17.17. Web Filter¶
You can find the Web Filter Settings at Services → Web Filter.
The Web Filter is using SquidProxy, a caching proxy for the Web supporting HTTP, HTTPS and more.
17.17.1. Settings¶
17.17.1.1. General Settings¶
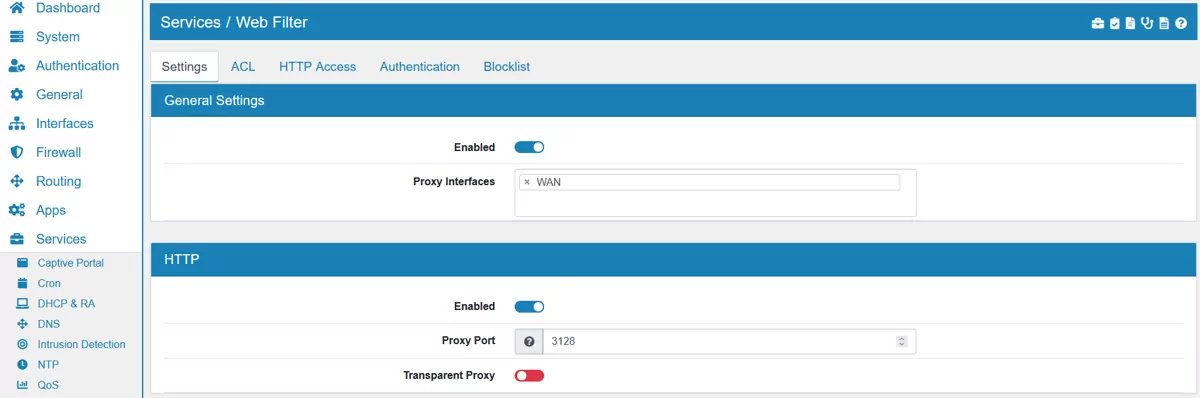
Enabled can be changed to enable or disable Web Filter. It’s disabled by default.
Proxy Interfaces are the interfaces and addresses the proxy is running on.
You can export the settings in the top right corner as an Excel spreadsheet.
17.17.1.2. HTTP¶
Enabled can be changed to enable or disable HTTP. It’s enabled by default.
Proxy Port is the port the HTTP proxy server will listen on. Default is 3128.
Transparent Proxy can be enabled to make the proxy act as a transparent proxy. It’s disabled by default. The Transparent HTTP Proxy always runs on 127.0.0.1 port 3129. Please DNAT the traffic to the address.
17.17.1.3. HTTPS¶
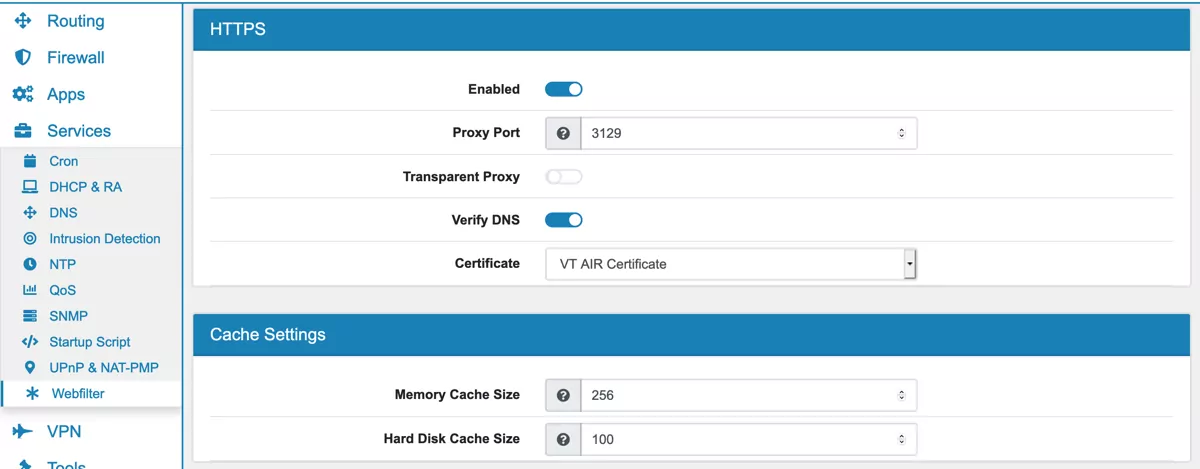
Enabled can be changed to enable or disable HTTPS. It’s disabled by default.
Proxy Port is the port the HTTPS proxy server will listen on. Default is 3129.
Transparent Proxy can be enabled to to make the proxy act as a transparent proxy. It’s disabled by default. The Transparent HTTPS Proxy always runs on fd00:7371:7569:6470:726f:7879::1 port 3129. Please DNAT the traffic to the address. Since traffic is encrypted and the Transparent Proxy of VT AIR does not do a Man in the Middle Attack the desired information are obtained from looking at the connection start and extracted IPs and the SNI field. This leaves the client without warnings about the connection while obtaining enough information to evaluate HTTP Access rules.
HTTPS Proxy Mode can be configured when Transparent Proxy is enabled. It can be either SNI Scan or Man-in-the-Middle. SNI will look at the SNI field during the TLS handshake. Man-in-the-Middle will break the connection and presents the client it’s own Certificate. The client must trust the Certificate or a browser warning is generated.
Verify DNS Verify HTTPS Header Domain against the DNS entry. Disabling this allows security risks like spoofing. On the other hand google or amazon sites usually do not work when transparent SSL is enabled because they use so many DNS entries.
Certificate can be configured which certificate will be used.
17.17.1.4. Cache Settings¶
Hard Disk Cache Size is the amount of disk space to use in megabytes. The default is 100 MB.
Memory Cache Size specifies the ideal amount of memory to be used in megabytes. Default is 256 MB.
17.17.1.5. Clamav Anti-Virus¶
ClamAV can scan the webtraffic of the proxy for viruses. This only works when the traffic can actually be seen unencrypted and is uneffective in the transparant HTTPS case.
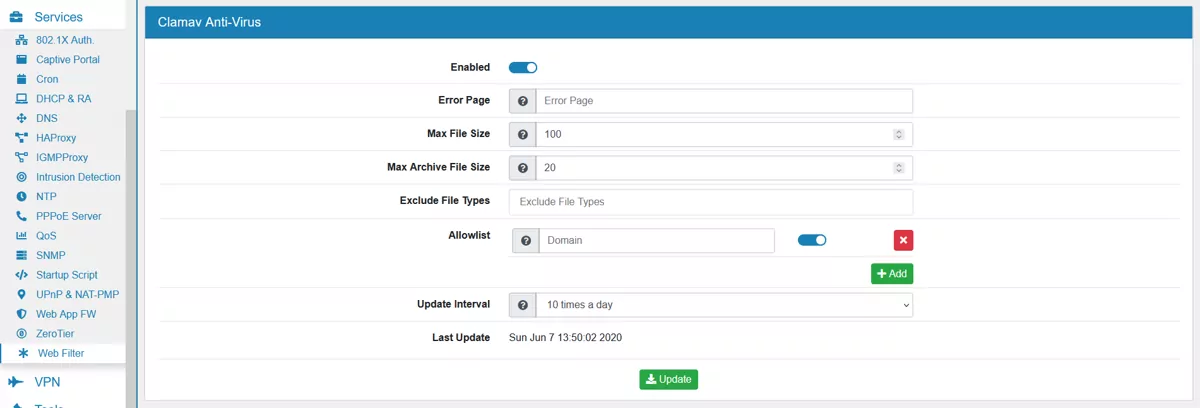
Enabled enable or disable the virus scan.
Error Page is the complete url of an error page where the user is redirected to if a virus is found.
Max File Size is maximum file size to scan in MB.
Max Archive File Size is maximum archive file size to scan (e.g. ZIP) in MB.
Exclude File Types can be used to exclude specific file types from the virus scan.
You can add multiple Domains to configure an Allowlist. Traffic from those Domains will not be scanned by the virus engine.
Update Interval specifies how often the virus definition should be updated during a 24 hour period.
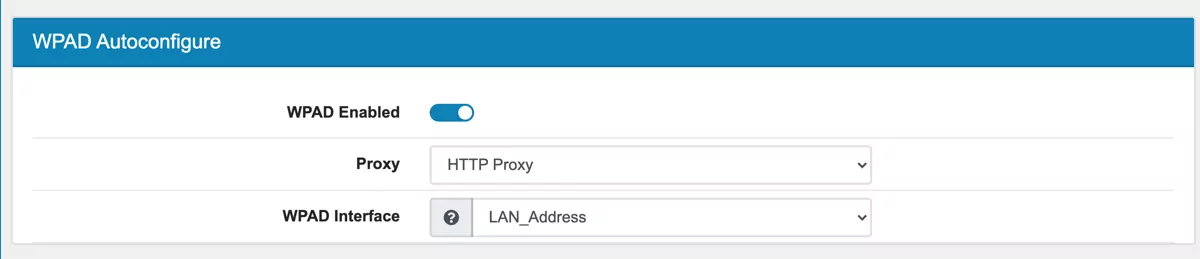
17.17.1.6. WPAD Autoconfigure¶
WPAD allows your clients to enable the Auto Proxy setting and find the VT AIR Webfilter.
Proxy lets you choose the HTTP or HTTPS proxy port.
WAPD Interface is the interface address used to propagate to the clients. Only one ipaddress can be used here so make sure that the connection is allowed in the Firewall.
A DNS record with wpad is created to find the settings.
The wpad file is served by the webserver over port 80.
17.17.1.7. Advanced¶
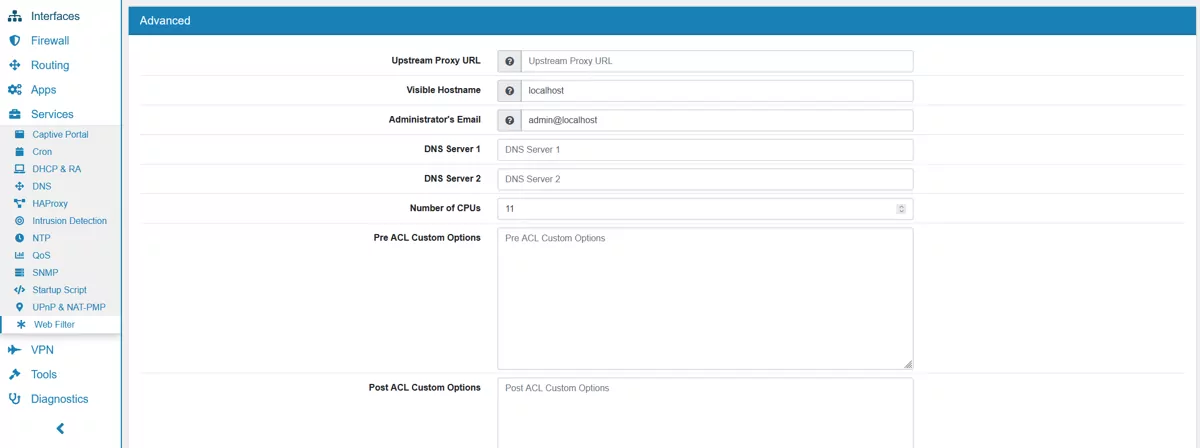
Upstream Proxy URL is the entire Upstream Proxy URL e.g. http://user:password@proxy.server:port/.
Visible Hostname will be displayed in proxy server error messages. Default is localhost.
Administrator’s Email will be displayed in error messages to the users. Default is admin@localhost.
DNS Server 1 and DNS Server 2 can be configured here.
Number of CPUs is by default the number of available CPUs minus one. The Webfilter will run on all configured CPUs allowing for a higher processing capacity.
Pre ACL Custom Options can be used for custom configuration parameters for the config. They will be placed before the ACL data.
Post ACL Custom Options can be used for custom configuration parameters for the config. They will be placed after the ACL data.
17.17.2. ACL¶
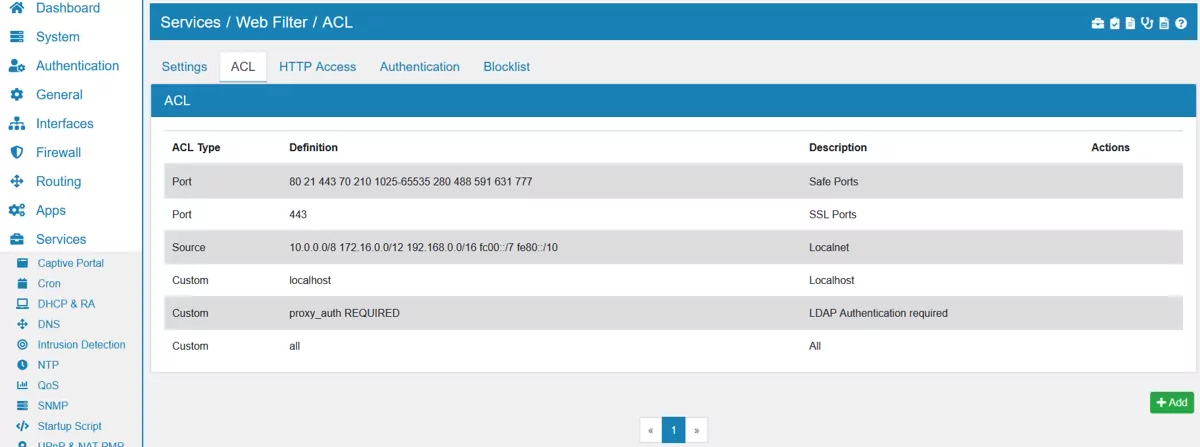
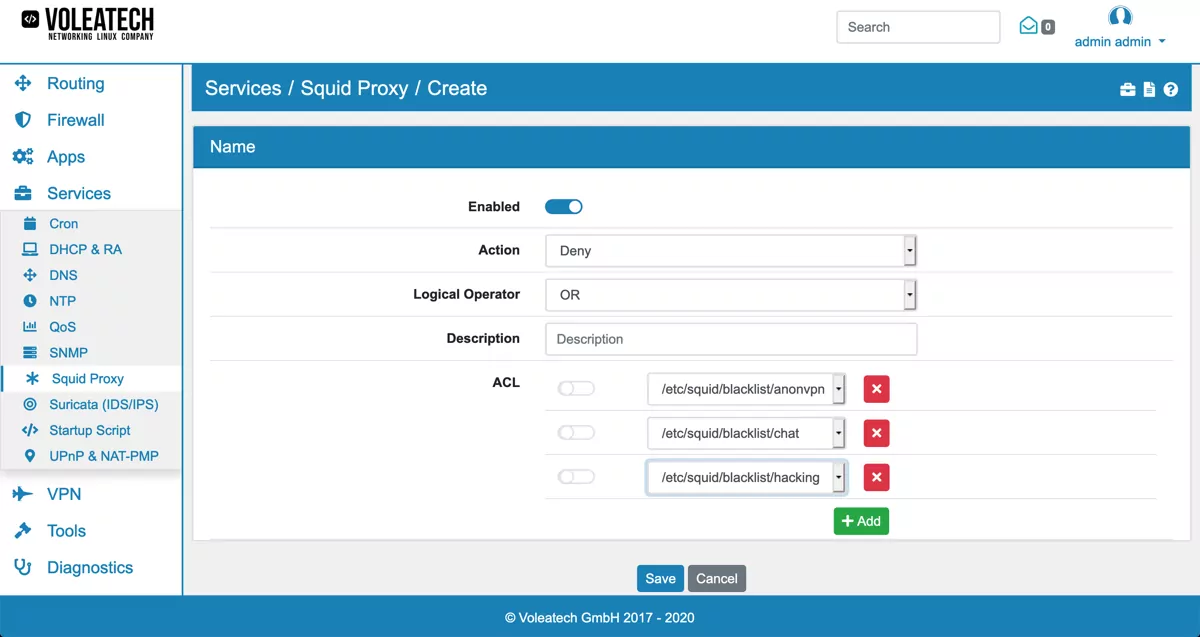
Defining an Access List. An ACL has a type Source, Destination Domain, Destination Regex, Port, Protocol or Custom. Custom allows you to pick an ACL Type from the Squid manual (Squid ACL).
An ACL entry can have one or multiple entries and you have to enter one per line. For example the ACL Source could contain:
192.168.100.1
192.168.101.0/24
Log Full Traffic enables you to log the full data packet that matches this ACL. For HTTPS traffic it must be bumped first so it can be read unencruypted.
SSL Bump SSL Bump and look into SSL traffic. Splice reads the SNI field and the certificate but does not decrypt the traffic. Bump will create a MITM with the squid certificate and encrypt and decrypt all traffic. The option allows you to only read or encrypt matching traffics. Please run Squid in HTTPS mode and choose a Certificate or this option will not have an effect.
17.17.3. HTTP Access¶
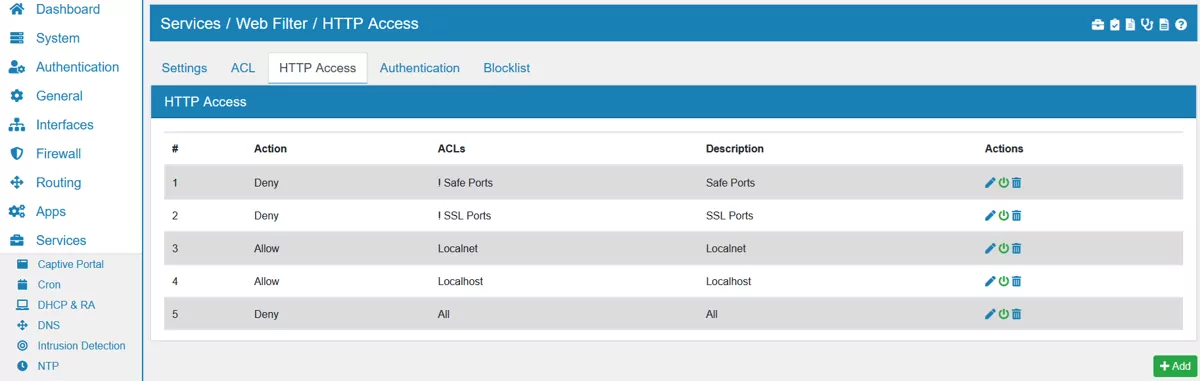
Allowing or Denying access based on defined access lists. HTTP Access lists are defined by combining ACLs with either AND or OR. You can also negate an ACL with NOT.
This allows you to define access or decline access based on ACLs.
For example to deny access to www.google.com you have to create an ACL of type Destination Domain. You can use that ACL in HTTP Access of type Deny.
The order of HTTP Access matters and you can drag & drop entries in the list to create the desired order.
17.17.4. Authentication¶
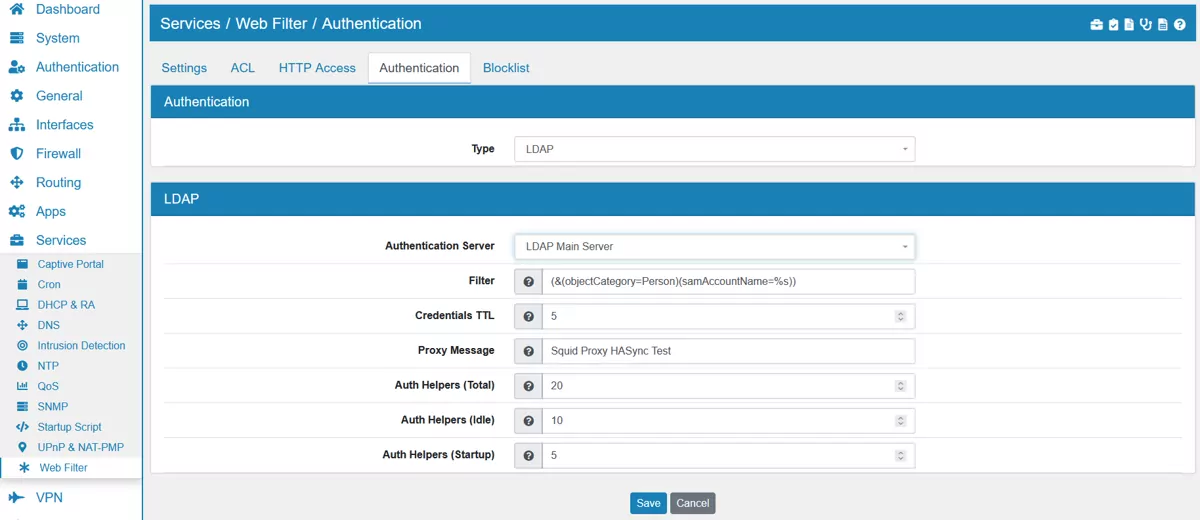
Here you can setup an additional authentication method. You can choose between LDAP and Active Directory.
17.17.4.1. LDAP¶
Authentication Server can be selected from the authentiation servers you created in the VT AIR.
Filter is an LDAP search filter to locate the user DN. Required if the users are in a hierarchy below the base DN, or if the login name is not what builds the user specific part of the users DN. It is (&(objectCategory=Person)(samAccountName=%s)) by default.
Credentials TTL is the time in minutes after credentials will be rechecked. Default value is 5.
Proxy Message is the proxy authentication informational message for your proxy users. Default is Squid Proxy.
Auth Helpers (Total) is the total number of authentication helpers to run. It is recommended to set it equal to the approximate number of proxy users in the network. Default value is 20.
Auth Helpers (Idle) is the idle number of authentication helpers to run. It is recommended to make it equal to about half of the total number of users in the network. Default value is 10.
Auth Helpers (Startup) is the number of authentication helpers to run at startup. It is recommended to make it equal to about a quarter of the total number of users in the network. Default value is 5.
In order to enforce the authentication, you need to create a HTTP Access rule that includes the predefined ACL proxy_auth REQUIRED.
17.17.4.2. Active Directory¶
Domain name short is the first part of the domain name.
Domain name long is the full domain name.
Authentication Processes is the number of authentication processes. It is recommended to make it equal to about a quarter of the total number of users in the network. Default value is 10.
17.17.5. Blocklist¶
Allows you to use the UT1 blocklist by selecting several categories.
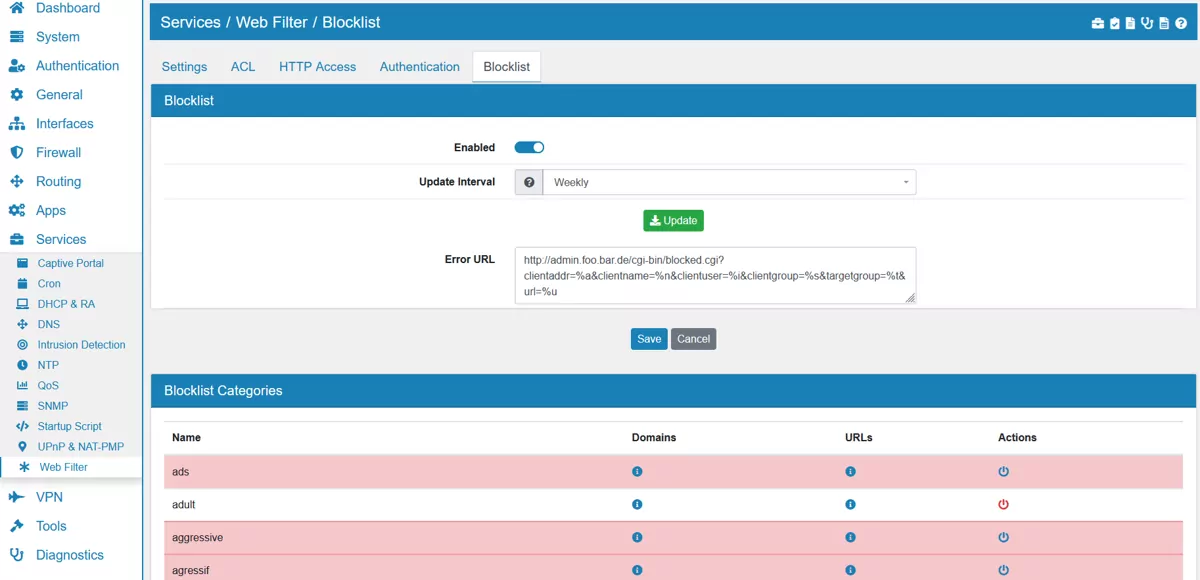
Enabled enable or disable the blocklists.
Update Interval specifies how often the blocklist definition should be updated.
Error URL can be defined and is http://admin.foo.bar.de/cgi-bin/blocked.cgi?clientaddr=%a&clientname=%n&clientuser=%i&clientgroup=%s&targetgroup=%t&url=%u by default. An error URL NEEDS to be defined or no blocking will happen.
Blocklist Categories can be enabled or disabled. By default adult, cryptojacking, ddos and malware are enabled. The Domains and URLs of each category can be displayed by clicking on the information button.
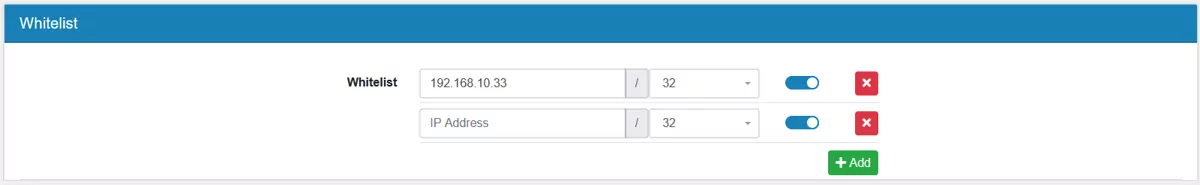
Multiple Whitelists can be added with their ip address and netmask.
17.17.6. Example Proxy Configuration¶
Web Filter can be configured as a Proxy in your network. This means that traffic from inside your network can be analyzed before leaving towards the internet and web content entering your network can be cached. This is useful for blocking access to specific services that are unwanted but not necessarily malicious (which is a task for Intrusion Detection Intrusion Detection) and to save on bandwidth when browsing the internet with multiple clients in your local network.
A typical configuration is shown here. Go to Services → Web Filter and enable the package. Typically you’d want your local network (e.g. LAN) selected as the Interface.
Transparent Proxy
Top configure your Web Filter as a transparent proxy that caches web traffic for your local network, enable HTTP and HTTPS as well as the Transparent Proxy option on both.
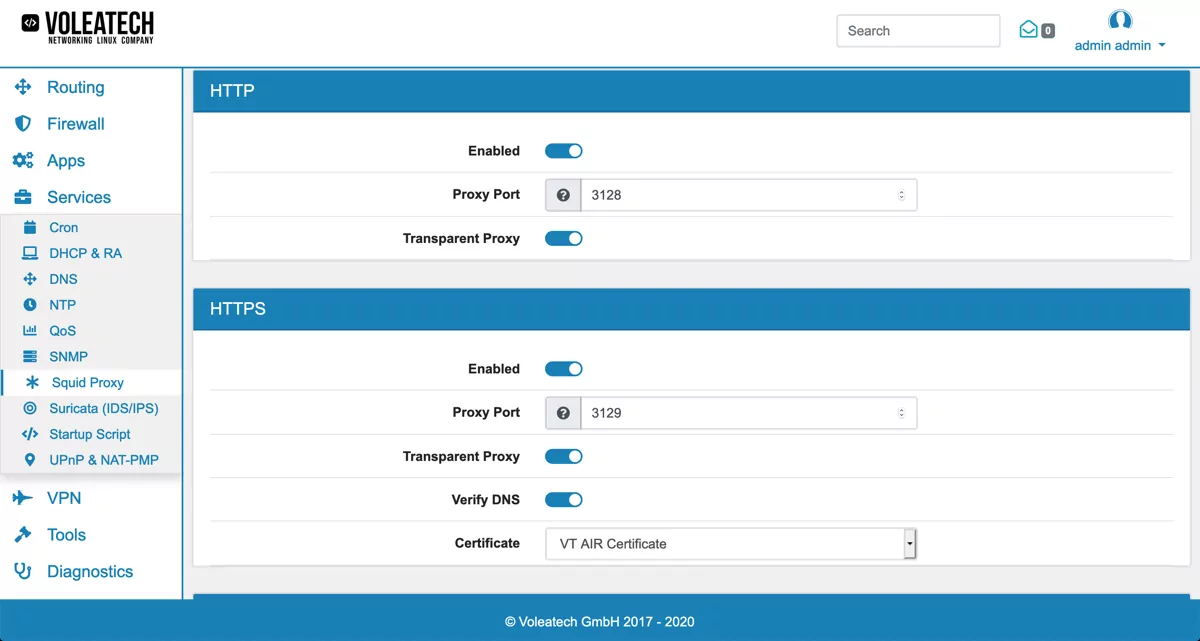
Be aware that the HTTPS transparent proxy can not look inside encrypted traffic. Only the certificate and hostname are visible to make decisions.
Proxy with anti-virus
Then Enable ClamAV Anti-Virus and choose an update interval. The anti virus can only inspect unencrypted traffic. For HTTPS transparent proxy no virus scan can be performed.
Blocklists
Enable Blocklist and choose an update interval to pull in the predefined blocklists.
To configure your blocklist settings go to Services → Web Filter → ACL. Here you can find an overview of all the blocklisting categories that are available. Go to Services → Web Filter → HTTP Access to create the filtering rules.
Click Add or Edit to create or edit the blocklist rule. Set Action to Deny, Logical Operator to OR and add all the blocklist categories that you want to block under ACL.