17.2. 802.1X Authenticator¶
You can find the 802.1X Authenticator Settings at Services → 802.1X Auth..
802.1X Authenticator, authenticates devices on the layer 2 before they can access the network. The authentication can be done with a user/password or a certificate. This adds an extra Layer of security to your network a you can block out unkown devices.
Before you can use the 802.1X Authenticator it has to be installed. You can install it at System → Addons.
Upon activation on a network interface the 802.1X Authenticator will block all forwarding traffic on the interface until a device is authenticated. The authenticated devices can be seen on the Diagnostics page 802.1X Authenticator.
Warning
DHCP Server can not be enabled on any interface when using 802.1X Authenticator. The 802.1X Authenticator is blocking the DHCP Server port and is not starting with an active DHCP Server. This is necessary for the 802.1X Authenticator to detect new devices on the network. Make sure to have another DHCP Server in the network
17.2.1. Settings¶
On the page the 802.1X Authenticator can be enabled or disabled. You can create an 802.1X Authenticator for each physical interface that you like.
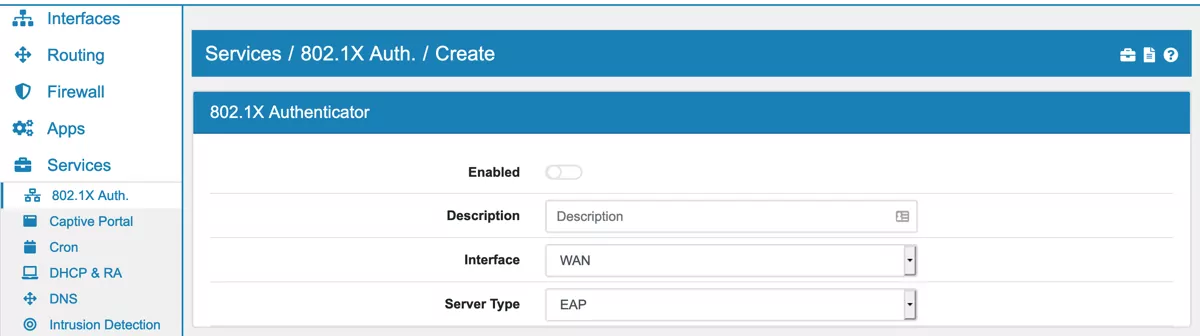
Server Type for authentication. Device authentication can either be send to an radius server or the 802.1X Authenticator can act as an EAP Authentication Server.
17.2.1.1. Radius Authentication¶
An authentication radius server and an accounting radius server can be configured. All requests from devices will be relayed to the server and the result determines if a device is authenticated.
You need to add the radius server, the identifier of the 802.1X Authenticator and a shared secret.
17.2.1.2. EAP Authentication Server¶
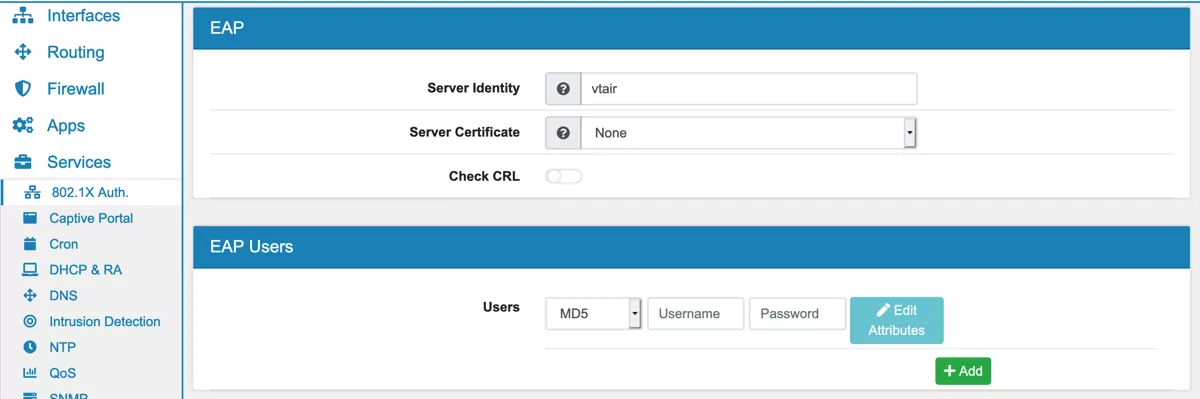
The 802.1X Authenticator can act as an EAP Authentication Server.
Server Identity sets the identity used in the EAP Authentication.
Server Certificate is optional and must be set if you use certificate authentication
Check CRL for a certificate revocation list.
A device can be configured in the EAP Client list:
Username of the device
Password of the device
Authentication Algorithm the following algorithms are supported: MD5, PSK, MSCHAPV2, TLS, TTLS
Key Value Pairs can be set and sent to the device upon successful authentication. They are in the same format as a radius key/value pair.