11.6. DNAT (Prerouting)¶
DNAT or Destination NAT is repsonsible for changing the Destination IP Address of a Network Packet. It is the first rule that is processed in VT AIR when a new Network Packet arrives at the firewall.
With DNAT you can do Port Forwarding or Host Forwarding. DNAT rewrites the destination of the Network Packet to the host you want it to be forwarded to.
Typical applications include the redirection of traffic from a single public IP address to a single private IP address within the private network. By doing this it becomes possible to connect to a single host from outside your local network that would otherwise be hidden. Other applications include the translation of an IP address range if you have multiple hosts you want to connect to.
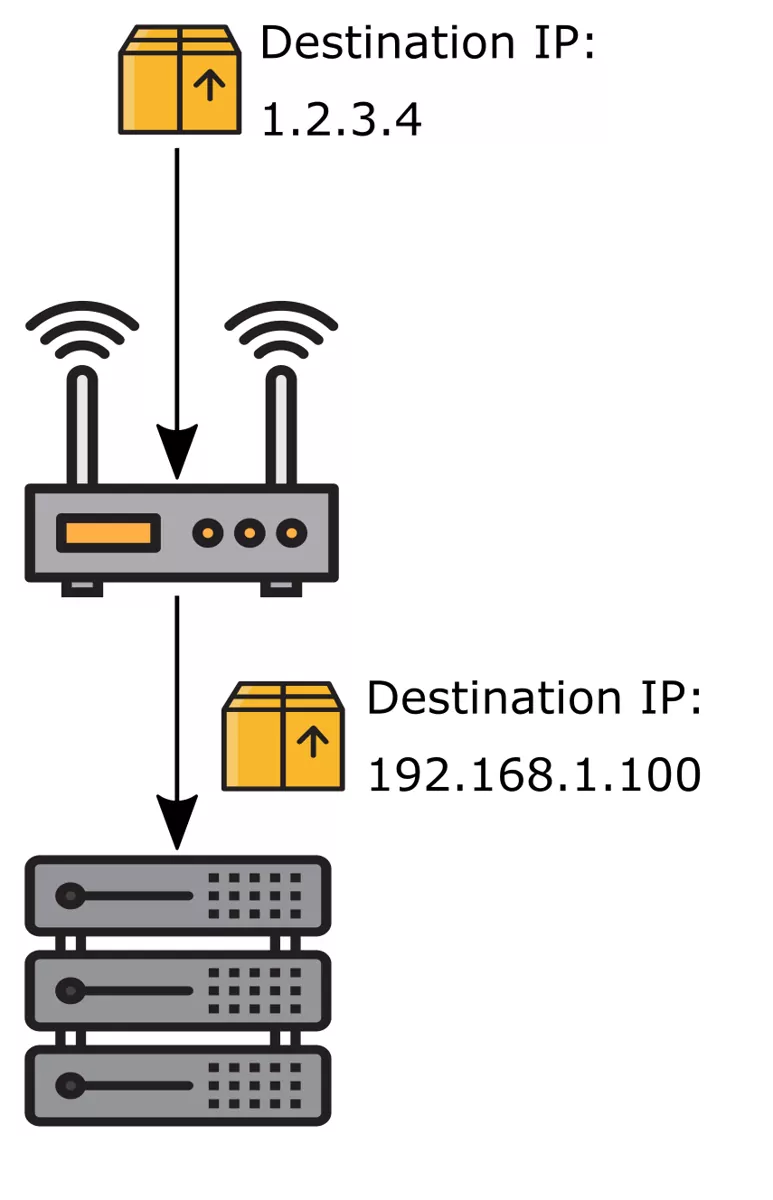
This image was created with icons by srip and Good Ware from Flaticon.
In a port forwarding scenario it is also possible to expand the mentioned scenarios by specific source and destination ports. That way you can have multiple servers running similar services on a single public IP address (separated by differing public ports) for example.
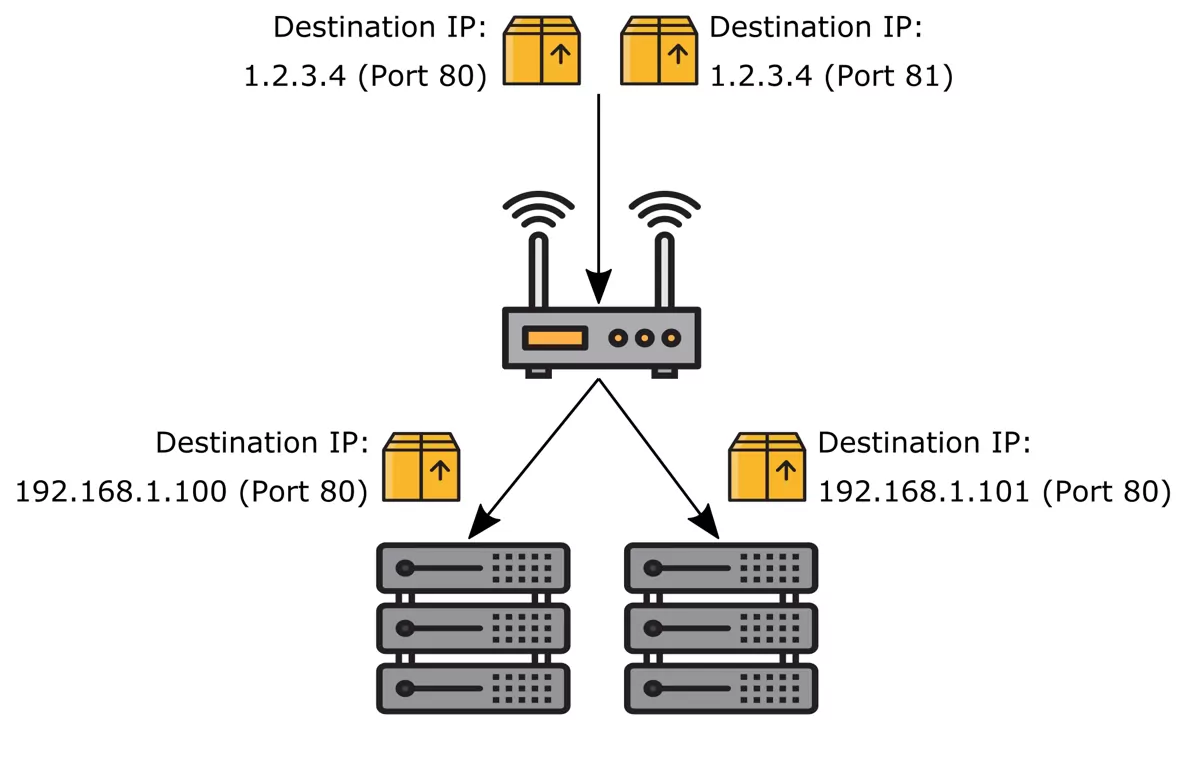
This image was created with icons by srip and Good Ware from Flaticon.
You can find the DNAT Rule Settings at Firewall → NAT.
You will find 3 Tabs here Inbound (DNAT), Outbound (SNAT) and Both (BiNAT).
Click on DNAT to get to the rules.
11.6.1. Move DNAT Rules¶
Rules are gouped by interface and are paged in groups of 20 rules. You can drag and drop user created rules to a different position and you can save that position by pressing save on the bottom navigation. You can also move a rule to the next or previous page or the first or last page if you mark the rule on the left (click on the first the cell of the firewall rule) and use the arrows on the bottom left. If you hover over the buttons they will also show you their description.
11.6.2. Create and Update DNAT Rules¶
If you click Add you will create a new dnat rule on the current interface where you are. You have various options for the rule to set and the rules are structured by the following sections:
General Settings
Sources
Destinations
NAT Settings
Advanced
11.6.2.1. General Settings¶
You can change the following options here:
Enabled Enable or Disable the rule
Interface You can change the Interface of this rule. It will be added to the end of the rule list of that interface if you change it.
Address Family Is either IPv4, IPv6 or both. Depending on the sources and destinations you define the system might not generate a rule for both if you choose IPv4+IPv6.
Protocol The Layer 2 Protocol of the rule.
11.6.2.2. Sources¶
The Source setting has options for the Source IPs and if applicaple Source Ports. You can add muliple entries of each and also mix IPv4 and IPv6. The system will figure out the rule for you.
Source Ports can be found under Advanced Source Settings.
The Invert IP Match option will invert IPs and Macs as well as the ports.
11.6.2.3. Destinations¶
The Destination setting has options for the Destination IPs and if applicaple Destination Ports. You can add muliple entries of each and also mix IPv4 and IPv6. The system will figure out the rule for you.
The Invert IP Match option will invert IPs as well as the ports.
Be aware that due to the structure in Firewall Flow, you have to explicitly choose the Interface IP Network Object if you want the destination to be the firewall itself. Custom IPs or Network Objects are not recognized.
The destination is the original address where the package arrives and not the address where you want it to be forwarded to.
11.6.2.4. NAT Settings¶
You can configure the Redirect IP and if applicaple the Redirect Port. This is the destination that the traffic should be forwarded/redirected to. The firewall will change the destination of the Network Packet to this address/port.
Be aware that you also need a firewall rule on the Interface where the traffic originates so it is allowed to go to the Redirect IP. The option Associate Firewall Rule will create one for you.
If you need a SNAT Rule associated with the DNAT Rule, the option Associate SNAT Rule will create and update a rule for you.
NAT Reflection is the option so your internal network will also be included in the DNAT. It is advisable to use a NAT Override instead because this will be slower. The traffic has to leave and reenter the firewall with this option instead of going directly to the Redirect IP.
If NAT Reflection is enabled you can also choose the Netmask of a Redirect IP in order to generate a NAT Reflection rule that matches the traffic of the same subnet. This is necessary to create a proper SNAT Rule for such traffic or NAT Reflection will not work properly.
11.6.2.5. Advanced¶
In the Advanced Settings you can configure a couple of extra options.
Logging You can log the rules traffic and also add a prefix so you can find it easier. Be aware that firewall logging is an expensive operation and generates a lot of log entries.
Routing Table Choose a different Routing Table for matches. The main routing table is used by default.
11.6.2.6. Changes¶
At the bottom of each rule you can see the Created date, Modified date and the user that last modified the rule Modified user.
11.6.3. Search¶
In the top right corner of the overview page you can search for rules. As search value you can use protocol, source, destination, IP address, port or description.