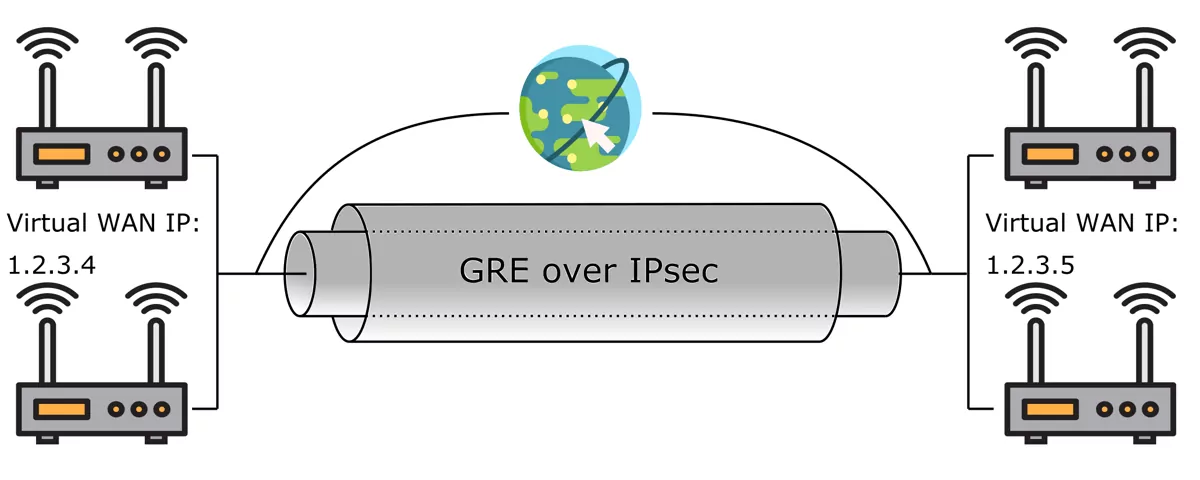
18.1.6. GRE over IPSec¶
GRE/GRETAP over IPSec can be configured in VT AIR. This is useful for encrypted site-to-site connections. In most cases it should not be necessary to have a GRE/GRETAP tunnel within your IPsec tunnel since you can add the remote subnets directly to your Phase 2 configuration.
First create a GRE Interface as described in Tunnel. Make sure to activate the option assign to a new interface. Afterwards configure the Interface in Configure Interfaces. Set the GRE Endpoints and the internal IPs (local and remote tunnel IPs) for example 10.10.10.1 (local) and 10.10.10.2 (remote).
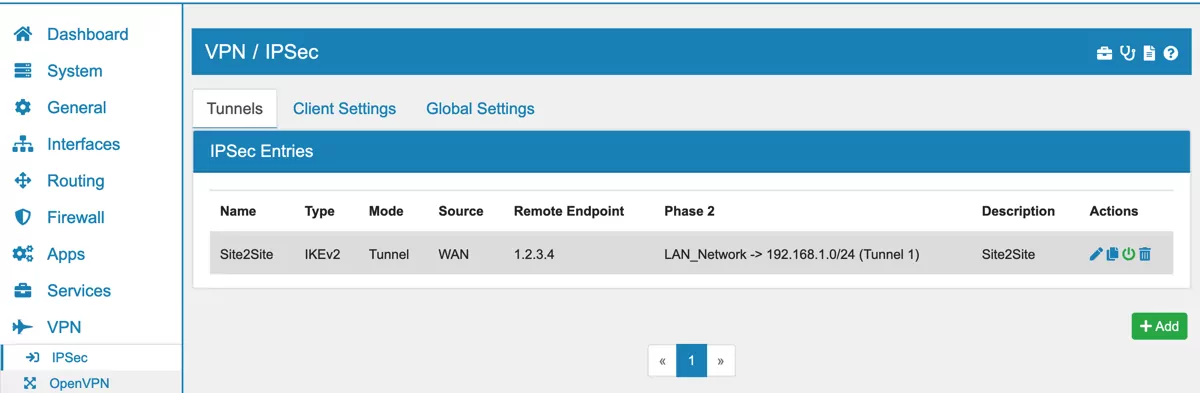
Create a new IPSec Phase 1 and choose Connection Type Transport. The Interfaces must be the WAN interface that is used to send the GRE packets to the endpoint. The Remote Endpoints is the remote tunnel IP (the external tunnel IP of the remote end e.g. 1.2.3.4). Also enable the option GRE over IPSec to encrypt only the GRE traffic. Configure the other parameters according to your IPSec endpoint.
A IPSec Phase 2 has to created as well with matching encryption parameters.
When the IPSec Tunnel is up it will encrypt all the GRE packets to the remote endpoint.
You might need to add Routes to have additional traffic pass the GRE tunnel as well as Firewall Rules (Forward and Input) to allow the traffic.
18.1.6.1. Encrypting Site-to-Site networks¶
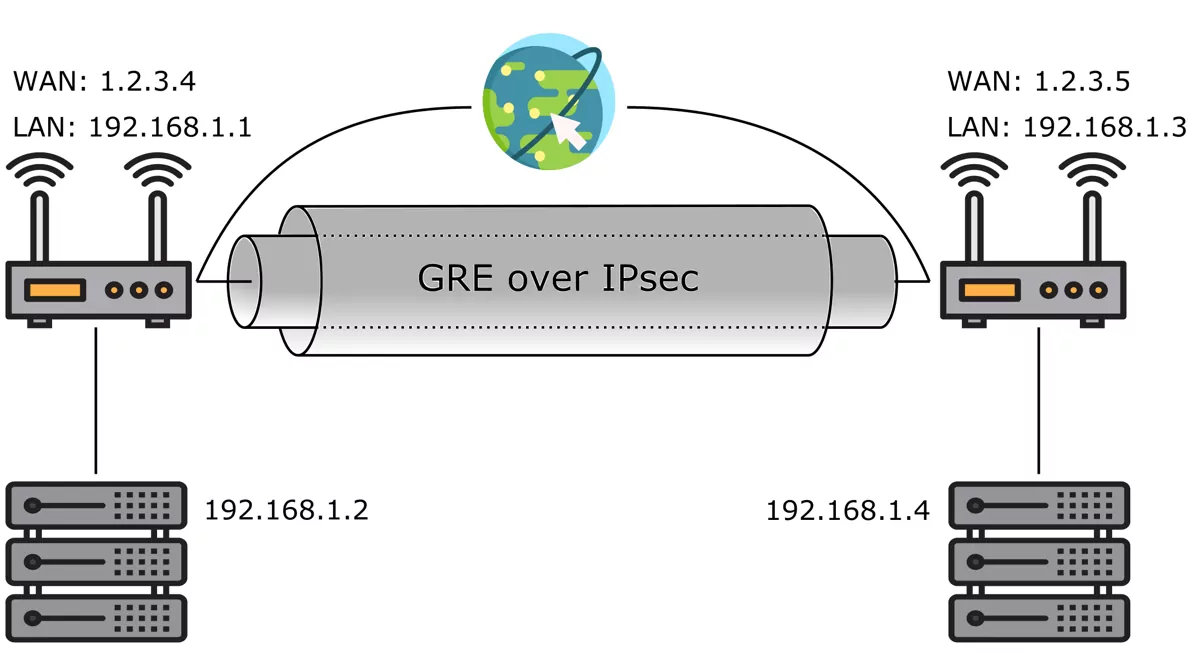
To combine multiple physical locations of your network into e.g. one large company network in a secure way you can use IPsec (and GRE/GRETAP). Follow the steps above and/or refer to Bridging Scenarios. This leaves you with a GRE/GRETAP tunnel that is encapsulated and encrypted in an IPsec tunnel. Your networks will then appear as if they were one physical network.
This image was created with icons by srip and Freepik from Flaticon.
Alternatively to using GRE over IPsec you can also use a standalone IPsec tunnel. Simply add the remote network and the local network that you want to connect as a Phase 2 entry in your IPsec tunnel. In the example below your local LAN network will be tunneled to the remote network with the public IP address 1.2.3.4 and the private IP address range of 192.168.1.0.
18.1.6.2. Failover Support¶
In a High Availability setup you can also include your GRE over IPsec tunnel. This keeps the tunnel open even if the secondary router takes control. First, configure your tunnel without failover support and configure your High Availability setup as described in High Availability. Then take note of the virtual IP address that you assigned for the Interface your tunnel is running on.
Add the virtual IP to both your GRE tunnel and your IPsec tunnel as described in IPsec with Failover and GRE with Failover. Your tunnel will now work seamlessly on all the VT AIR devices that are included in your High Availability setup.