17.7. DNS¶
You can find the DNS Settings at Services → DNS.
The Domain Name System is mainly used to translate more readable domain names to their numerical IP addresses.
17.7.1. General Settings¶
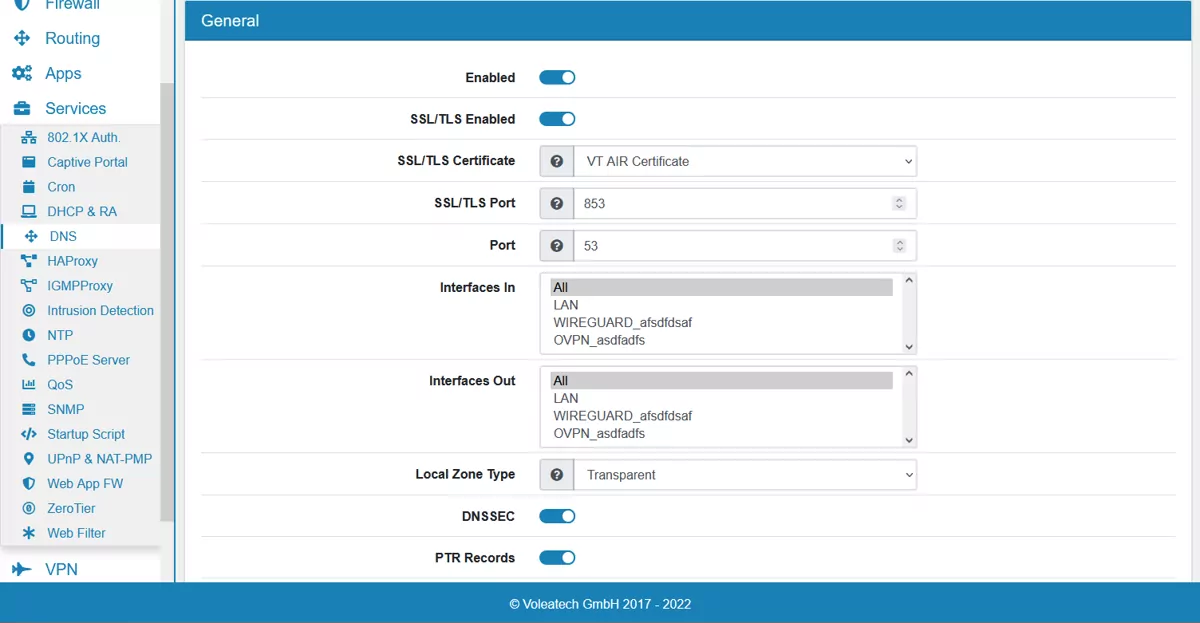
On the page the DNS server can be enabled or disabled. SSL/TLS is enabled by default and the VT AIR Certificate with port 853 is used. You can change Interfaces In and Interfaces Out and on which Port DNS runs on. The Local Zone Type can be configured and is on Transparent by default. The option DNSSEC controls the Domain Name System Security Extensions and if PTR Records is enabled, PTR Records for Host Overrides get added automatically. DHCP Registration will register the DHCP leases in the DNS server, while Static DHCP Registration will register the DHCP Host Reservations in the DNS server.
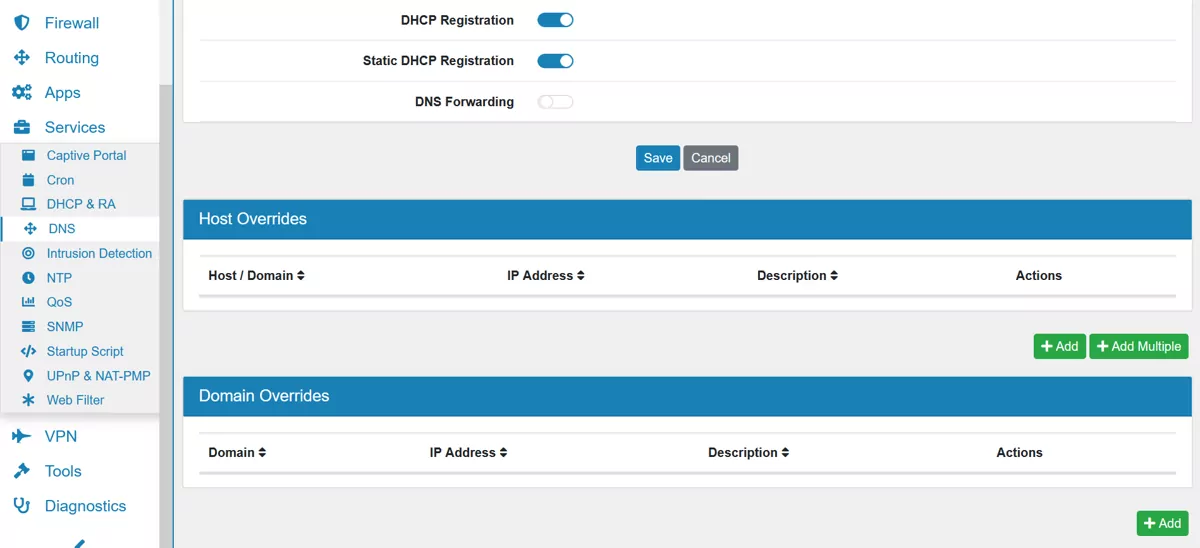
By default the DNS Server queries the DNS Root servers and is not forwarding traffic to other servers. If DNS Forward is enabled, you can add multiple DNS Forward Servers with an IP address for each and those are used instead of the Root Servers.
You can export the settings in the top right corner as an Excel spreadsheet.
17.7.2. Advanced Settings¶
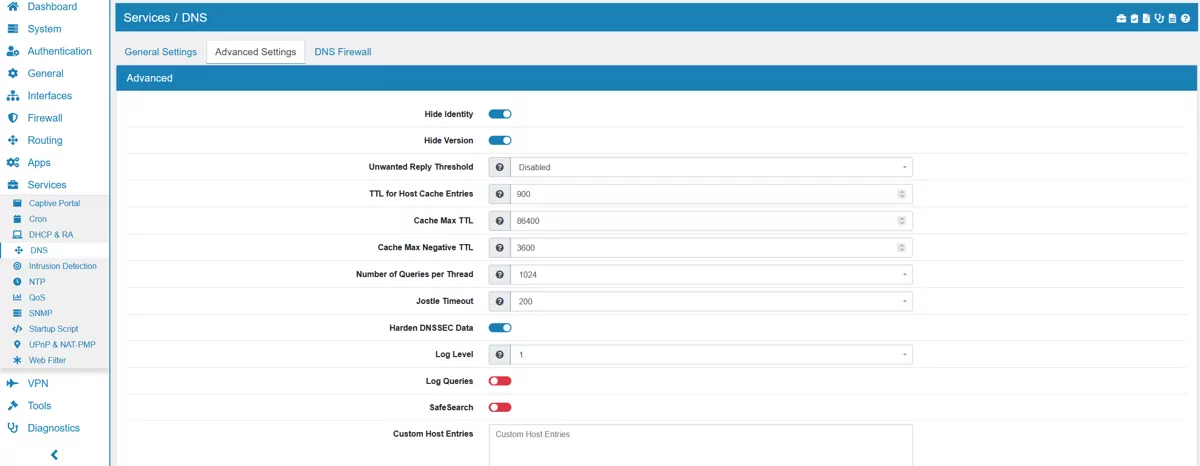
Hide Identity if enabled id.server and hostname.bind queries are refused.
Hide Version if enabled version.server and version.bind queries are refused.
Unwanted Reply Threshold if set, a total number of unwanted replies is kept track of in every thread. When it reaches the threshold, a defensive action is taken and a warning is printed to the log.
TTL for Host Cache Entries time to live for entries in the host cache. The host cache contains roundtrip timing, lameness and EDNS support information. It is 900 by default.
Cache Max TTL time to live maximum for RRsets and messages in the cache. When the TTL expires, the cache item has expired. It is 86400 by default.
Cache Max Negative TTL time to live maximum for negative responses, these have a SOA in the authority section that is limited in time. It is 3600 by default.
Number of Queries per Thread the number of queries that every thread will service simultaneously. It is 1024 by default.
Jostle Timeout timeout used when the server is very busy. Set to a value that usually results in one roundtrip to the authority servers. It is 200 by default.
Harden DNSSEC Data require DNSSEC data for trust-anchored zones, if such data is absent, the zone becomes bogus.
Log Level the Log verbosity level. It is 1 by default.
SafeSearch enables the SafeSearch functionality. It is disabled by default.
Log Queries logs all queries.
Custom Host Entries for custom host or domainn entries. They will be copied to the configuration directly.
Custom Options custom configuration parameters can be defined here.
Please refer to the Unbound documentation at Unbound.
17.7.3. Host Overrides¶
They allow the configuration of a specific DNS entry for a particular host.
17.7.4. Domain Overrides¶
They allow the configuration of a specific DNS server for a particular domain. If you define a domain multiple times, all DNS server will be used together.
17.7.5. DNS Firewall¶
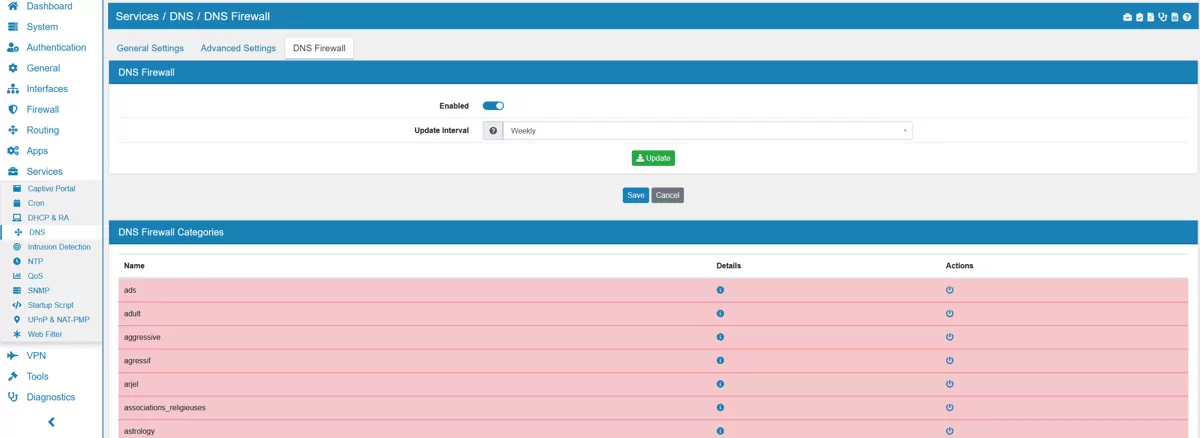
Since most web traffic is encrypted the most effective way to block access to websites is DNS blocklisting. It will send a fake IP back to your client for a domain.
VT AIR uses list of domains in a few categories for you to choose or you can add your own domains and hostnames.
Update Interval is set to weekly by default and can be changed to daily or monthly.
17.7.5.1. Categories¶
Blocklist Categories allow you to block hosts by different categories.
By default, the categories cryptojacking, ddos and malware are enabled. You can enable or disable each category individually.
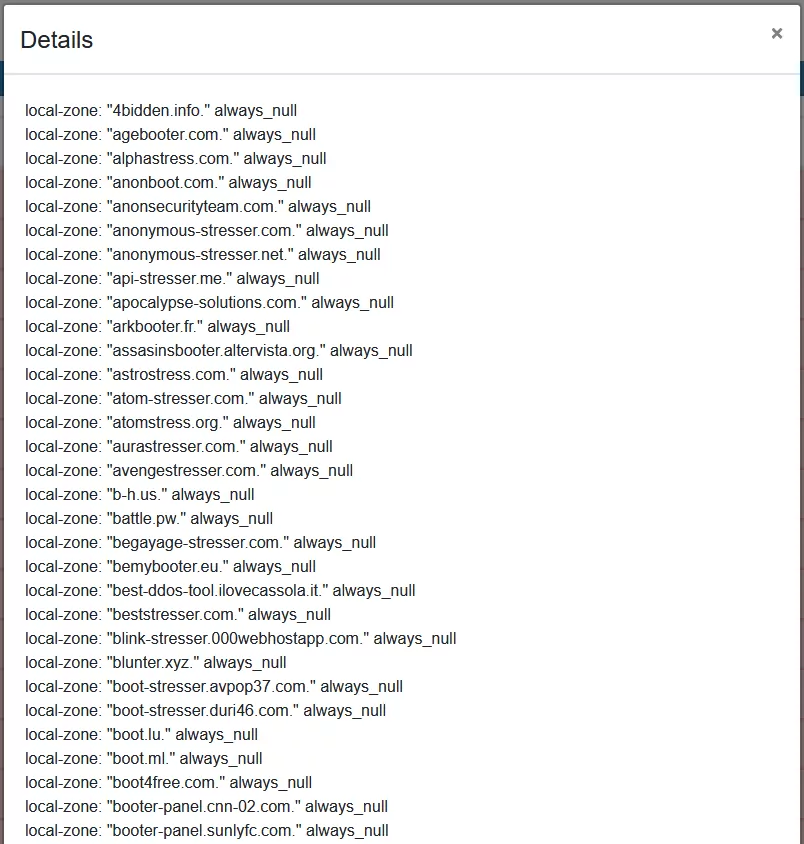
Each categorie has a button which opens a modal with detailed information. All hosts and IPs of that blocklist are listed here.
17.7.5.2. Custom Blocklists¶
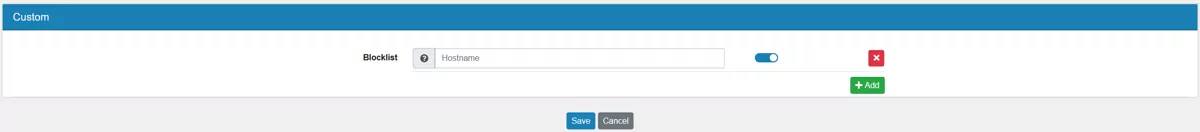
Multiple Custom Blocklist entries can be added with a hostname or domains. Each one can be enabled or disabled, independently from the categories.
All subdomains of the entered domain or hostname will be included in the blocklist.
17.7.6. Redirect DNS Requests¶
You can redirect all DNS requests to your VT AIR device and block other DNS servers (especially outside of your network). To do so go to Firewall → NAT → DNAT and click Add.
Select the Interface of your local network e.g. LAN, TCP/UDP as Protocol and the Address Family you want your rule to be active on.
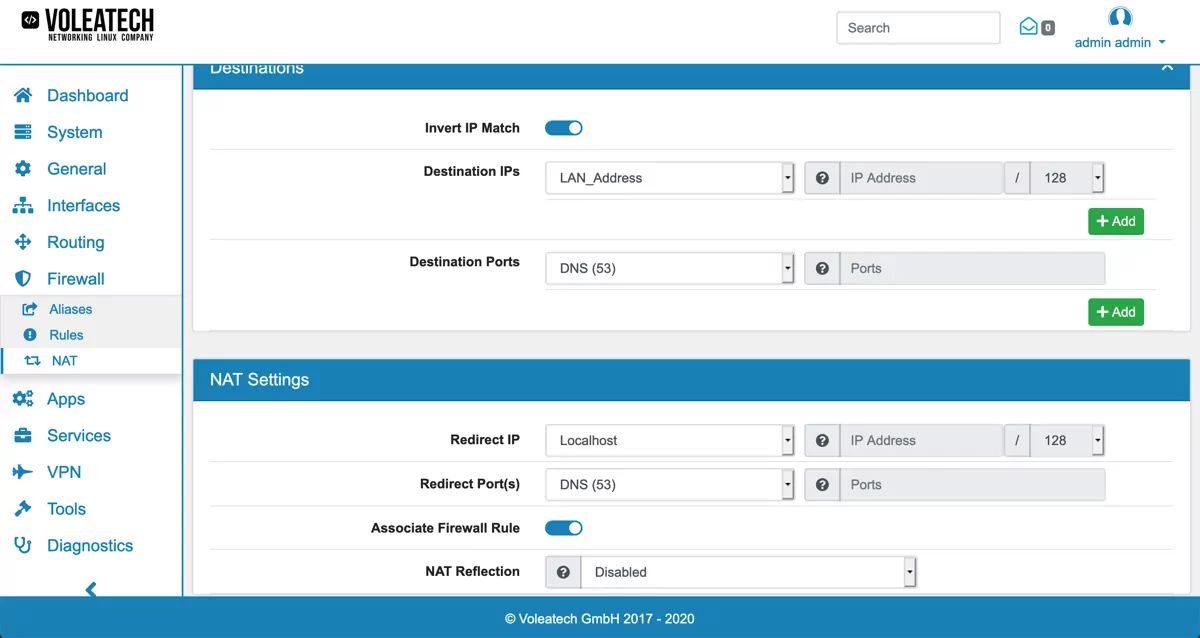
Enable Invert IP Match and select LAN_Address and Port DNS (53) as the Destination. This selects all DNS requests that are not targeted at the local DNS server.
Select Localhost and DNS (53) as the Redirect IP and Port. This redirects all DNS requests to your VT AIR device. Enable Associate Firewall Rule and set NAT Reflection to Disabled.
If you block outside DNS requests you can also effectively use the Blocklist feature described above without configuring each device individually in your network.
17.7.7. Wildcard Domain DNS Entries¶
If you need to create a wildcard DNS entry like *.subdomain.domain.com you can do so in the Custom Host Entries field. The structure is the following, replace the IP with the host that should be returned for all subdomain queries:
Note
local-zone: “subdomain.domain.com.” redirect local-data: “subdomain.domain.com. A 192.168.1.10”
17.7.8. DNS Troubleshooting¶
Note
If you use a forward server that returns private IPs, they will be rejected since the DNS server will see them as a DNS rebind attack. In order to deactivate the check for domains, declare them as private in the Custom Host Entries field with private-domain: “mydomain.ending”.
Note
If you use an internet load balancer, more than one WAN at the same time, you need to provide an upstream DNS server and change the mode to forwarding. Otherwise the DNS request might not be answered correctly and you will see hangs in the DNS requests.