17.8. HAProxy¶
You can find the HAProxy Settings at Services → HAProxy.
The HAProxy is a high availability load balancer and proxy server for TCP and HTTP.
Before you can use the HAProxy it has to be installed. You can install it at System → Addons.
17.8.1. General Settings¶
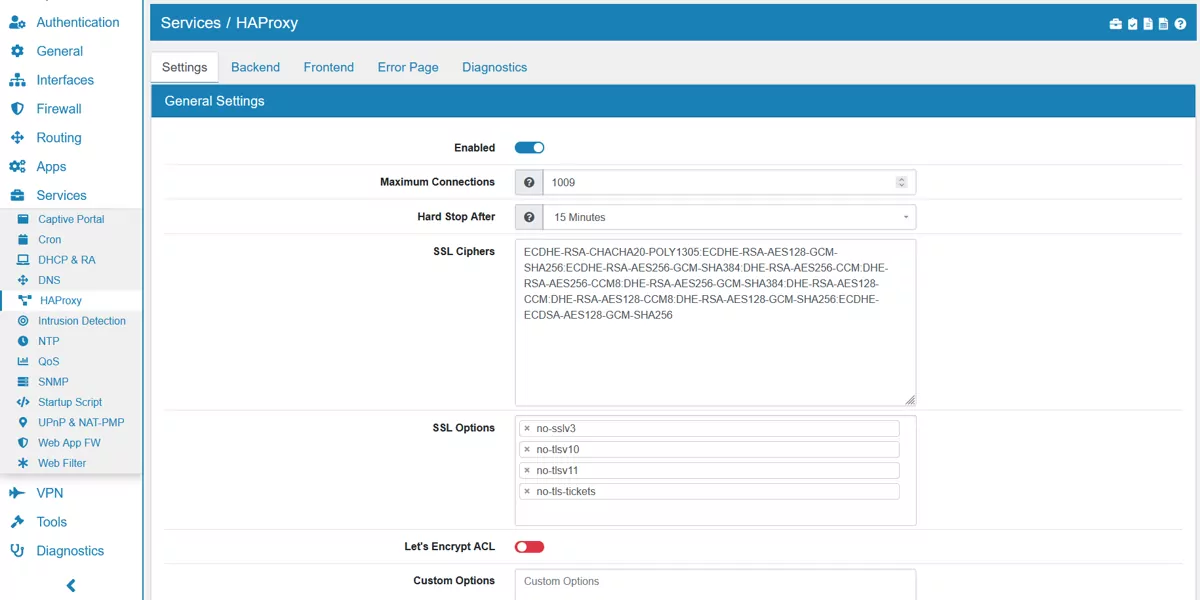
On the page the HAProxy can be enabled or disabled.
The Maximum Connections can be configured and is 1000 by default.
Hard Stop After defines the maximum time allowed to perform a clean soft-stop. This may be used to ensure that the instance will quit even if connections remain opened during a soft-stop.
SSL Ciphers is a list of ssl chiphers seperated by colons.
SSL Options can be a selection of no-sslv3, no-tlsv10, no-tlsv11, no-tls-tickets, no-tlsv12 and no-tlsv13.
Let’s Encrypt ACL will redirect all letsencrypt requests to the VT AIR firewall for renewal of certificates. Use this option if VT AIR itself is renewing the certificates in the web mode.
Custom Options can be used for custom configuration parameters for the config.
HAProxy will automatically be started with one thread per CPU core to load balance connections.
You can export the settings in the top right corner as an Excel spreadsheet.
17.8.2. Backend¶
A backend is a server behind the firewall that HAProxy should send data to. Data are received on the Frontend, are processed and forwarded to a backend.
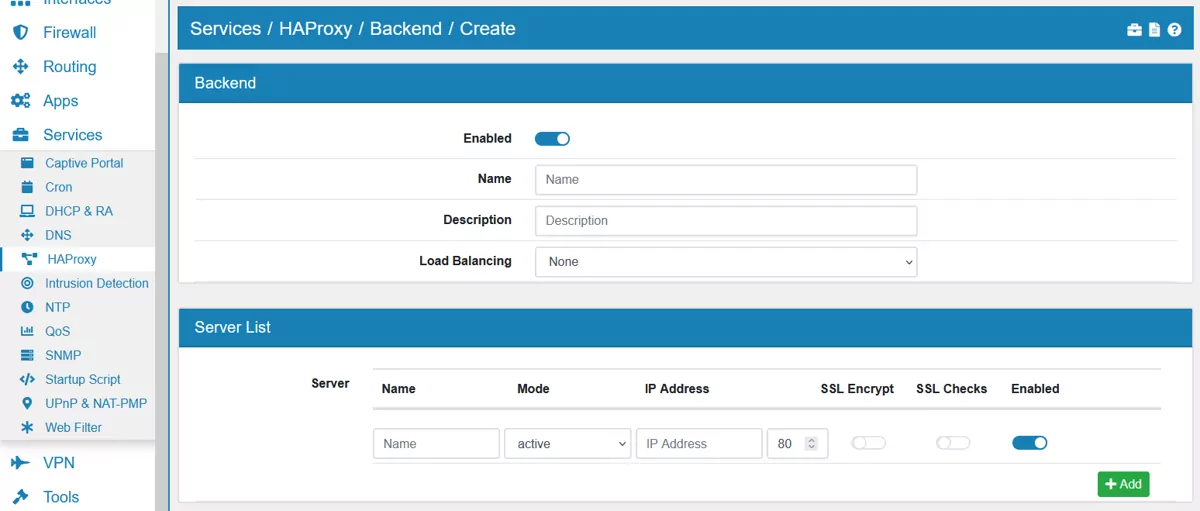
Each Backend has a Name, Description and can be enabled or disabled. You can add multiple Servers, each with a name, mode, IP address, port and ssl encrypt and ssl checks to each backend in case you want to load balance them.
SSL Encrypt enables SSL deciphering on connections instantiated from this listener.
SSL Checks forces encryption of all health checks over SSL, regardless of whether the server uses SSL or not for the normal traffic.
Load Balancing can be Round Robin, Static Round Robin, Least Connections or Source.
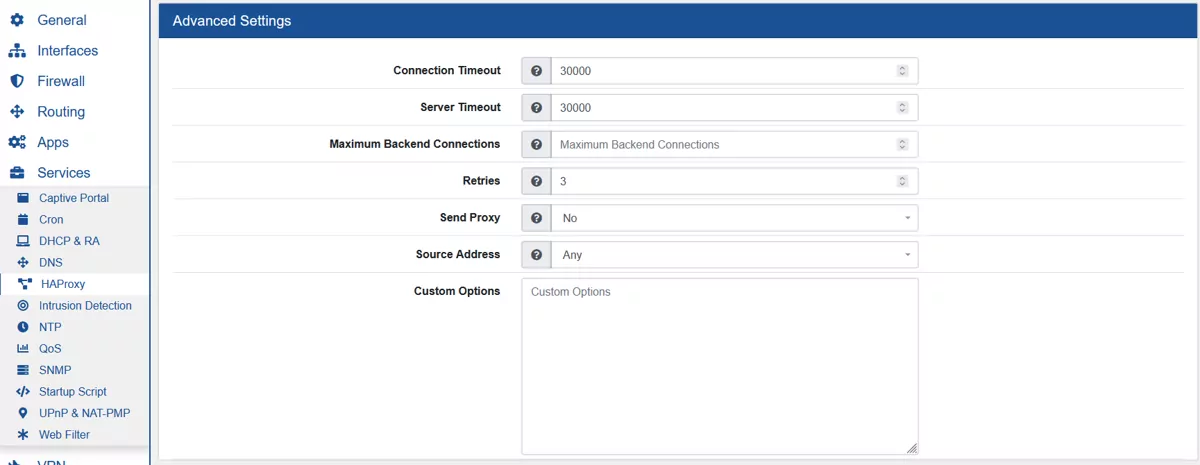
Connection Timeout is the maximum time (in milliseconds) to wait for a connection attempt to a server to succeed. The default value is 30000.
Server Timeout is the maximum inactivity time (in milliseconds) on the server side. The default value is 30000.
Maximum Backend Connections is the maximum amount of connections that all backends should process. If no value is specified the value is computed by the global Maximum Connection value.
Retries are the number of times a connection attempt should be retried on a server when a connection either is refused or times out. The default value is 3.
Send Proxy if the proxy protocol should be used to connect to the backend and if so which version.
Source Address in order to change the source of the connection from HAProxy to the firewall. This might be useful in HA Setups to use the virtual ip as sender.
WAF Error Page File is a Custom Error Page if WAF is activated and access is blocked for this backend. Has to be a HTML file.
Custom Options can be used for custom configuration parameters for the config.
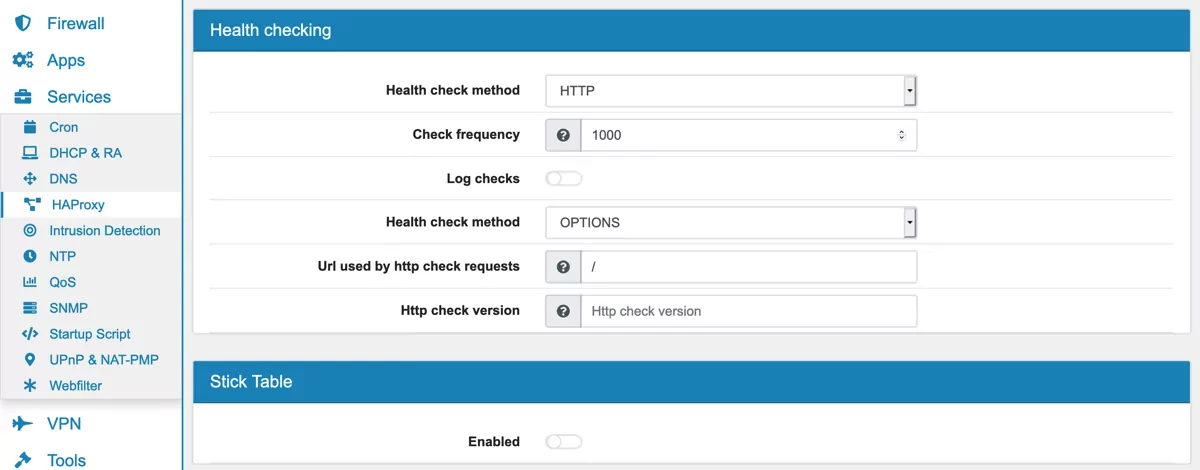
Health check method can be None, Basic, HTTP, SMTP or LDAP.
Check frequency is the check frequency in milliseconds. The default value is 1000.
When Log checks is enabled, any change of the health check status or to the server’s health will be logged.
Health check method can be OPTIONS, HEAD, GET, POST, PUT, DELETE or TRACE.
Url used by http check requests defaults to / if left blank.
Http check version defaults to “HTTP/1.0” if left blank.
Stick Table can be enabled.
Type is the stick table type.
Size is the stick table size in MB. The default value is 1 MB.
Expire is the stick table expire time in seconds. The default value is 10 seconds.
17.8.3. Frontend¶
Frontend is the service where HAproxy is listening for connections to process. A frontend is listening on an IP Address and port pair.
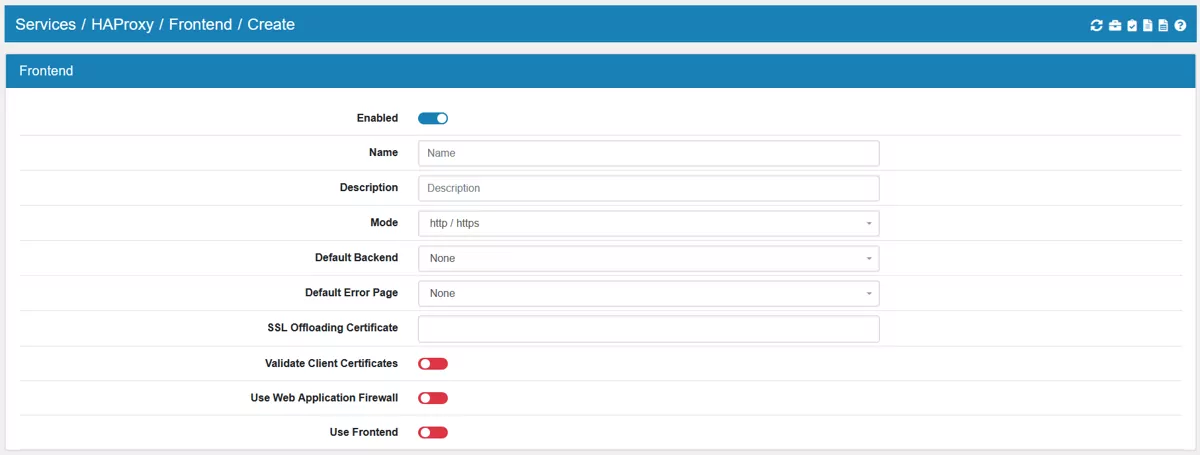
Each Frontend has a Name, Description and can be enabled or disabled.
A Frontend can either be standalone or connected to another frontend. In the case of a connected frontend, only the acl and actions will be available and all other settings are merged from the connected frontend.
A frontend can have multiple addresses with an IP address and port. You can also add multiple ACLs with a description, expression, backend and value. The value can be negated and checked for case-sensitivity.
Mode can be http / https, ssl / https (TCP mode) or tcp.
Default Backend is the default connection to a backend when no specific one is chosen in a following option.
Default Error Page is the default error page. Is has to be created in the system beforehand.
SSL Offloading Certificate allows you to SSL Offload connections. HAProxy can have more than one certificate and they are chosen based on CName and the request that is coming in. To enable SSL Offloading the IPAddress and port have to be explicilty set to enabled even when certificates are selected here. Only HTTP connections can be offloaded and not TCP or TLS connections.
Validate Client Certificates can be enabled. If enabled, you also need to choose a Certificate Authority. This is only possible on http / https and tcp mode with SSL Offloading enabled for external addresses. Client Certificate Verification will also be configurable and can be either Required or Optional.
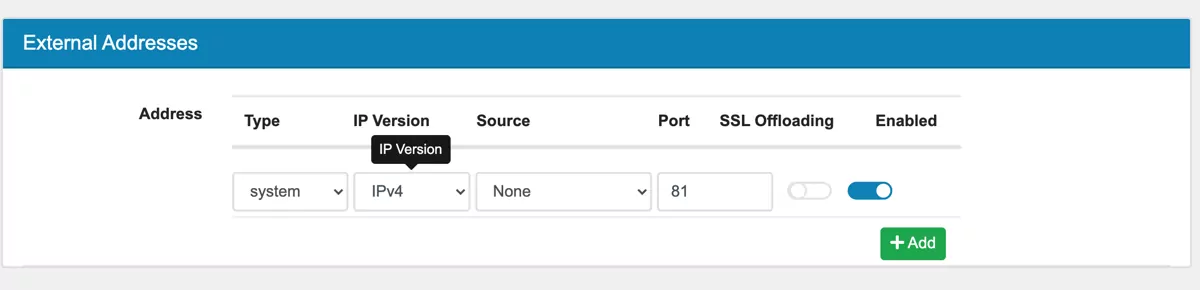
Each Frontend can listen on one ore more IPAddresses and ports. You need to set the type (IPv4 or IPv6) and which address to use. System addresses are Network Objects from the Firewall. You can enable SSL Offloading for each Pair.
In order to use the Web Application Firewall on encrypted connections you can enable the SSL Offloading to transparently encrypt traffic to the user but still give access to the WAF.
Use Web Application Firewall enables the web application firewall for this frontend. The traffic will be inspected by the WAF and if a threat is detected it will be blocked with a 404 error.
Use Frontend lets you select and use another HAProxy Frontend. In order to make managing different Frontends easier, you can connect one Frontend to another Frontend. All settings except ACLs and Actions are shared between the Frontends. The Frontends are merged together in the configuration to display one unified Frontend. Different use cases make it more user friendly to seperate the Frontends in the GUI like multiple complex Backends or separating by Customer.
17.8.3.1. Advanced¶
Advanced allows to set some settings for the entire frontend.
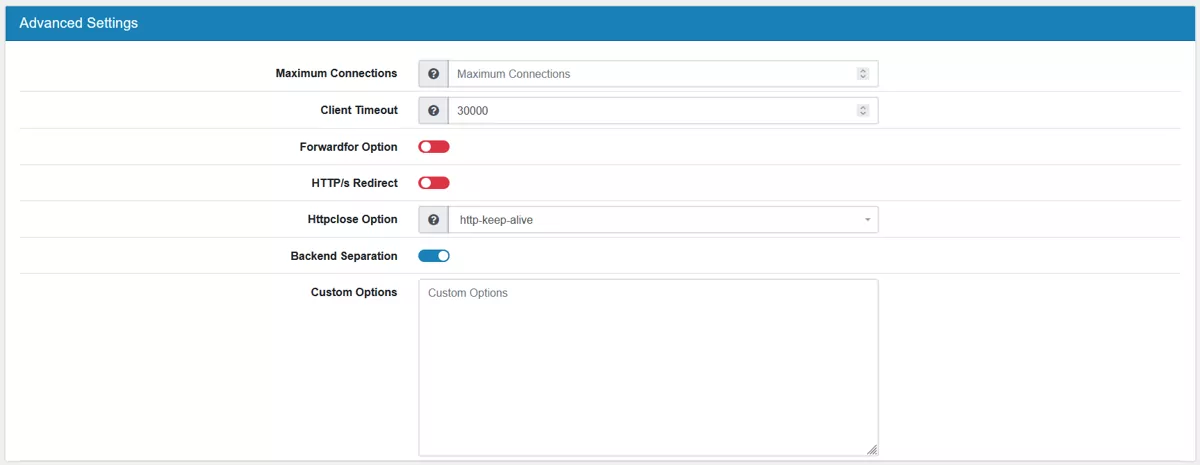
Maximum Connections limit the sockets to this number of concurrent connections.
Client Timeout is the maximum inactivity time (in milliseconds) on the client side. The default value is 30000.
Forwardfor Option enables the insertion of the X-Forwarded-For header to requests sent to servers.
HTTP/s Redirect can be enabled.
Httpclose Option enables passive HTTP connection closing.
Backend Separation If we have an ACL with host matches, use a copy of the backend for each action and run the backend health check with this host name. This allows only this host to be not available in case of problems especially when a backend is hosting multiple homepages under different hostnames.
Custom Options can be used for custom configuration parameters for the config.
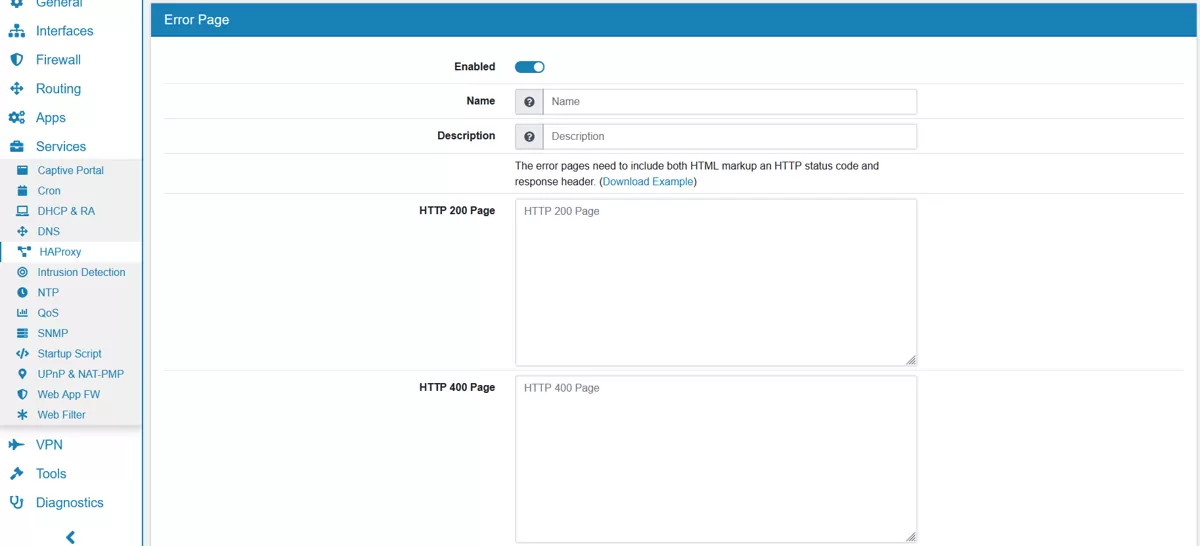
17.8.4. Error Pages¶
Error Pages with custom error pages can be configured and linked to actions and acls. The following HTTP codes are supported: 200, 400, 401, 403, 404, 405, 407, 408, 410, 425, 429, 500, 502, 503 and 504. An example file can be downloaded from the GUI. The error pages need to include both HTML markup an HTTP status code and response header.
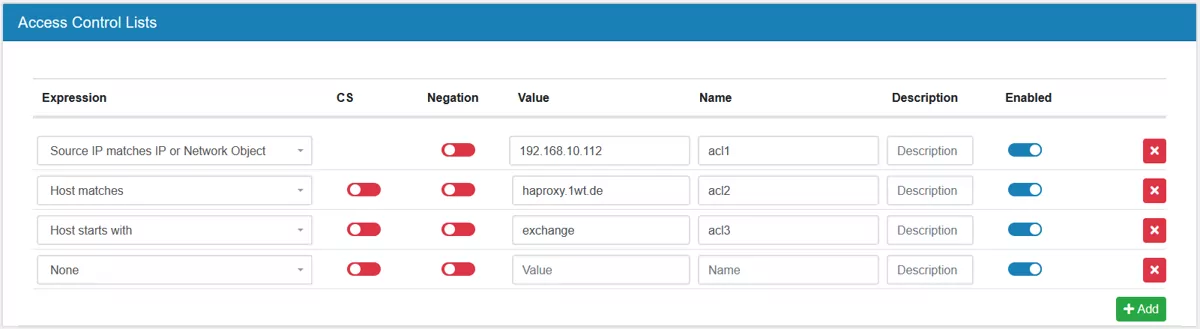
17.8.5. Access Control Lists¶
Access Control Lists are rules to match against which can be used in Frontends and Backends. In the Frontend they depend on the mode and include host names and source ips. Each ACL needs a unique name for the frontend so it can be used in the actions assignment.
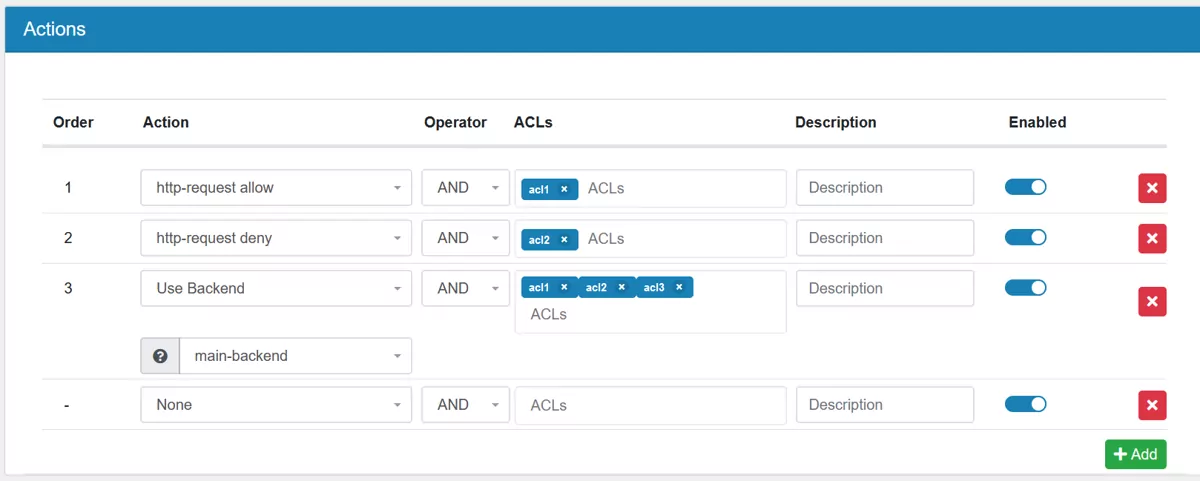
17.8.6. Actions¶
Actions can be linked to one or many ACLs. Multiple ACLs can be AND/OR together to get a flexible assignment. Frontend and Backend Actions have different specific actions to choose from.
A Error Page can be assigend to a Frontend Action or set as Default Error Page in a Frontend. They have to be created in the system beforehand.
A Error Page Backend Down can be assigend to a Frontend Action. It will be used, if the selected backend is down.
17.8.7. General¶
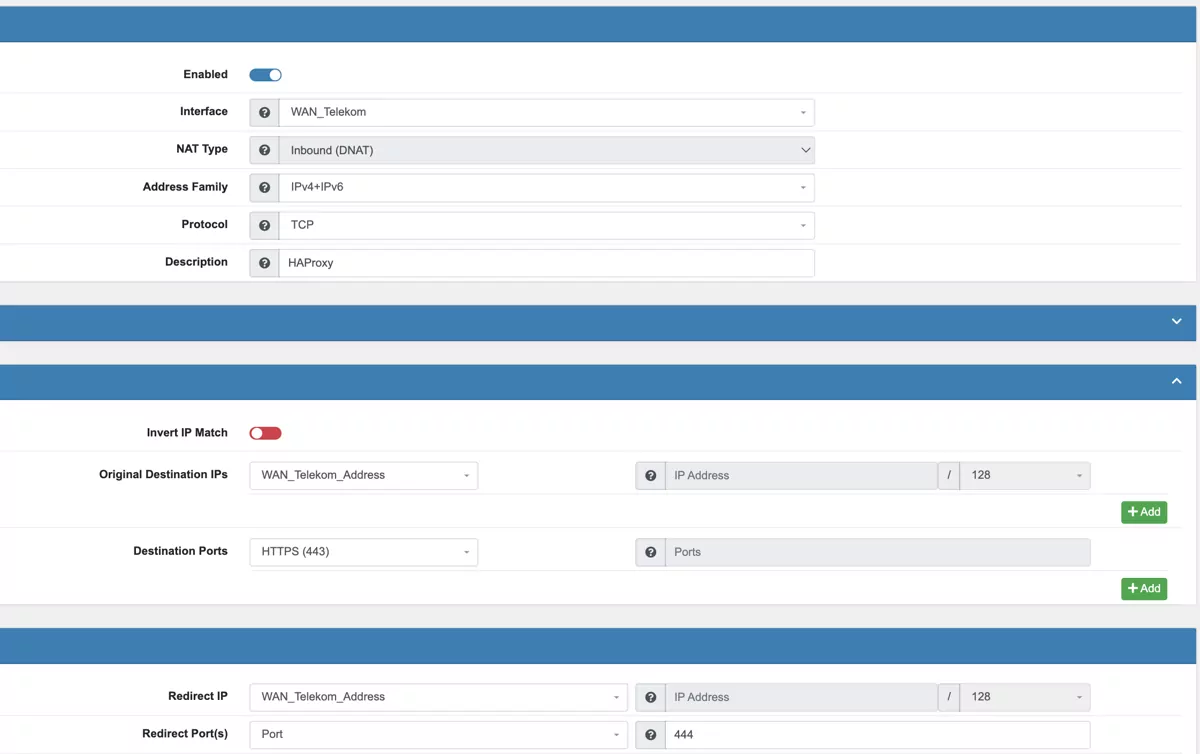
Please be aware that port 443 and port 80 are occupied by Nginx. If you want to use them for HAProxy, please use DNAT on the interfaces to a different Port that the Frontend of HAProxy is using.
You can simply redirect the port 443 and 80 from WAN to HAProxy. HAProxy needs to run on a different port, for example 444 and 81.
An example for the DNAT rule can be found in the following image.