8.1.13. Advanced Settings¶
You can find the Advanced Settings at System → Settings → Advanced.
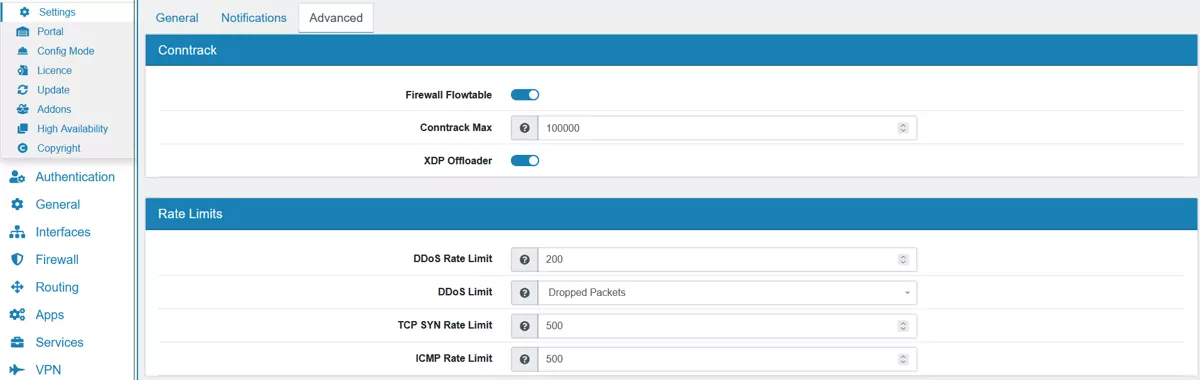
XDP Offloader can be enabled here. But Flowtable needs to be enabled for XDP to work.
8.1.13.1. Rate Limits¶
DDoS Rate Limit is maximum number of connections per IP per minute before the IP is blacklisted for 60 seconds. Needs to be enabled on each interface to be effective. It’s 1000 by default.
DDoS Limit can bei either All or Dropped Packets. All will count also valid traffic against the limit, make sure to choose a high enough limit in case of legitimate traffic. The default value is Dropped Packets.
TCP SYN Rate Limit is 500 by default. A value of 0 means disabled. It specifically targets TCP SYN packets to protect against a SYN attack.
ICMP Rate Limit is 500 by default. A value of 0 means disabled. It specifically targets ICMP packets to protect against an ICMP attack.
8.1.13.2. Timeouts¶
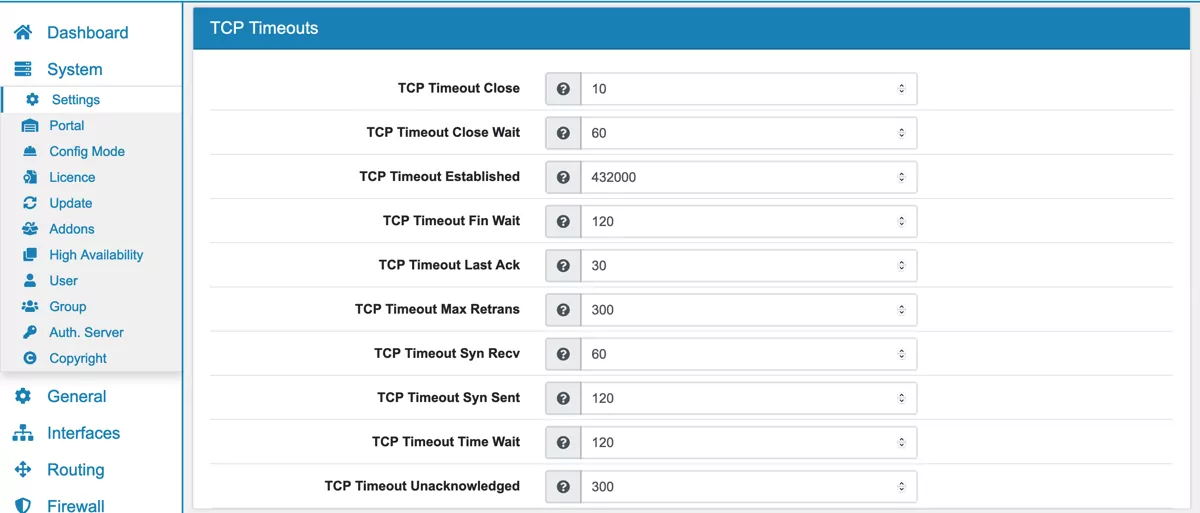
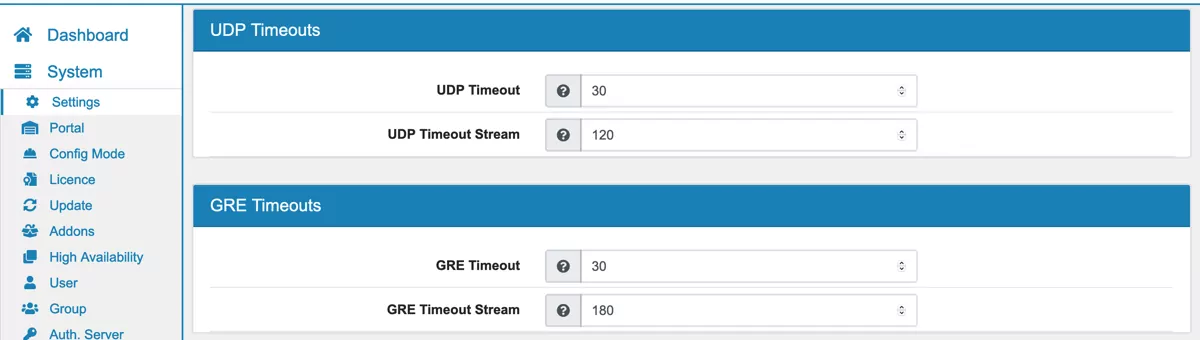
You can configure Firewall timeouts for
ICMP
ICMPv6
TCP
UDP
GRE
as well as the conntrack states table size.
8.1.13.3. Firewall Helper¶
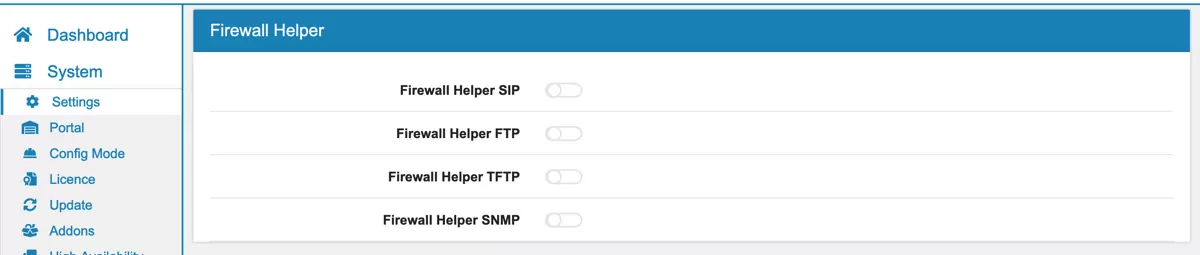
There are 4 firewall helper that help with protocols that need to open up additional random ports
SIP
FTP
TFTP
SNMP
You can enable each helper individually and the firewall will try to track any additional port that a connection of one of those protocols opens without you adding a new firewall rule for it.
8.1.13.4. Network Interfaces¶
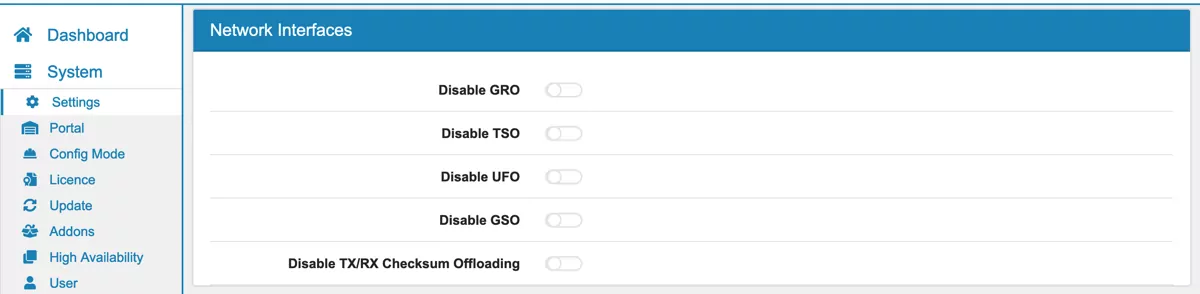
You can disable hardware and software offload features here.
GRO (Generic Receive Offload)
GSO (Generic Segmentation Offload)
TSO (TCP Segmentation Offload)
UFO (UDP Fragmentation Offload)
TX/RX Checksum Offload
A restart is not required to disable or enable any of the settings.
8.1.13.5. Allowlisting¶
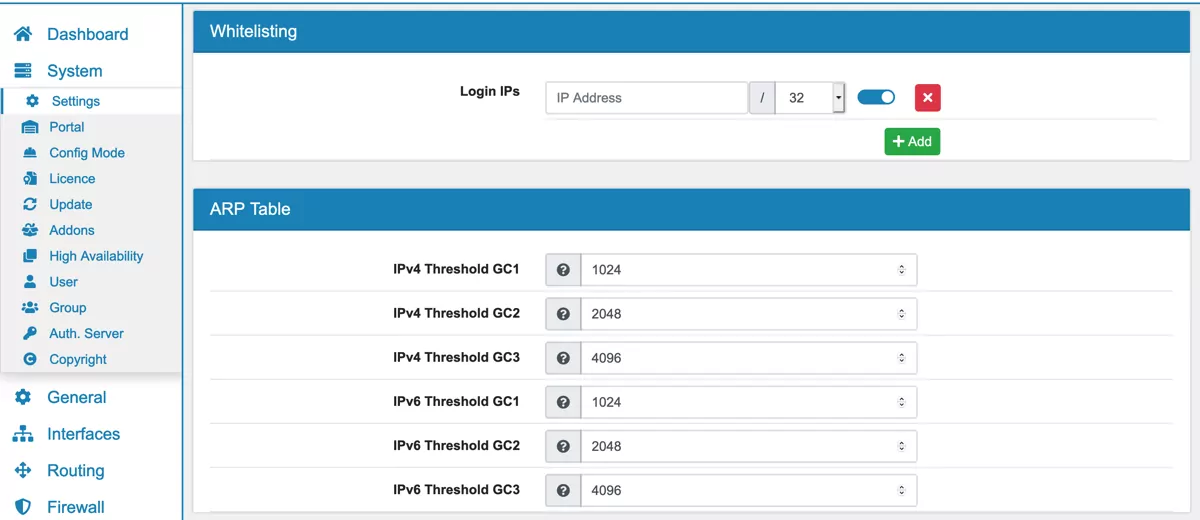
You can add multiple IPv4 or IPv6 addresses or networks which will not be blocked at the VT AIR login, when the username or password are incorrect. Otherwise the login is secured with a blocking function after 3 unsuccessful logins.
8.1.13.6. ARP Table¶
Here you can define the ARP Table cache threshold for IPv4 and IPv6, as well as for GC1, GC2 and GC3. The default values are: 1024 for GC1, 2048 for GC2 and 4096 for GC3. When you have a large amount of clients you might need to increase the values.
8.1.13.7. Miscellaneous¶
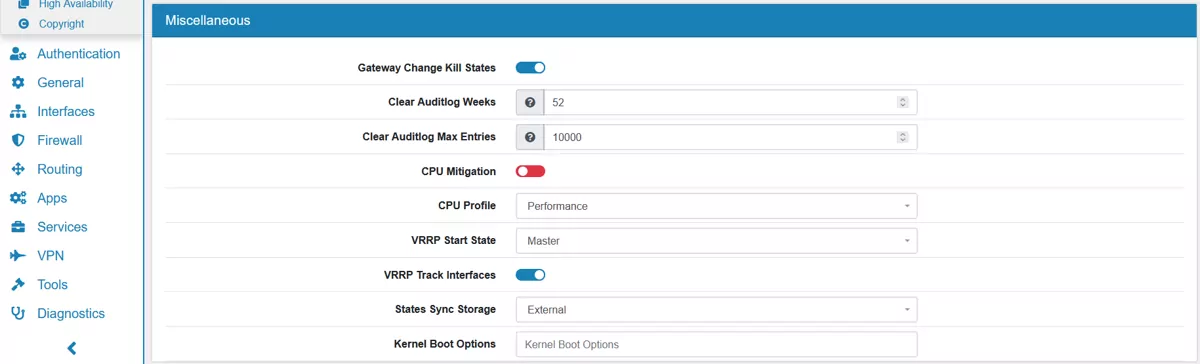
Gateway Change Kill States can be enabled or disabled. When enabled it will kill all States on Gateway change. This is useful when you want to force a gateway change. Be careful, it disrupts all connections though.
Clear Auditlog Weeks defines how long the auditlogs shall be kept with the System Action. Default is 52 weeks.
Clear Auditlog Max Entries Clears auditlogs with the System Action when there are more entries than this value. A large number of auditlogs will slow down the GUI. Please use the txt auditlog from the logging settings instead. Default is 10.000.
CPU Mitigation can be enabled or disabled. It enables a CPU mitigation like Spectre v2. This usually costs around 20% performance.
CPU Profile sets the systems CPU performance and power profile. Performance gives you the maximum speed but also uses more energy and might produce more heat. Dynamic (schedutil) will reduce the CPU speed or put CPUs to sleep if they are not needed. It might be slower to use this profile or it takes longer for CPUs to be ready to perform work. On the other hand your system will use less energy and might stay cooler.
VRRP Start State is either Master or Backup. The master VT AIR should be master and all other VT AIR backup. If not set to master the VRRP IPs will disappear upon changes/service reloads for a few seconds.
VRRP Track Interfaces will track Interfaces and fail over all IPs if an interface goes down.
States Sync Storage can either be External or Inernal. Internal will save all states directly into the active state table at a greater processing cost but faster failover time as the states are available immediately. External will save all states in an external table and will load them at failover time. This is more efficient but there is a delay between the failover and when the states are available.
Kernel Boot Options can be used for custom kernel boot options.
8.1.13.8. Firewall Flowtable¶
Flowtable is a fast forwarding path for TCP/UDP packages that pass the firewall. Packages first traverse the firewall on the normal way. After a state is established the connection is added to the flowtable. Any incoming package will now be sent from the incoming to the outgoing interface directly, bypassing the firewall infrastructure and therefore saving a lot of processing time.
This feature allows for 2-3 times faster package processing and it is compatible with QoS and logging. It is enabled by default. If you enable IDS/IPS only bypassed traffic will be offloaded to the flowtable. If you enable the limiter inside a firewall rule the matching traffic will not be added to the Flowtable as there is no limiter functionality. If you encounter any issues, please disable this feature.
MTU must be the same on all involved interfaces. Otherwise you might see very low throughput on connections.
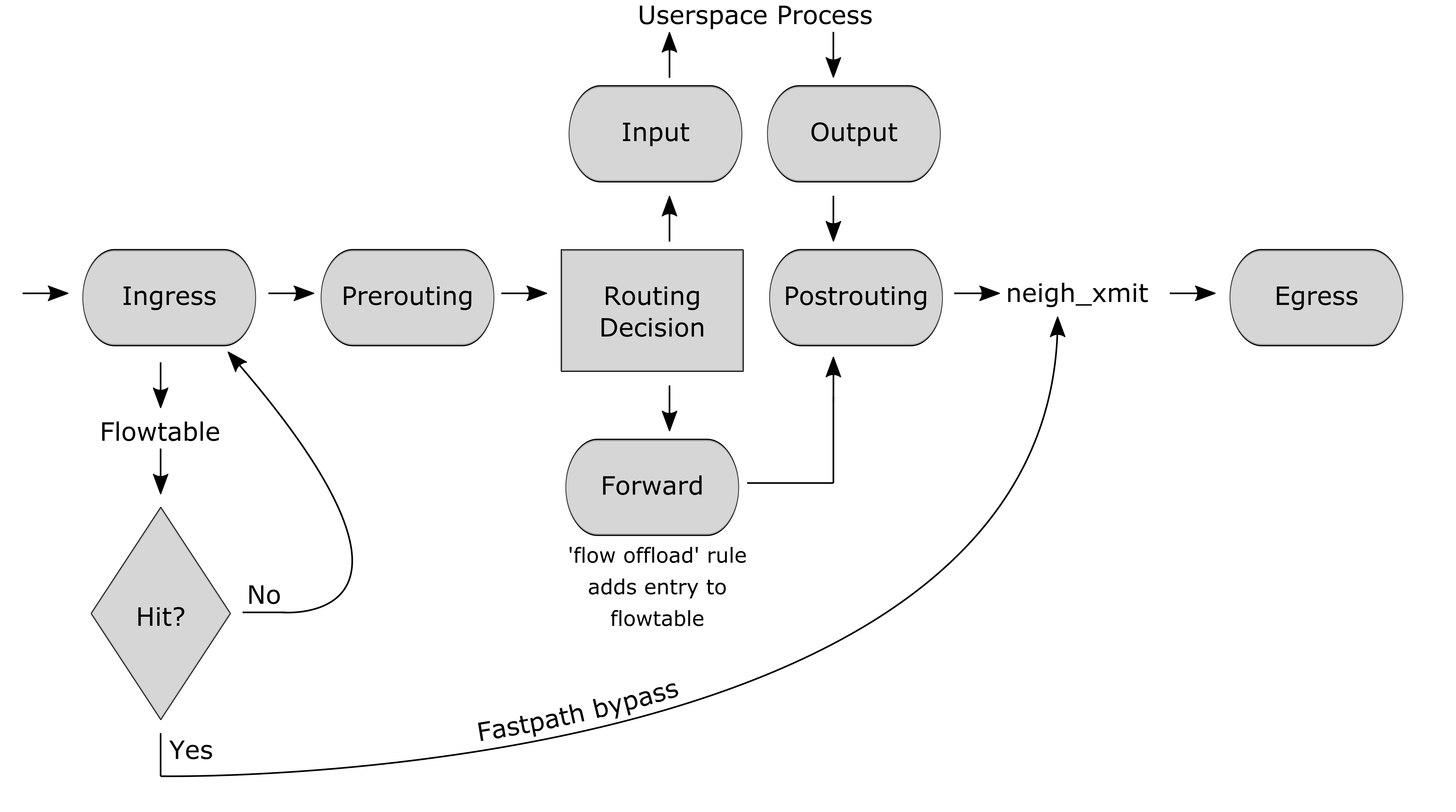
Fig.1: Netfilter hooks and flowtable interactions
8.1.13.9. General Troubleshooting¶
In case of very slow download or upload speeds you can go to System → Settings → Advanced and disable Firewall Flowtable and/or enable Disable GRO. This might improve the speed.
Warning
While disabling GRO and Flowtable Offload might improve network speeds, your Firewall will become much slower with a configuration like this!