17.19. Web Application Firewall¶
You can find the Web Application Firewall Settings at Services → Web Application FW.
The Web Application Firewall (WAF) is a specific form of application firewall that filters, monitors, and blocks HTTP traffic to and from a web service.
Before you can use the Web Application Firewall it has to be installed. You can install it at System → Addons.
You can export the settings in the top right corner as an Excel spreadsheet.
The Web Application Firewall is integrated into HAProxy and requires you to configure HAProxy accordingly. The Web Application Firewall needs to be able to read the entire web traffic without encryption. HAProxy might need to be configured for SSL Offloading for that purpose.
17.19.1. OWASP Core Ruleset¶
The VT AIR Web Application Firewall uses the OWASP ModSecurity Core Rule Set.
The OWASP Core Ruleset is designed to work as a single entity to calculate a threat score and execute an action based on that score. When a rule in the ruleset matches a request, the threat score increases according to the rule score. If the final threat score is greater than the configured score threshold, WAF executes the action configured in the last rule of the ruleset.
17.19.2. Settings¶
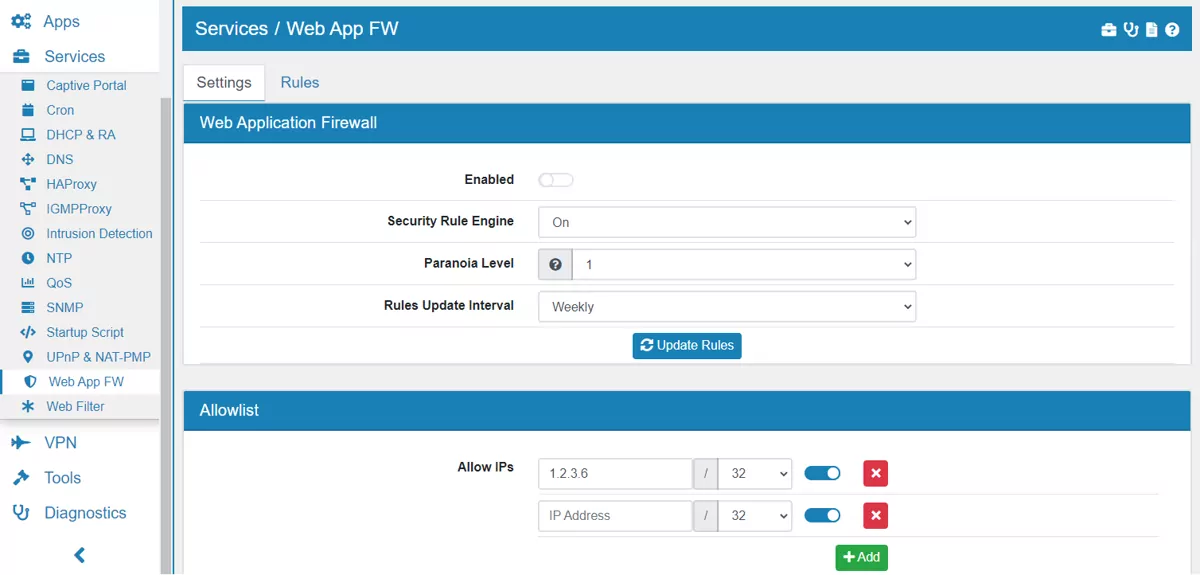
Here the Web Application Firewall can be enabled or disabled.
The Security Rule Engine can be On, Off or DetectionOnly.
The Paranoia Level is defined as a number between 1 and 4. With a higher paranoia level additional rules are enabled and the level of security increases. However, higher paranoia levels also increase the possibility of blocking some legitimate traffic due to false alarms. Default is 1.
Rules Update Interval is a cronjob which will update the rules according to the selected time interval.
17.19.3. Allowlist¶
Multiple Allow IPs can be added with their ip address and port. The IPs will not be checked by the WAF.
Multiple Allow URIs can be added with their URI. The URIs will not be checked by the WAF.
17.19.4. Plugins¶
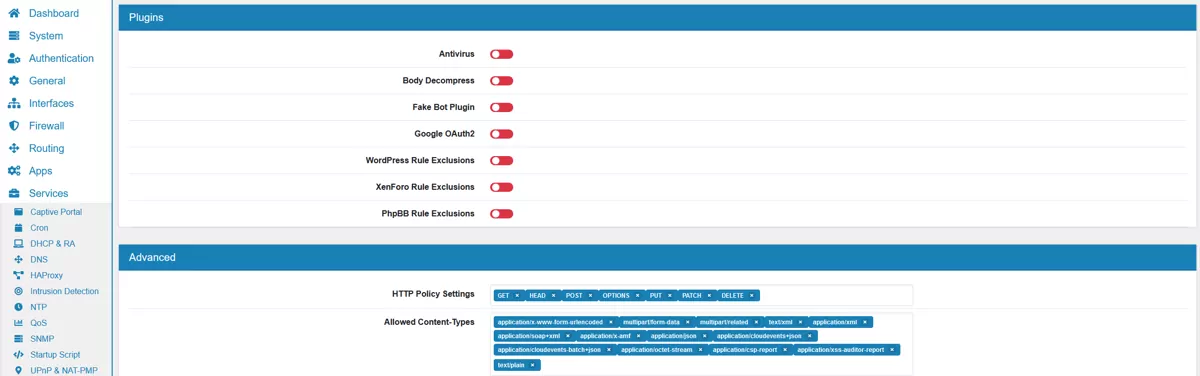
Here you can enable the following WAF plugins:
Antivirus
Body Decompress
Fake Bot Plugin
Google OAuth2
WordPress Rule Exclusions
XenForo Rule Exclusions
PhpBB Rule Exclusions
If you use any if the applications it is advisable to enable the plugin. The plugins will enable special rules and exceptions for the Application for extra protection or to avoid false positives.
17.19.5. Advanced¶
HTTP Policy Settings and default is GET, HEAD, POST, OPTIONS, PUT, PATCH and DELETE.
Allowed Content-Types are the Content-Types that a client is allowed to send in a request. Default is application/x-www-form-urlencoded, multipart/form-data, multipart/related, text/xml, application/xml, application/soap+xml, application/x-amf, application/json, application/cloudevents+json, application/cloudevents-batch+json, application/octet-stream, application/csp-report, application/xss-auditor-report and text/plain.
Allowed HTTP versions and default is HTTP/1.0, HTTP/1.1, HTTP/2 and HTTP/2.0.
Forbidden file extensions and default is asa, asax, ascx, axd, backup, bak, bat, cdx, cer, cfg, cmd, com, config, conf, cs, csproj, csr, dat, db, dbf, dll, dos, htr, htw, ida, idc, idq, inc, ini, key, licx, lnk, log, mdb, old, pass, pdb, pol, printer, pwd, rdb, resources, resx, sql, swp, sys, vb, vbs, vbproj, vsdisco, webinfo, xsd and xsx.
Forbidden request headers and default is proxy, lock-token, content-range, if and user-agentt.
File extensions considered static files and default is jpg, jpeg, png, gif, js, css, ico, svg and webp.
Allowed Charsets are the Content-Types charsets that a client is allowed to send in a request. Default is utf-8, iso-8859-1, iso-8859-15 and windows-1252.
At the bottom you can add Custom Rules.
17.19.6. Rules¶
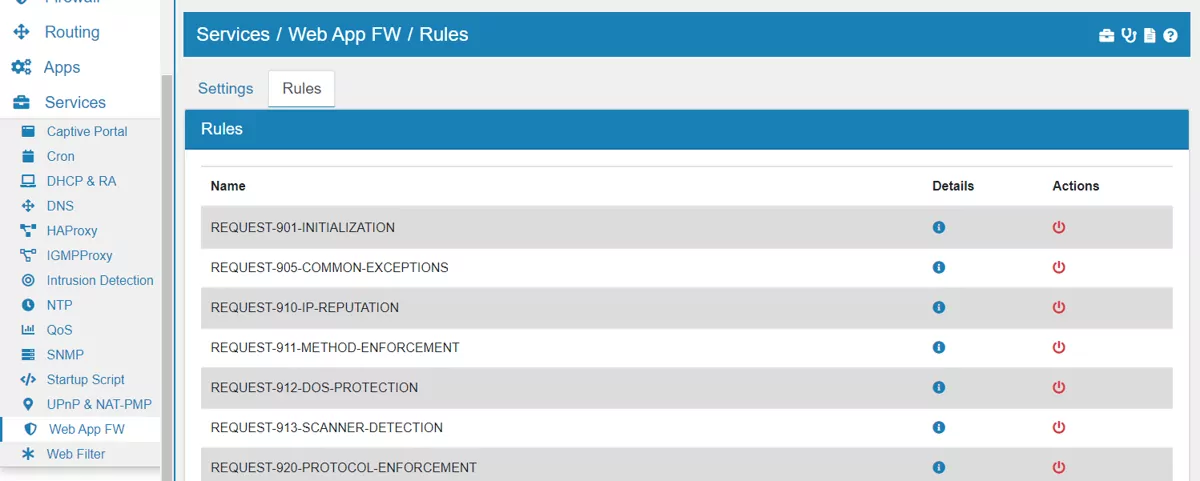
Here you can see all installed and used rule files. Each rule file can be disabled and enabled on the actions column on the right side. You can also click on the detail icon of each rule to see the specific definion of it.
Multiple Remove Rules can be added to disable specific rules by their Rule ID.