21.25. IPSec¶
You can find the IPSec Diagnostics at Diagnostics → VPN → IPSec.
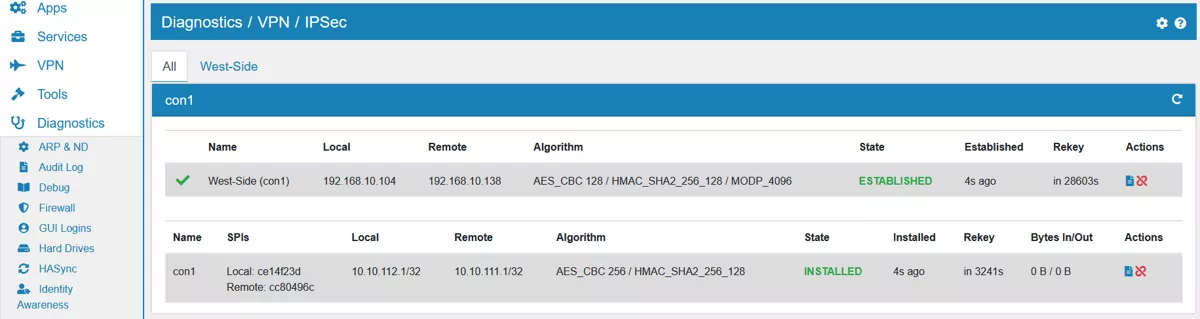
Here you can see connection information about your IPSec setup. There is one All tab with all IPSec setups and each IPSec entry has also its own tab. The connection information is split up into Phase1 and Phase2.
21.25.1. Phase1¶
The first column shows whether the entry is enabled or not.
Local and Remote display their corresponding IP addresses.
Reauth shows, when the next reauthentication is planned.
Algo lists the used encryption algorithms.
Status will be Connected or Disconnected.
At Actions, it’s possible to manually start the connection or disconnect it, depending on the current status. There is also a Log symbol. When clicked, a window opens with detailed log information of the sepecific connection.
21.25.2. Phase2¶
All setup Phase2 will be listed here.
Local and Remote display their corresponding IP addresses.
SPIs shows a Security Parameter Index, which is an identification tag helpul for the kernel.
Rekey shows when a new key is negotiated.
Algo displays the used encryption algorithm. Bytes In/Out show the traffic.
At Actions, it’s possible the manually disconnect the connection. There is also a Log symbol. When clicked, a window opens with detailed log information of the sepecific connection.
To change the IPSec setup please go to VPN → IPSec and refer to the documentation at IPSec Phase 1.
21.25.3. IKEv2¶
There is one important aspect that affects IKEv2. The keys for the CHILD_SA that’s implicitly created with the IKE_AUTH exchange will always be derived from the IKE keys even if PFS is configured. So if the peers disagree on whether to use PFS or not (or on the DH groups) it will not be known until the CHILD_SA is first rekeyed with a CREATE_CHILD_SA exchange (and fails). This is also the reason why you won’t see a DH group in the status of the phase 2 until the SA is first rekeyed.