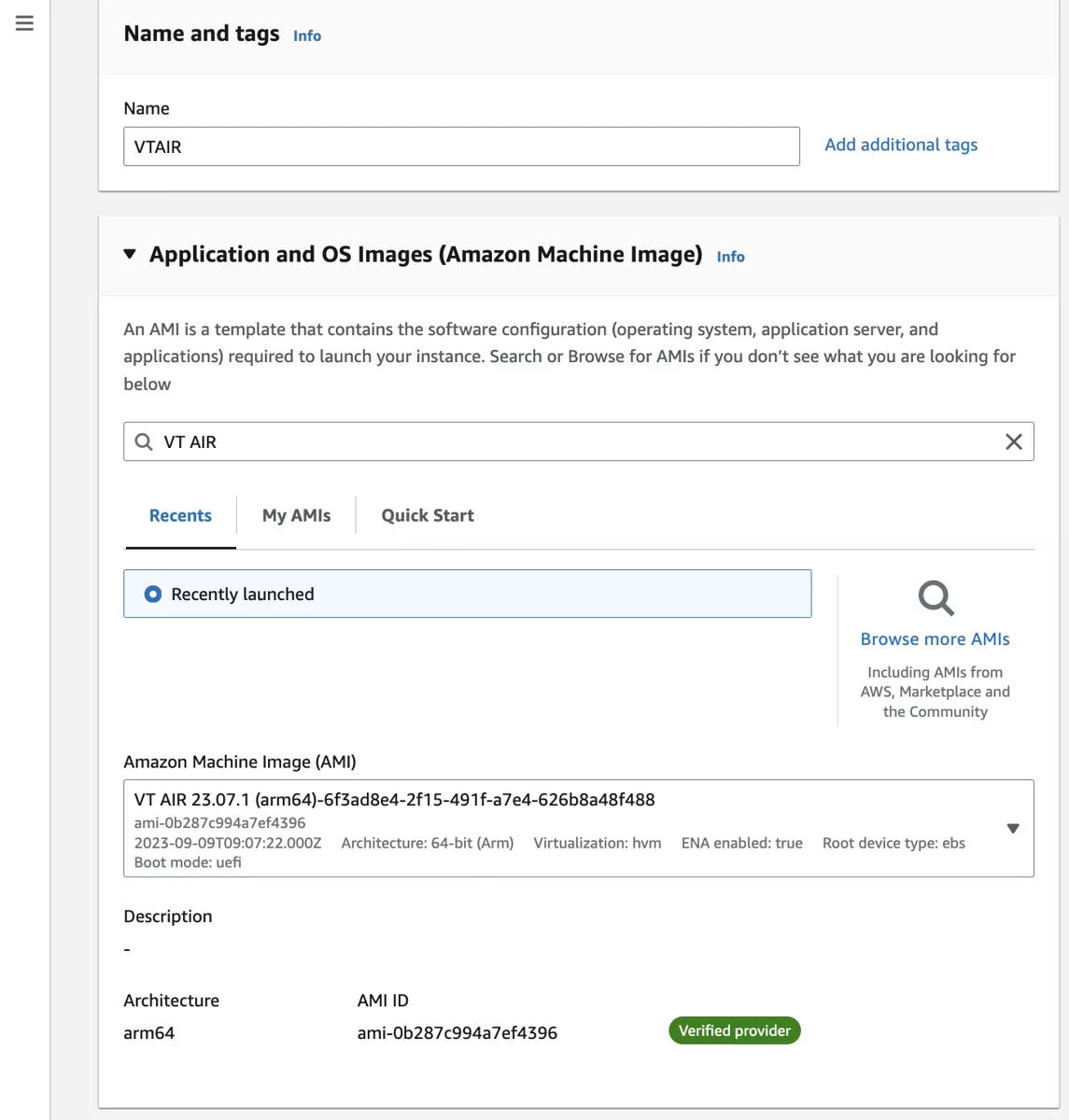
We will name the instance VTAIR. Search for VT AIR in the Amazon Machine Image.
Choose your preferred Instance type.
Select your instance type and a key pair for the default SSH connection.
The instance will also be available via the webgui.
3.8.3.1. Public Network Interface (WAN)¶
In the network settings choose the create VPC VT AIR VPC. Also choose the public network vtair-public-subnet. You need to disable the Auto-assign public IP option as it will not working with multiple network interfaces.
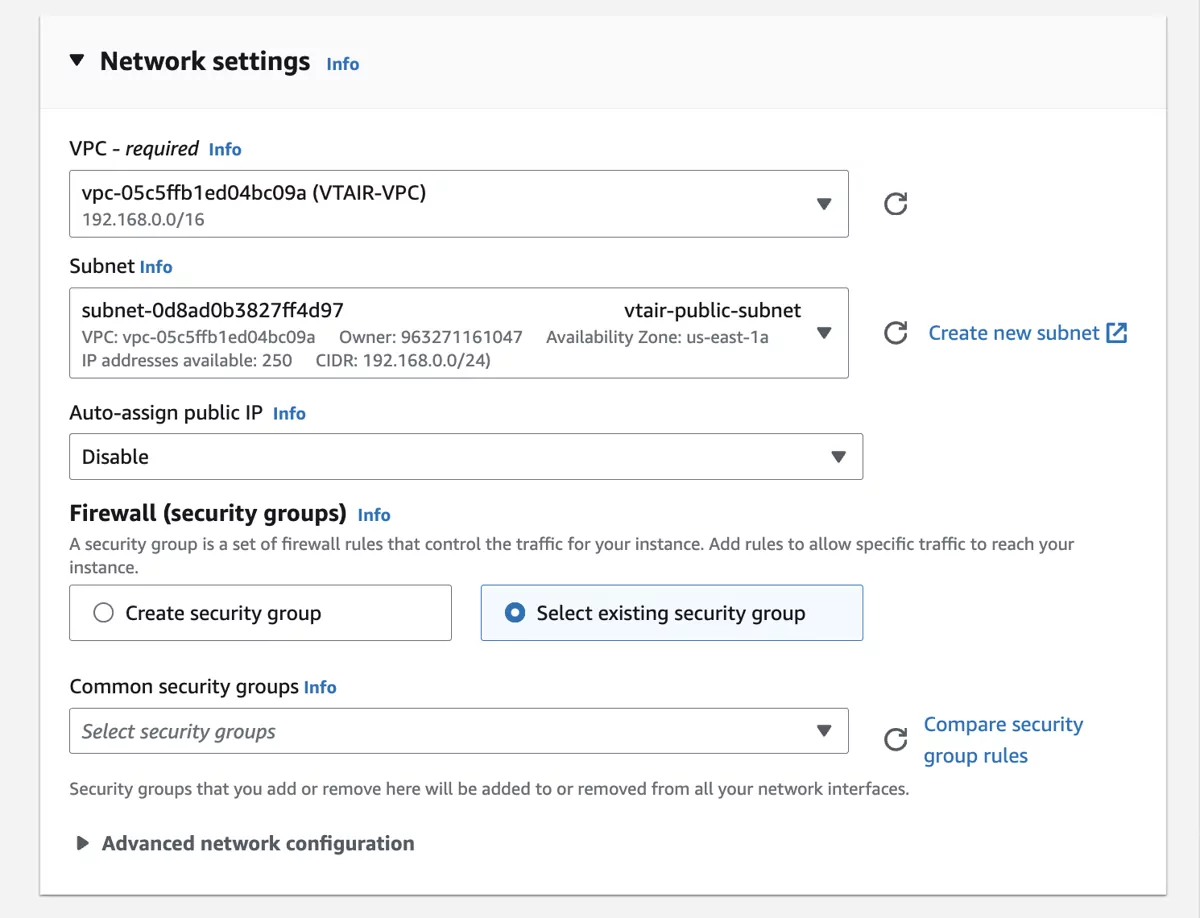
For the security group select Select existing security group
Click on Advanced network configuration
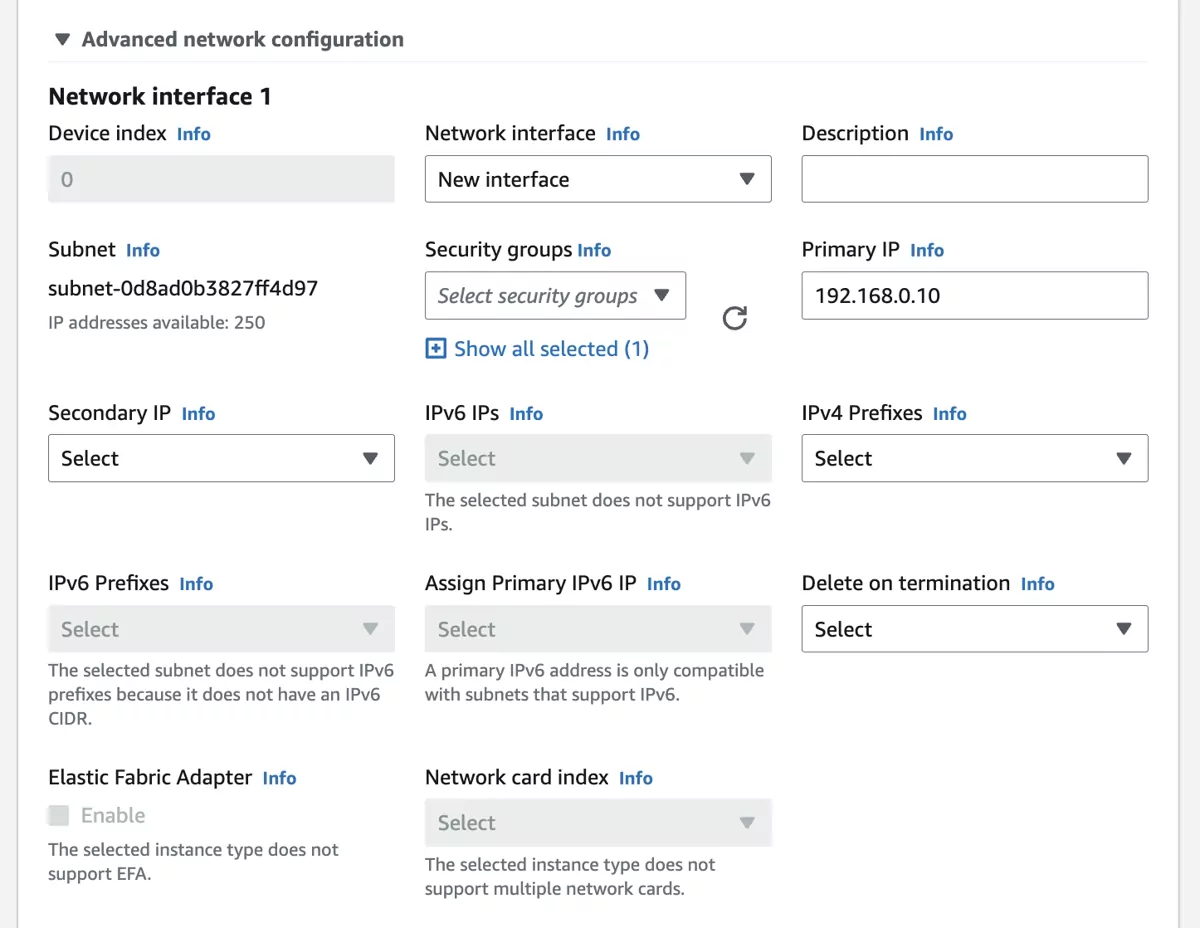
The Network Interface 1 will be our Public Network Interface (WAN). Select the Security Group VTAIR-Public-SecurityGroup for this interface. We also want to give a static IP to the interface, the first 4 or 5 IPs are in use by the subnet so we start at 10. The IP is assigned via DHCP. We set the IP to 192.168.0.10.
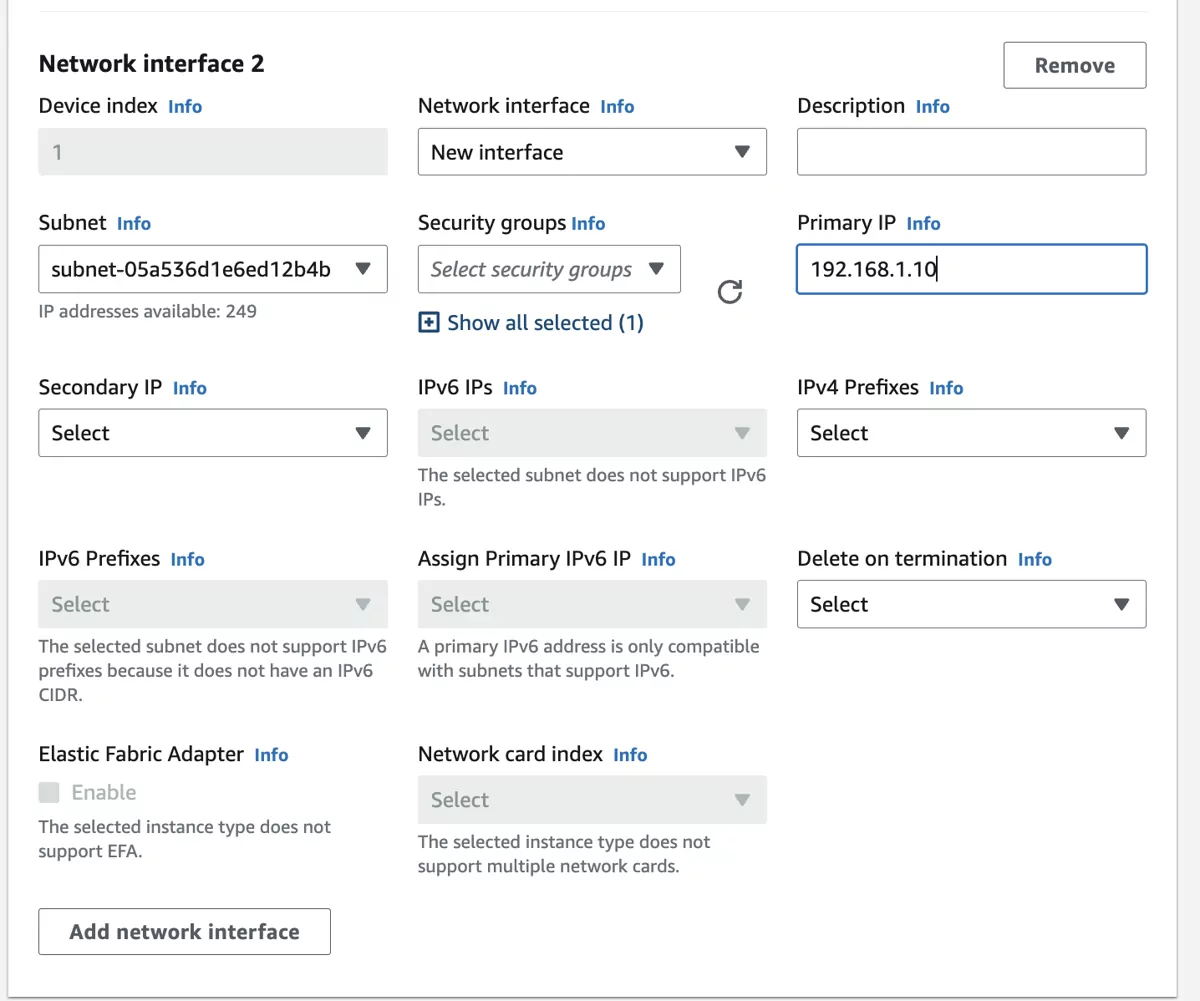
3.8.3.2. Private Network Interface (LAN)¶
Click on the Add network interface button to create a second interface for the LAN side. As subnet select vtair-private-subnet and also choose the security group VTAIR-Private-SecurityGroup
We also want to give a static IP to the interface, the first 4 or 5 IPs are in use by the subnet so we start at 10. The IP is assigned via DHCP. We set the IP to 192.168.1.10.
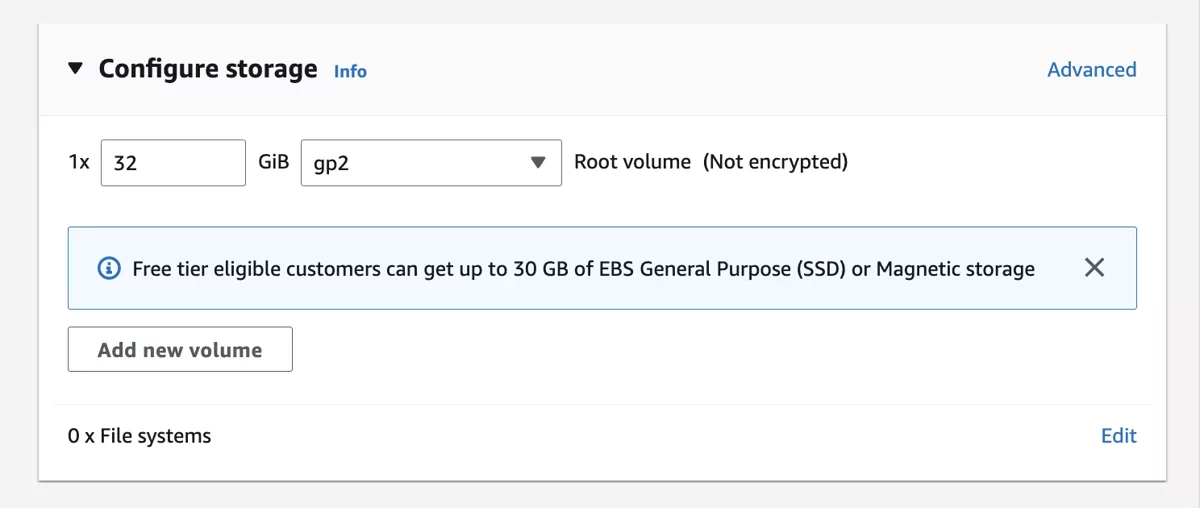
3.8.3.3. Storage¶
Make sure to select a large enough storage space. We recommend 30GB or more.
All settings are finished, you can create and run the instance.
3.8.3.4. Disable Source and Destination Check¶
In order to forward traffic, the option Disable Source and Destination Check has to be disabled. In EC2 -> Instances select the newly created VT AIR instance.
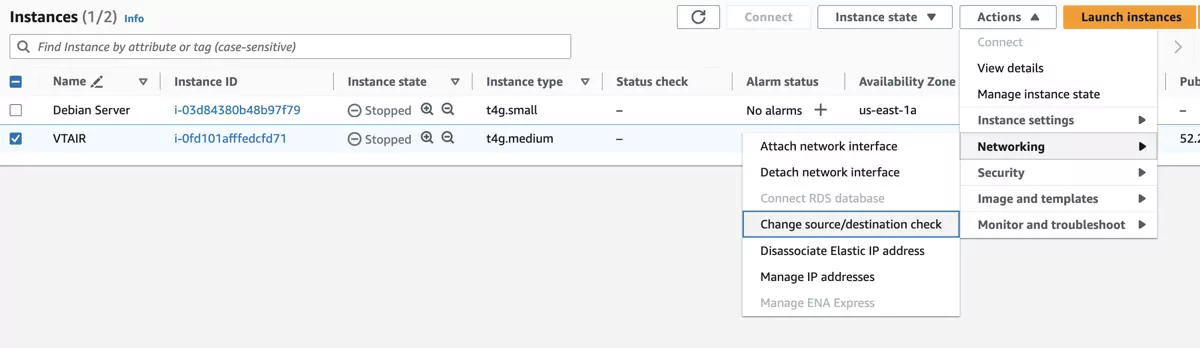
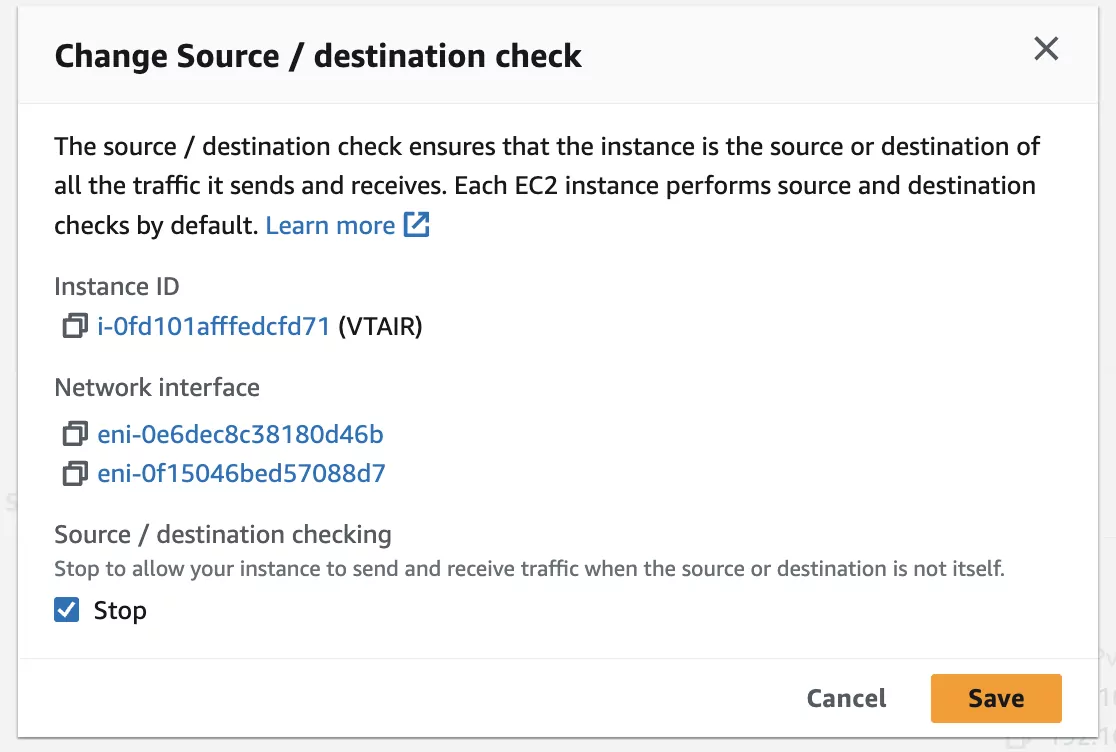
In the menu select Actions -> Networking -> Change source/destination check. A new popup will appear. Select the option Stop at the bottom and press Save
3.8.3.5. Allocate Elastic IP¶
For the VT AIR instance to be reachable via the internet, a new Elastic IP has to be created and attached to the Public Network Interface.
First go to EC2 -> Instances and write down the network interface names. Make sure to select the public network interface for the Elastic IP and the private network interface for the next step to connect it to the private routing table.
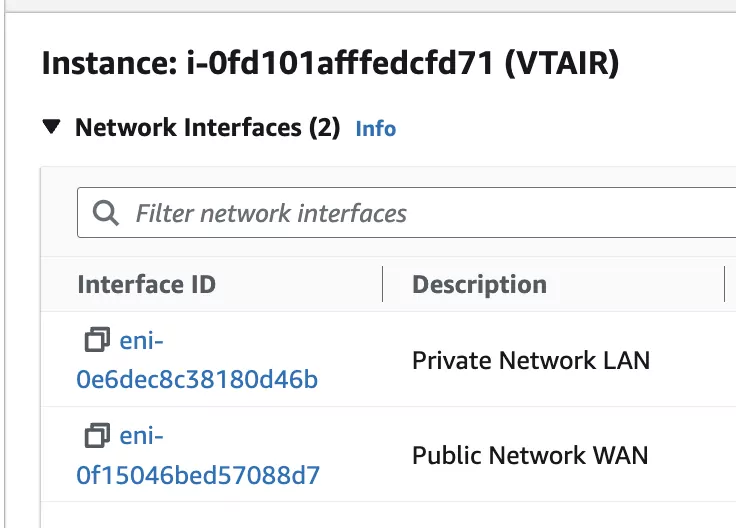
Navigate to EC2 -> Network Security -> Elastic IP and click on Allocate Elastic IP address.
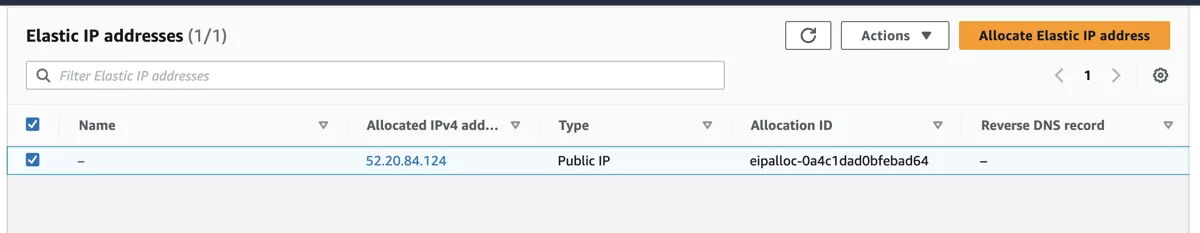
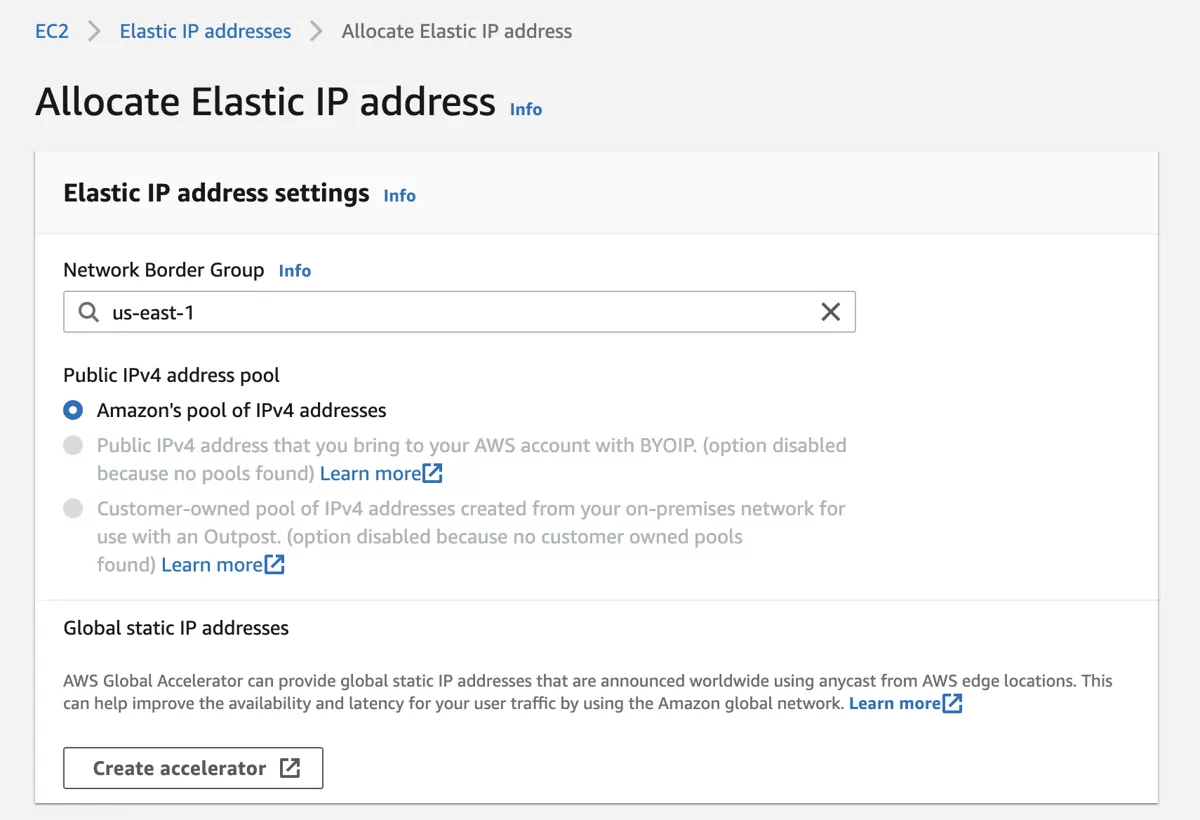
Allocate the IP with the appropriate settings.
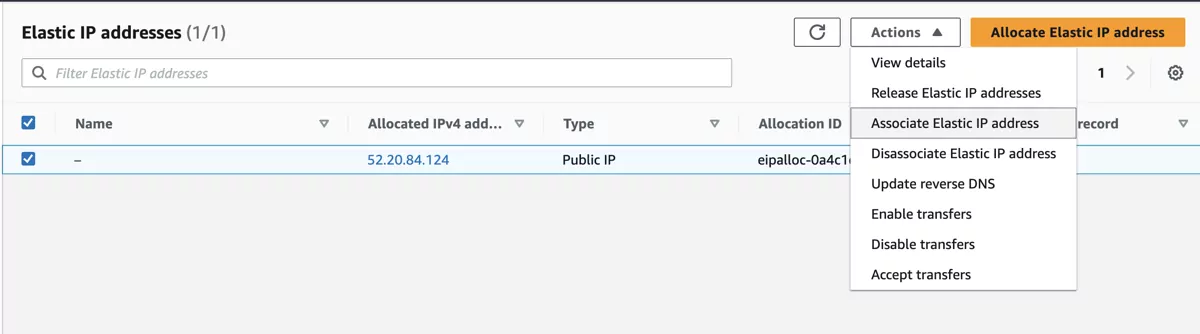
Select the newly created Elastic IP and click on the Action button. Choose the option Associate Elastic IP address and choose the option Network interface.
Look for the public network interface of the VT AIR instance and also select the IP address, in our case 192.168.0.10.
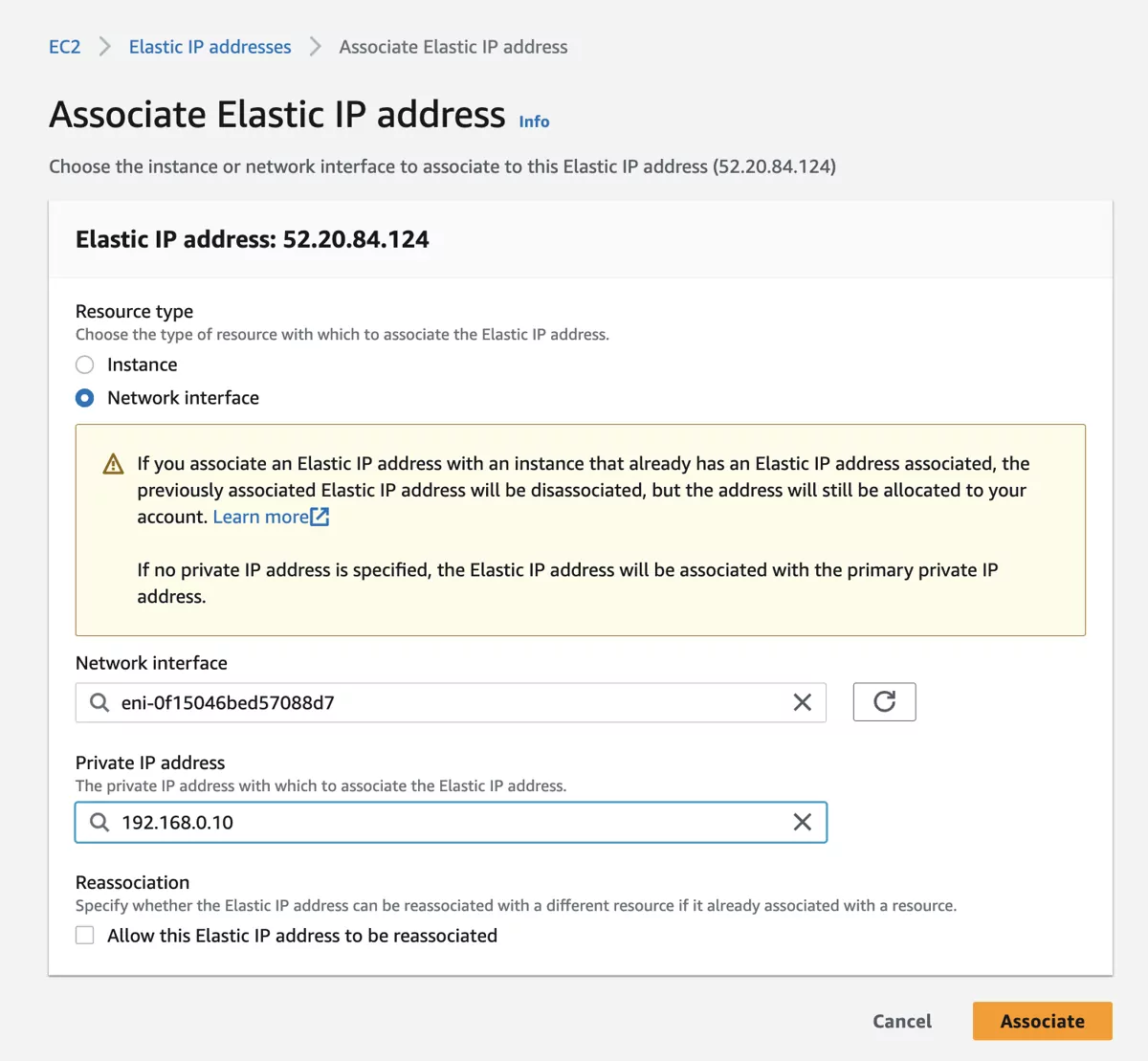
Save the settings.
3.8.3.5.1. Default route pointing to VT AIR LAN interface¶
The next step needs to be completed in the VPC settings. The Private Network Interface (LAN) needs to be the default gateway for the vtair-private-routetable
Navigate to Route Tables and click on the vtair-private-routetable. In the menu on the bottom select the Routes tab and press Edit routes.
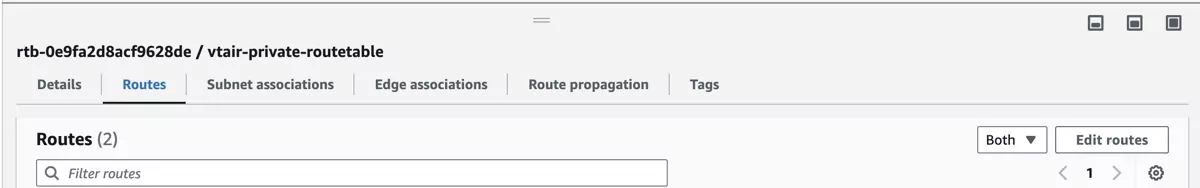
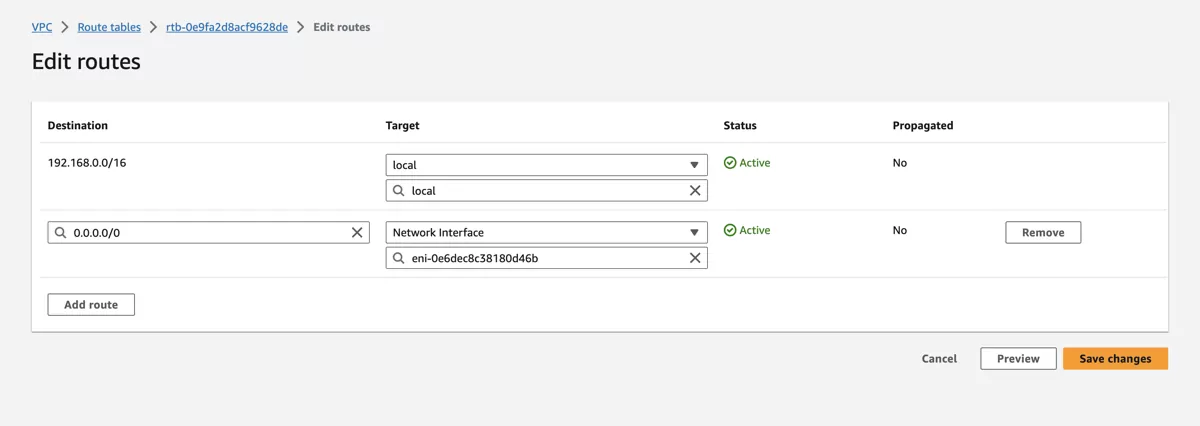
Create a new route with destination 0.0.0.0/0 and as target select Network Interface and select the Private Network Interface from the VT AIR instance.
3.8.4. VT AIR configuration¶
We will now need to login to the VT AIR instance webgui to configure the LAN interface and additional settings.
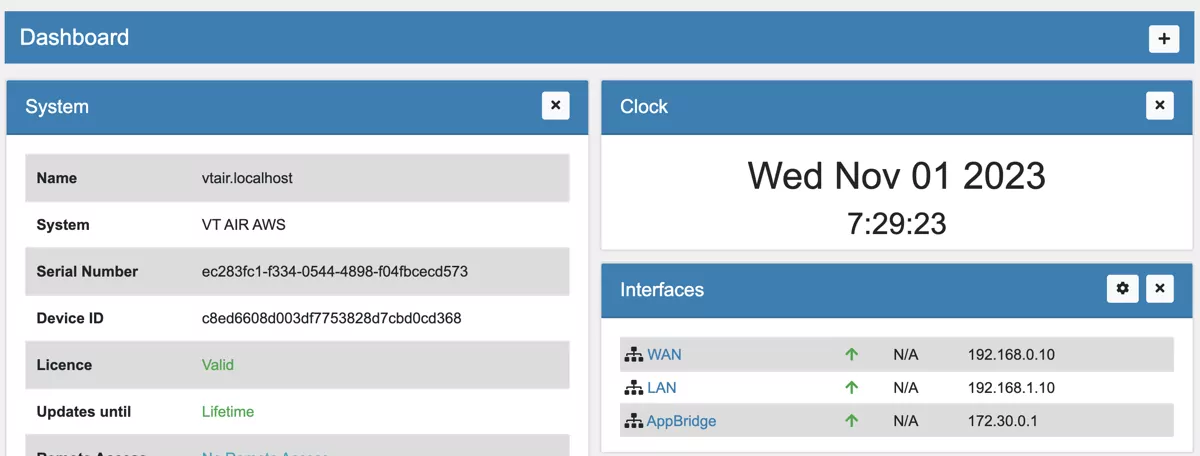
3.8.4.1. Enable and set LAN Interface¶
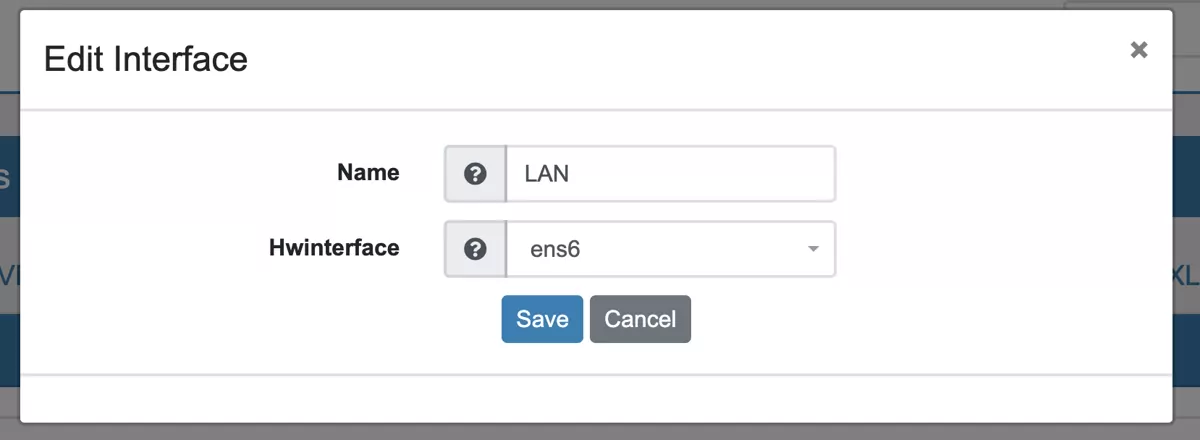
In the webgui navigate to Interfaces -> Assign. Select the edit button next to the LAN interface and assign the new interface to it.
Switch to the LAN interface settings by going to Interfaces -> LAN. Enable the interface and set the IPv4 type to DHCP. Save the settings.
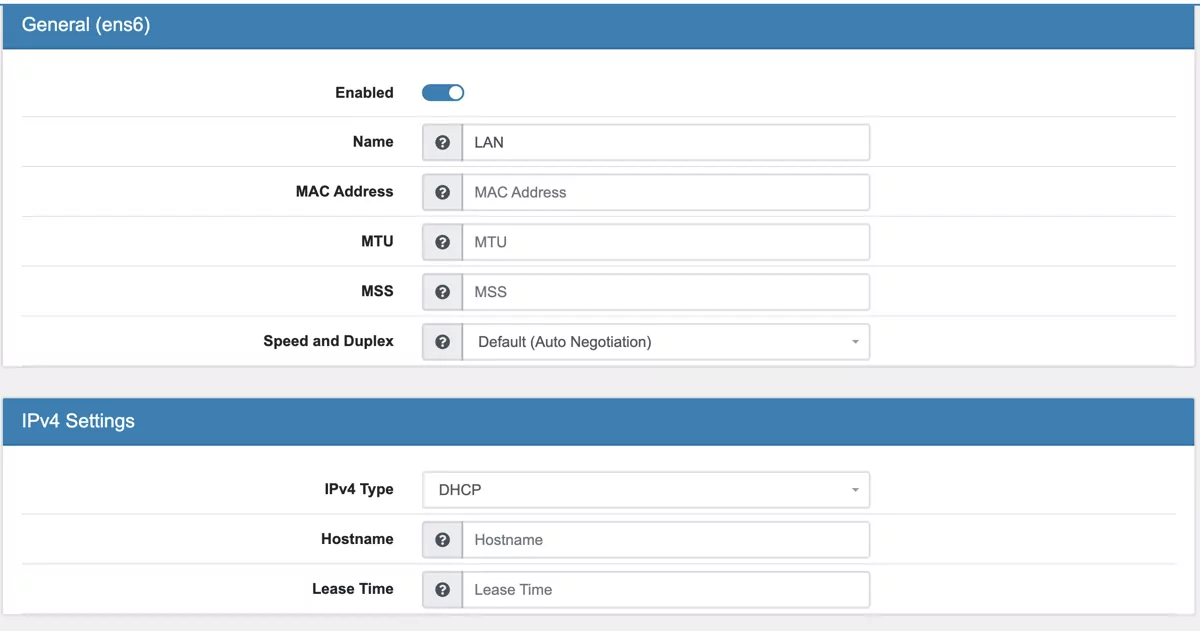
This will enable the LAN interface and the IP 192.168.1.10 will be assigned.
3.8.4.2. Create DNAT Rules and VPN Configuration¶
You can now create all the different setting you need for your setup. To make instances behind VT AIR available to the elastic IP, configure a DNAT rule.
You can also configure the different VPN options.
3.8.5. EC2 VMs¶
Connect EC2 VMs to the private subnet so they are in the LAN network of the VT AIR.
We have created videos to show the entire configurations.
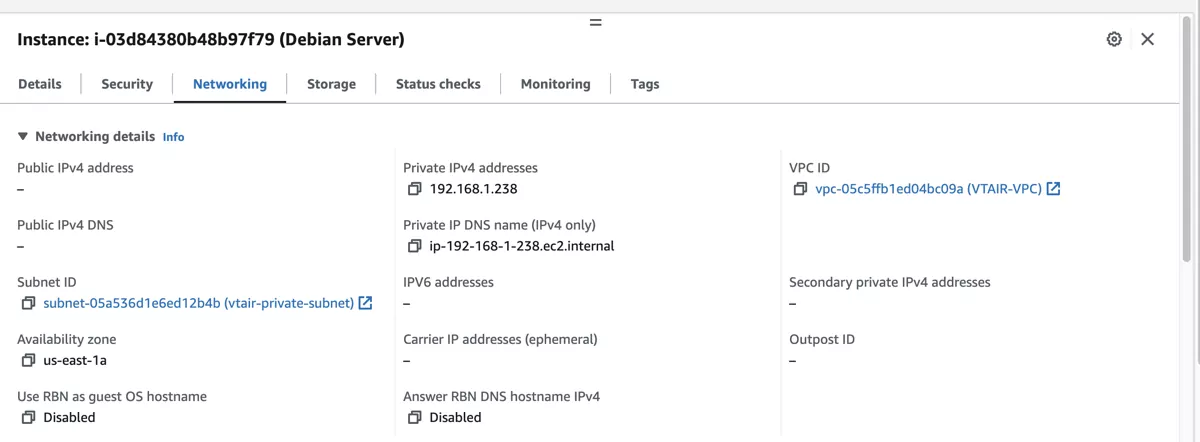
3.8.5.1. Add to the Private Network Subnet¶
If you have already running instances, you need to create an AMI image of the VM, stop it and relaunch it in the new VPC and private subnet. AWS unfortunately does not offer an option to move a running VM to the new VPC/subnet.
When you create a new VM, you can select the VPC and private subnet in the network settings when you create it.
3.8.5.2. Set Private Security Group¶
Make sure to select an appropriate Security Group so the VM can be accessed by the VT AIR.