18.1.2. IPSec Phase 1¶
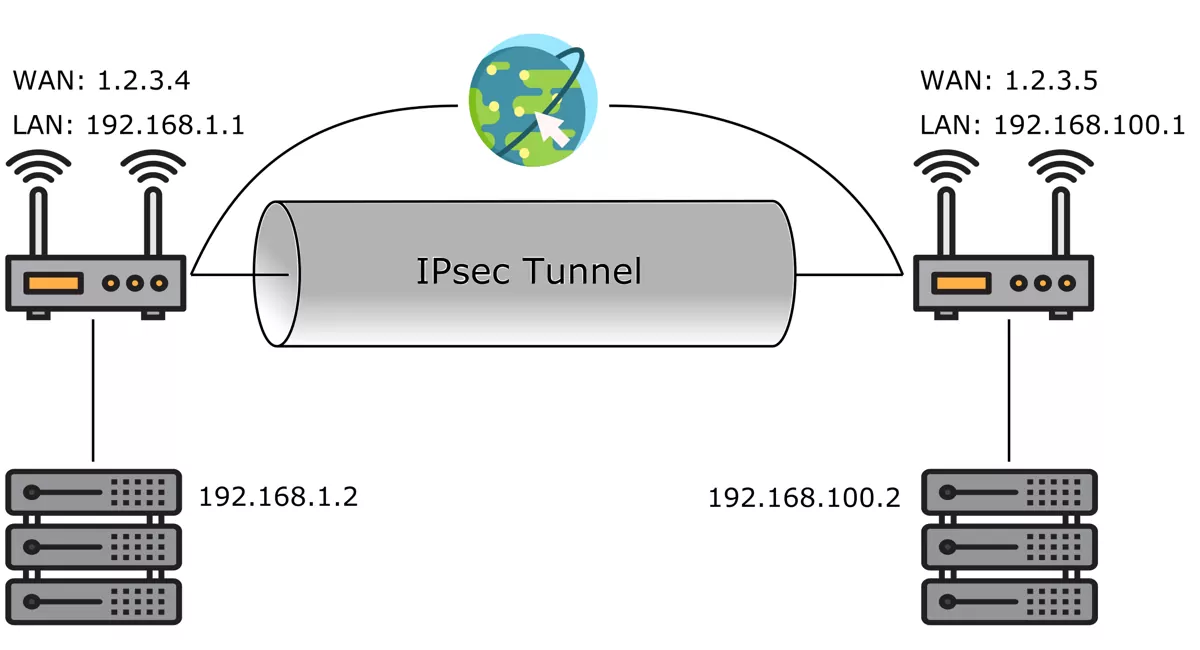
IPsec, also known as the Internet Protocol Security or IP Security protocol, defines the architecture for security services for IP network traffic.
It secures traffic between two entities, either by full encryption or by authentication only.
This image was created with icons by srip and Freepik from Flaticon.
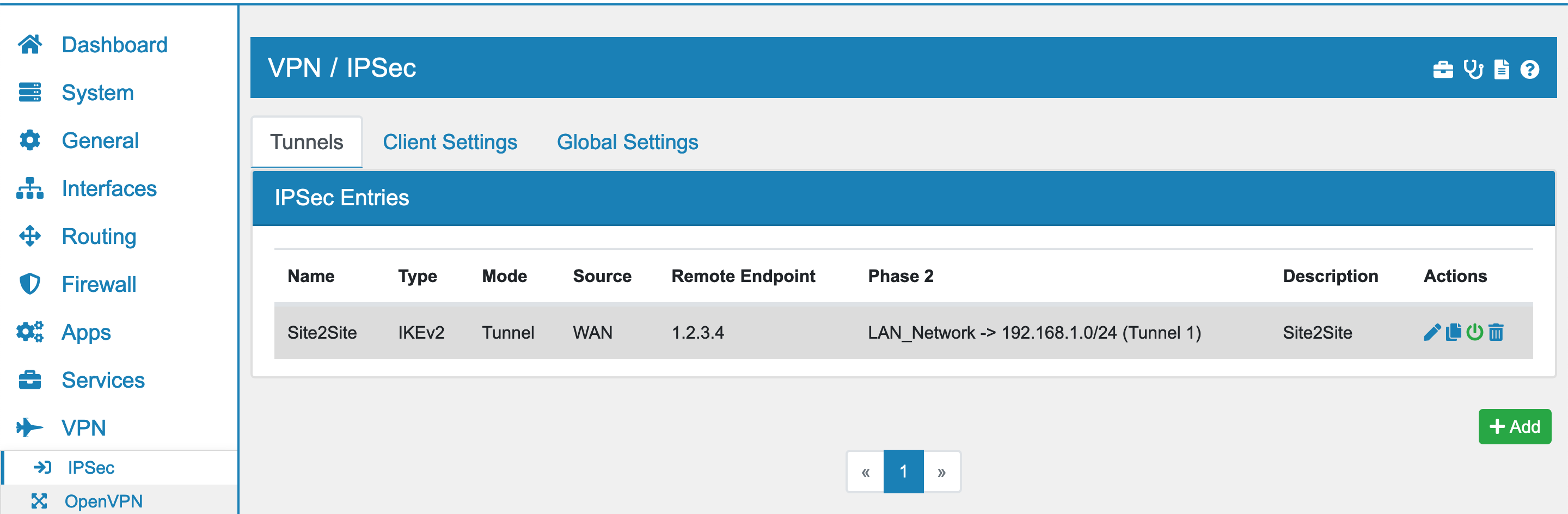
You can find the IPSec Settings at VPN → IPSec.
18.1.2.1. Phase 1¶
The IPSec Phase 1 negotiates the encryption and setting parameter. In VT AIR you have various options to configure a Phase 1.
Interfaces is the sender Interfaces. It also sets the source IP of the IPSec Tunnel on the VT AIR end. If the Interface is a VRRP virtual IP of a HA Setup, only the Master holding the IP has the tunnel activated. The Slave will be on standby for the IPSec. You can select multiple Interfaces here. Be aware that the default route of the system is used when the VT AIR is initializing the connection and therefore only the IP of the interface of the default Route is used. If you choose Any the system will select the IP based on the default route and active interfaces. This is useful for Backup connections if you have multiple Gateways and will select the current interfaces faster.
IPSec Interface lets you choose an existing IPSec interface. It only works if the Phase 2 networks don’t overlap.
IP Type is either IPv4 or IPv6.
IKE Type can be IKEv1 and IKEv2. It is highly recommended to use IKEv2 as it is saver, more robust and easier to setup.
Connection Type can be
Tunnel
Transport
Tunnel creates a tunnel between the two tunnel endpoints. Traffic is automatically encrypted if the source and destination match the IPSec Phase 2.
Transport mode causes the IPsec protocol to encrypt only the payload of an IP packet. The protocol then encloses the encrypted payload in a normal IP packet. Traffic sent in Transport mode is less secure than traffic sent in Tunnel mode, because the IP header in each packet is not encrypted. It encrypts all traffic between the two entities and only has a single IPSec Phase 2 to configure the transport parameter.
Encryption Type is either ESP or AH.
ESP (Encapsulating Security Payloads) provides confidentiality, data-origin authentication, connectionless integrity, an anti-replay service (a form of partial sequence integrity), and limited traffic-flow confidentiality.
AH (Authentication Headers) provides connectionless data integrity and data origin authentication for IP datagrams and provides protection against replay attacks.
Init Type can either be Start/On Demand, Start or Nothing. Start/On Demand will try to connect immediatly and will install a policy to initiate a connection when the first package is flowing. The policy makes sure that no packet will travel to the endpoint unencrypted and will also start a reconnect when the tunnel is down. Nothing will put the Phase 1 in responder only mode.
Interface will create a XFRM interface in the system for this IPSec Tunnel. The interface can be used like any other interface. You need to manually create routes Routes from the Phase 2 to enter the interface. You can also set an IP Address on the interface settings Configure Interfaces. The interface will automatically be set to up or down when the Phase 1 is connected or disconnected. It allows for custom routes and metrics that are removed and added when the interface is up or down. You can also choose an existing XFRM interface, as long as the Phase 2 IP pairs do not overlap. This is useful to manage multiple tunnels in a single Interface.
Remote Endpoints one or more IP Addresses of the remote end. Hostnames are also supported but a working DNS is required for them to be resolvable. There is no DNS caching so if a connection is reestablished the name will be looked up again. This allows for DynDNS hostnames. A remote endpoint of 0.0.0.0 will create an any entry in case your remote IP is dynamic. Identification will be done via Identifier and PSK/Certificate in that case.
Note
As an initiator, the first IP Address is used to initiate the connection to. As a responder, the initiator source address must match at least to one of the specified addresses, subnets or ranges. If FQDNs are assigned they are resolved every time a configuration lookup is done.
18.1.2.2. Phase 1 Authentication¶
Phase 1 Authentication provides you with different options to authenticate the connection.
Authentication Method is either Pre Shared Key, Certificate, EAP TLS (Certificate), EAP MD5 or EAP MSCHAPv2. You can either enter a pre shared key that must match on both ends or a certificate and the corresponding CA. EAP MD5 and EAP MSCHAPv2 are usually used for client authentication with a username and password.
Local Identifier is the identifier of the VT AIR and it is one of
My IP Address
IP Address (Custom IP)
Other
Remote Identifier is the identifier of the remote side and it is one of
Any
Peer IP Address
IP Address (Custom IP)
Other
Use Two Authentications allows you to define a secondary authentication which has the same options as above.
18.1.2.3. Phase 1 Settings¶
Phase 1 Algorithms can be a mix of any of the algorithms. You can add as many combinations as you like.
Lifetime must also match the remote sides lifetime.
Advanced Options give you some more control over the IPSec connection.
Associate Firewall Rule will generate a firewall rule for you and keeps it up to date with any changes you do.
Rekey will let the VT AIR start renegotiation if the connection is about to expire. If turned off, only the remote side can start the negotiation.
Responder Only if you don’t want VT AIR to start the connection but waits for the remote side to start it.
Close Action can either be Connect, On Demand or Nothing. Connect will try to connect immediatly while on demand only initiates a connection when the first package is flowing. Nothing will only close the connection. The default is nothing.
NAT-T should be set to automatic so IPSec can figure out the correct remote IP.
MOBIKE is for the IKEv2 Mobike protocol. Please have a look at Strongswan Mobike for a more detailed explanation.
IPComp is the IP Payload Compression.
Split Connection for IKEv2 creates a new connection for each IPSec Phase 2 entry. Usually they are grouped and sent through a single connection. Depending on the endpoint this is not supported and Split Connection needs to be enabled. This is usually require for Cisco ASA.
Dead Peer Detection lets IPSec check if the remote endpoint is still alive.
DPD Delay defines the time between checks. It is 10 by default.
DPD Timeout defines the time before a connection is restarted if the DPD check failed. It is 30 by default.
DPD Action can either be Restart, On Demand or Nothing. Restart will try to restart immediatly while demand only initiates a new connection when the first package is flowing. Nothing will only close the connection without further action.
Traffic Selector can only be selected in transport mode. It can bei either Any, GRE or VXLAN. In cases other than Any only the selected Protocol/Traffic will be encrypted between the two endpoints.
Fallback IPSec lets another IPSec act as a fallback for this Phase 1. Each IPSec can only be selected once in a fallback scenario.
Ping Check and the following ping options can only be configured if a Fallback IPSec has been chosen. The ping check determines when the fallback IPSec should be used.
Ping IP Address defines the Ping IP Address for the fallback check.
Ping Interval defines the interval between the checks in minutes. It is 5 by default.
Ping Retries defines the number of retries before the connection is terminated and initiated when the ping check failed. It is 3 by default and a value of 0 means disabled.
Ping Fallback defines whether there shall be a fallback to the primary tunnel if ping works again. This option depends on if you ping an outter or inner IP. If you ping an inner IP it will be available on the fallback as well. If you ping the primary IP endpoint this option will check the tunnel endpoint and enabling it is advisable.
Ping Cron lets you select an existing Cron object.
Restart Gateway Change Restart the Tunnel on Main Routing Table Gateway Change. This is useful in Multi WAN setups since ipsec does not always change the gateway automatically.
18.1.2.4. IPSec Action Best Practice¶
IPSec has three different parameter to manage the start and reconnect behaviour: Init Type, Close action and DPD Action. If not set correctly a combination of them can lead to duplicate tunnel connections.
Two sets of configurations make the most sense:
1. Start connection immediatly and restart on failure: Init Type: Connect DPD Action: Restart Close Action: Nothing
If no DPD is used the Close Action should be Restart.
2. Start connection when traffic is flowing (also makes sure that no unencrypted traffic is flowing): Init Type: On Demand DPD Action: Nothing Close Action: Nothing
For Encryption AES-256 SHA 256 DH-16 is recommended as a minimum for the phase 1. AES-GCM is not recommended for the phase 1 but highly recommended for the phase 2 encryption, as it provides the fastest speed for IPSec.
18.1.2.4.1. IPSec Multi WAN Setup¶
Creating a Multi WAN Setup with automatic failover to a backup WAN also requires to set Restart Gateway Change. The IPSec Tunnel does not always follow the Gateway change to a different WAN. The restart will disconnect and reconnect the tunnel to force it to the new active WAN connection.
18.1.2.5. IPsec with Failover¶
If you want to configure your IPsec with failover support you can configure your server and clients as described in IPSec.
If you haven’t configured your High Availability setup do so as described in High Availability and enable the Configuration Sync option. Note the Virtual IP address of the Interface your IPsec server runs on.
On your remote device go to VPN → IPsec and configure your VPN connection. Enter the Virtual IP you noted earlier as Remote Endpoint instead of the real address of the device. This way the IP address of the remote device doesn’t change in case the secondary router takes control.
18.1.2.6. Performance¶
Note
Each SA is assigned to a single CPU. To get the best performance you might want to enable Split Connection if you have multiple phase 2 entries. This will create one SA for each phase 2 and therefore utilize more CPUs. It has to be enabled on both ends of the connection.
18.1.2.7. IPSec Firewall Rules¶
Note
You need to create Firewall Rules on the IPSec Tab or if you chose to create an Interface, in the newly create XFRM_XXX Interface, in order to allow network traffic from the other end of the ipsec. Please have a look at Firewall Rules (Forward and Input) for a detailed explanation on how to create Firewall Rules for an interface.