11.1. Firewall General¶
You can find the Firewall Rule Settings at Firewall → Rules.
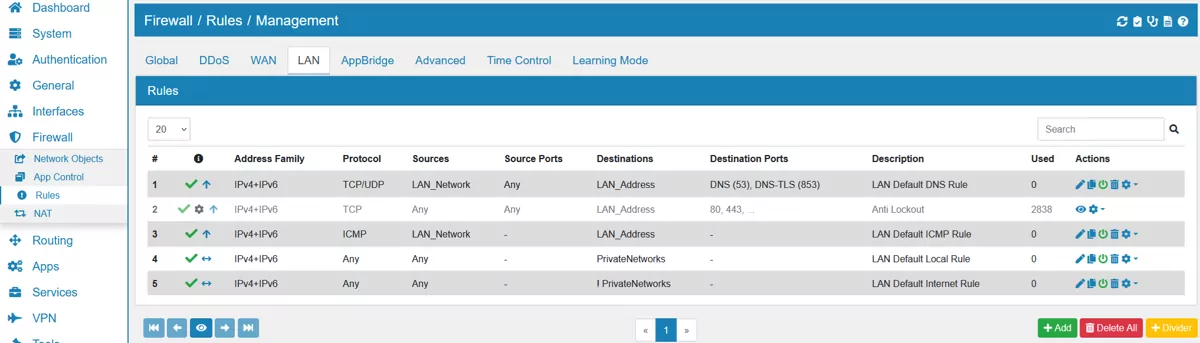
We have a Video Tutorial regarding the firewall rules:
11.1.1. Stateful vs Stateless¶
First a small excurse on what kind of firewall VT AIR is. * |prodname|** is a stateful firewall, it keeps track of open connections and also allows them without rechecking the firewall rules.
The definition of a stateful firewall is:
Note
In computing, a stateful firewall is a network firewall that tracks the operating state and characteristics of network connections traversing it. The firewall is configured to distinguish legitimate packets for different types of connections. Only packets matching a known active connection are allowed to pass the firewall. (Stateful Firewall)
The definition of a stateless firewall is:
Note
Stateless firewalls watch network traffic, and restrict or block packets based on source and destination addresses or other static values. They are not ‘aware’ of traffic patterns or data flows. A stateless firewall uses simple rule-sets that do not account for the possibility that a packet might be received by the firewall ‘pretending’ to be something you asked for. (Stateful vs Stateless Firewalls)
11.1.2. Firewall Flow¶
To better understand firewall rules it is necessary to have a look at how the system processes the rules
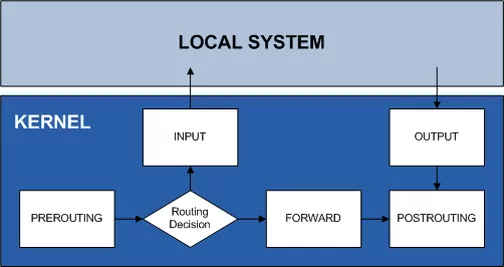
In different stages the following operations are performed
PREROUTING: DNAT
FORWARD: Firewall Rules for forwarding traffic between interfaces
INPUT: Firewall Rules if the destination is the firewall itself (e.g. DNS Server, WebGUI)
OUTPUT: Firewall Rules if the firewall itself is the source (answer from DNS Server, WebGUI)
POSTROUTING: SNAT
We will look into each option throughout this chapter.
Note
OUTPUT is not filtered in VT AIR. The firewall itself can always send out everything.
Note
To match INPUT rules to the firewall, you need to use the Network Objects Address or Network of each Interface. It is not enough to type the IP Address of the interface as destination. The destination will be added as a forward rule and not input.
11.1.3. Firewall Processing¶
In VT AIR, the Global Firewall Rules are processed before any Interface Rule. First match wins and order matters.
11.1.4. Flowtable Bypass¶
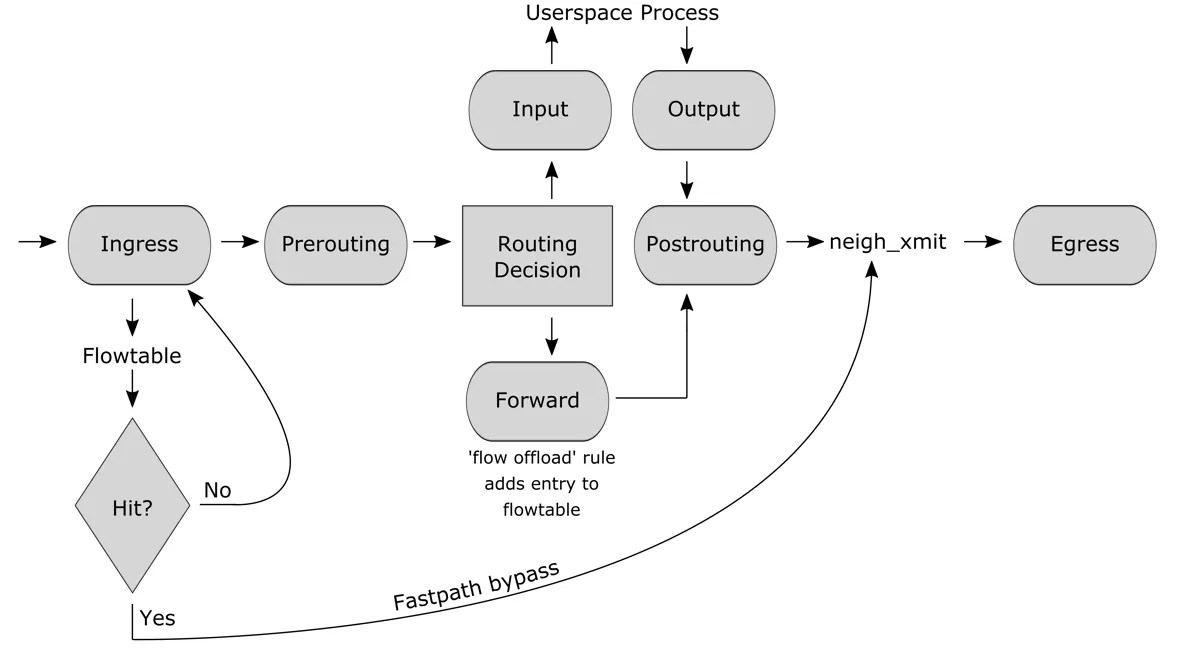
Fig.1: Netfilter hooks and flowtable interactions
We use a feature called flowtable bypass which speeds up the firewall processing by a factor of 2. It bypasses the network stack for established connections and directly forwards traffic from the input interface to the output interface. It only works with stateful connections (TCP/UDP) and is activated after the first package flow is established. If a long lived connection is used flowoffload will only be active for the time actual traffic is seen. The connection will revert to a normal state when there has not been any traffic for a few minutes. The same way it will be turned back to a flowoffload when there is new traffic detected.
It is disabled for firewall rules that have logging or a limiter enabled since those features are not compatible with the flowtable bypass.
11.1.5. eXpress Data Path¶
Our XDP offload technology enhances the speed of the flowtable bypass by a factor of 2.5X and the normal firewall speed by 5X by utilizing the XDP and eBPF technology. Our offloader allows for established TCP/UDP connections to be forwarded directly from the network driver.
Be aware that QoS does not work when XDP is enabled and this is due to the fact that the speed improvements are only possible by bypassing any QoS logic in the VT AIR Firewall.
We recommend to enable XDP for the fastest possible firewall experience.
For more information, we recommend to read the manual section regarding the XDP technology XDP Accelerator.